Security policy setting and determining method, and method and device for executing operation by application program
A technology of security policy and application program, which is applied in the field of communication, can solve the problem of inflexibility in the scheme of assigning security policies, and achieve the effect of improving flexibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
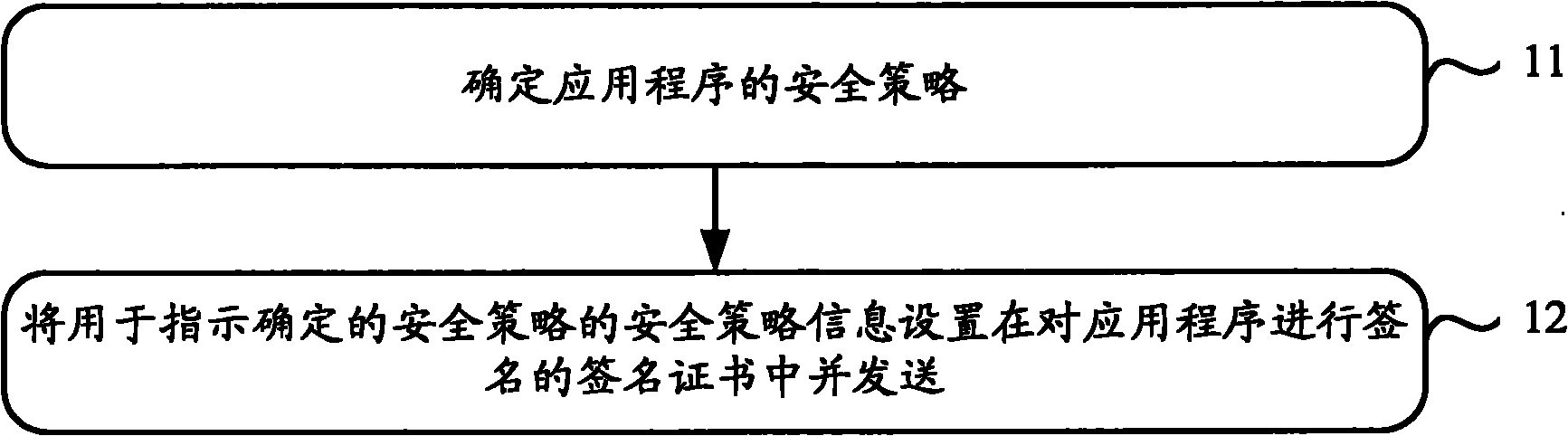
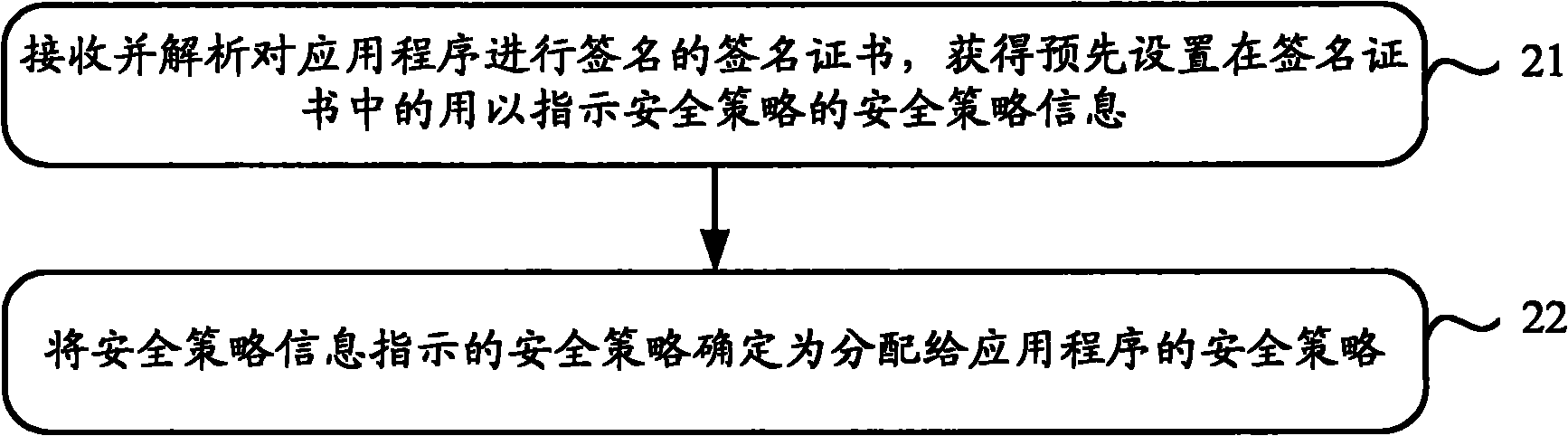
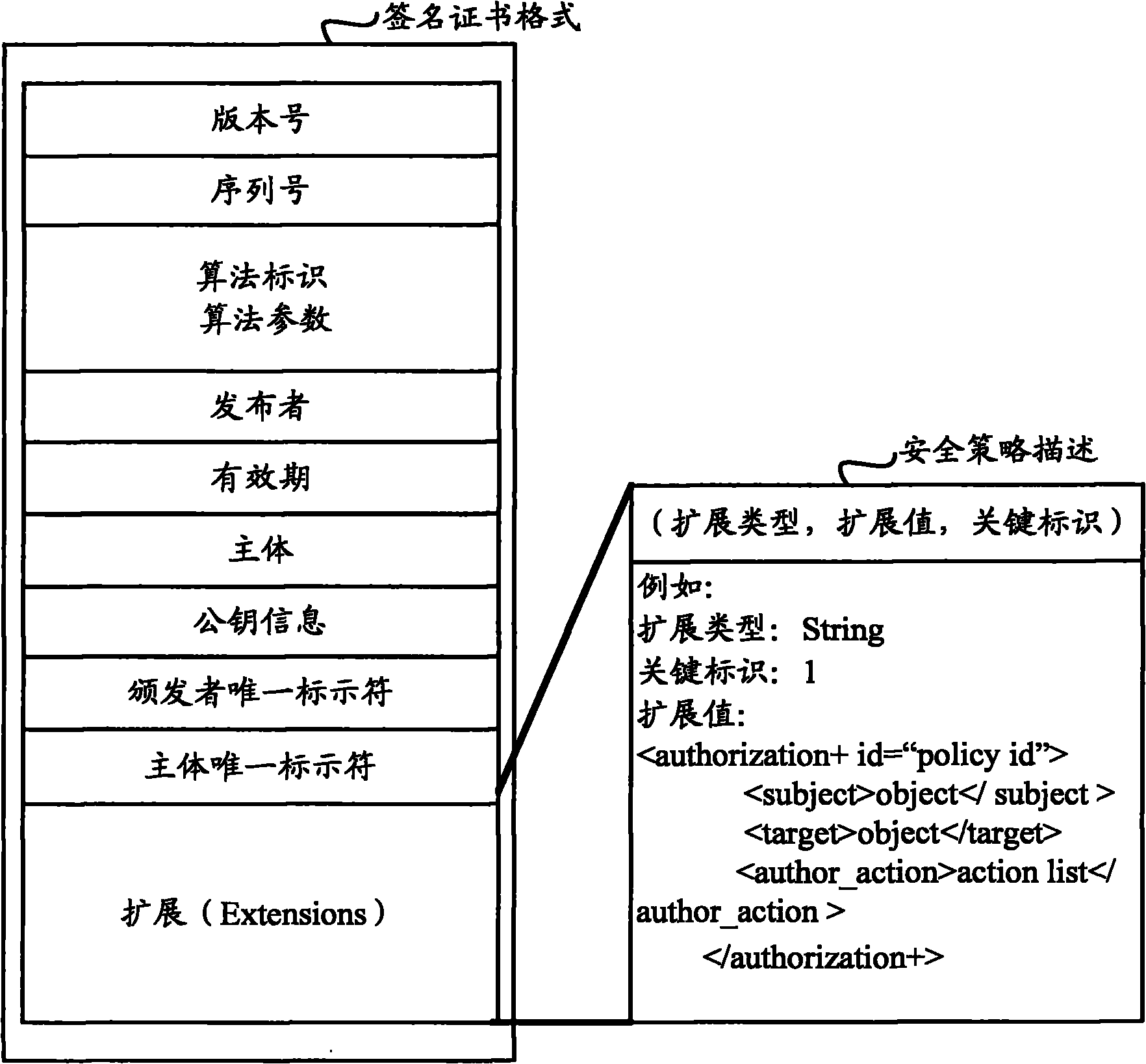
[0029] When the inventor analyzed the security policy allocation scheme provided by the prior art, he found that its shortcomings are mainly reflected in the following two points:
[0030] 1. The static nature of the certificate system. After the application is signed by the signing certificate, a series of security attributes such as its security domain mapping and security permissions are statically determined, and cannot be dynamically configurable and adjustable;
[0031] Second, the singleness and simplification of the security system. When using the security policy allocation scheme provided by the prior art, it is selected from multiple security policies set in advance, so that the application identification will be mapped to a number of fixed security domains, and through the background technology section Analysis shows that these security domains may not reflect all the operations that the application can perform.
[0032] In order to solve the above-mentioned probl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com