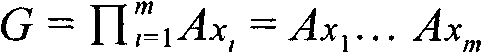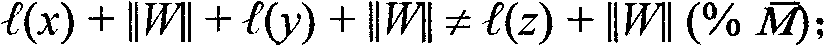Light message abstract extraction method based on new problem
A technology of message summary and extraction method, which is applied in the field of lightweight message summary extraction based on new problems, and can solve problems such as inability to use and restrictions on usage occasions
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0097] The lightweight message digest extraction method based on the non-normative sub-set problem includes two parts, and its characteristic is that it can generate a public initial value, and no intermediate value can be deduced from the initial value, so that the initial value is helpful Due to the strong collision-free nature of message digests. More importantly, the length of the summary output by this method is very short, but at the same time it meets the security requirements.
[0098]Each user can obtain an initial value from the designated CA certificate center. The CA certificate center is an organization that registers and manages users, and generates and distributes initial values. It utilizes an initial value generation method to output a non-mutual prime sequence for message digest extraction.
[0099] This message digest extraction method can be implemented with logic circuit chips or programming languages, and it consists of two parts: ① Develop an initial v...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com