Cloud storage encrypting and deciphering method based on secret key pool
An encryption and decryption algorithm and encryption and decryption technology, applied in the field of Internet distributed cloud storage, can solve the problems of inapplicable encryption and decryption of large files, large amount of calculation, etc., and achieve the effect of improving reliability, ensuring security and privacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
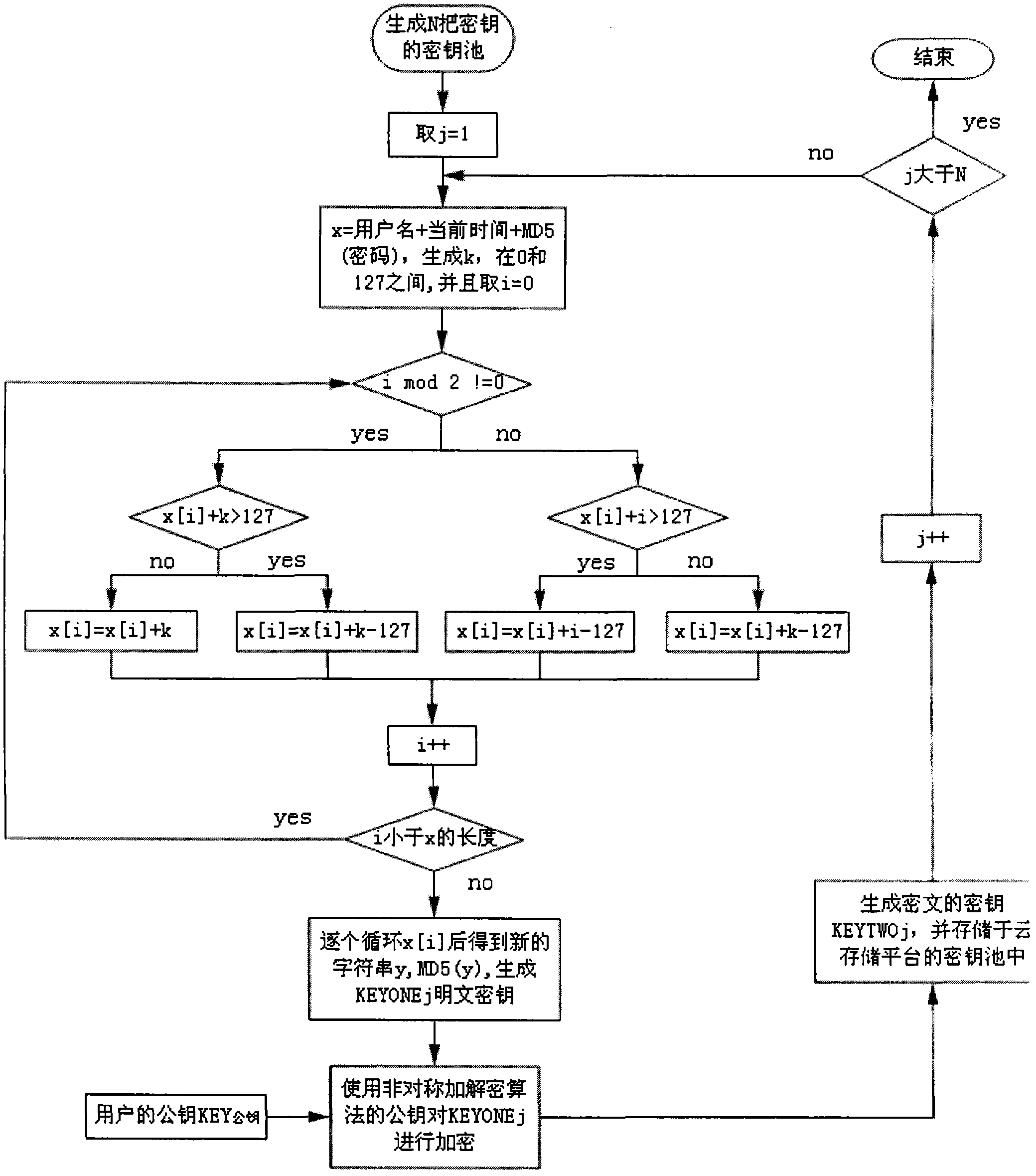
[0028] Embodiment 1, generation of ciphertext key pool
[0029] The key pool generation process reference figure 1 , the specific process of key pool generation is introduced below.
[0030] (1) Take the original string x
[0031] In order to make the generated keys more disorderly and random, the key generation algorithm uses as many random parameters as possible as initial seeds. x = username (registered username) + current time (expressed as year, month, day, hour, minute, second, millisecond) + MD5 code of the user password. And de-symbolize x, that is, remove all non-alphabetic and non-numeric characters in x.
[0032] (2) Set the control factor as k (randomly generated), and k needs to satisfy:
[0033] (2a) is an integer;
[0034] (2b) 0≤k≤127
[0035] (3) Loop for each character x[i] in the string (1≤i≤length(x) is the length of the string x):
[0036] (3a) If the remainder of i modulo 2 is 1, that is, for all odd-numbered characters x[i], perform the following ...
Embodiment 2
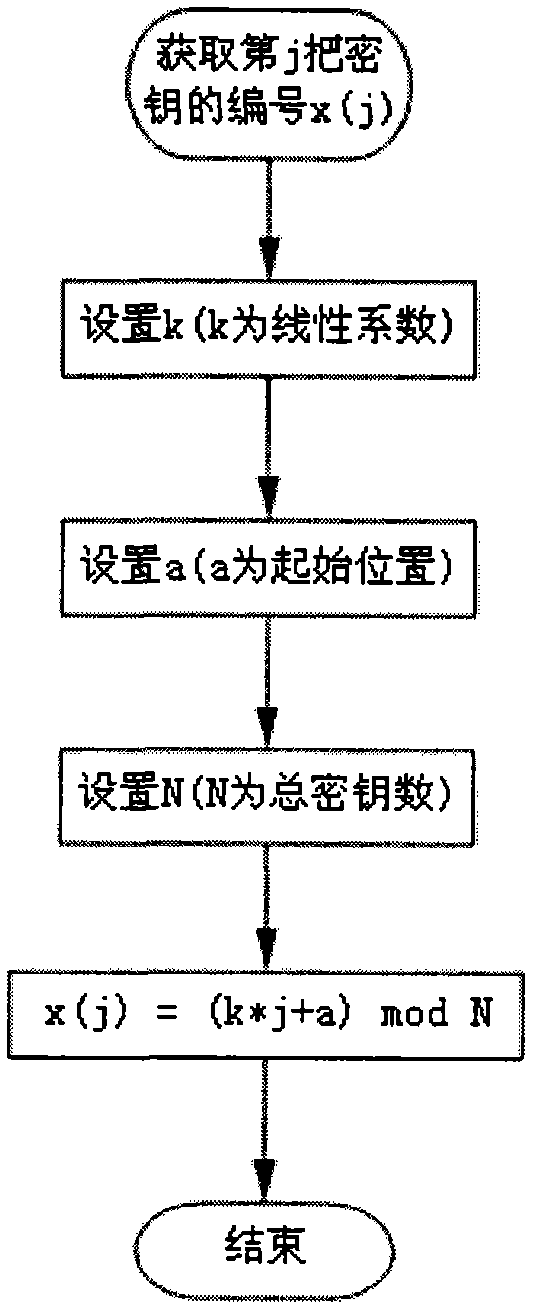
[0049] Embodiment 2, the extraction algorithm of key
[0050] Key extraction algorithm reference figure 2. The key extraction algorithm adopts the linear extraction method, and provides a linear division method to extract the key algorithm (but not limited to this method), the formula is as follows:
[0051] x(j)=(k*j+a) mod N j=1, 2,...
[0052] Where x(j) is the serial number of the jth key, k is the linear step coefficient, a is the starting position, and N is the total number of keys. If k=7, a=66, N=100, the first extracted key number is 73, the second extracted key number is 80, and the third key number is 87. …
[0053] The key extraction algorithm can also adopt a non-linear extraction method, providing a parabola method to extract the key algorithm (but not limited to this method), the formula is shown in the following formula:
[0054] x(j)=(k*j*j+a) mod N j=1, 2,...
[0055] Where x(j) is the number of the jth key, k is the step factor, a is the starting posi...
Embodiment 3
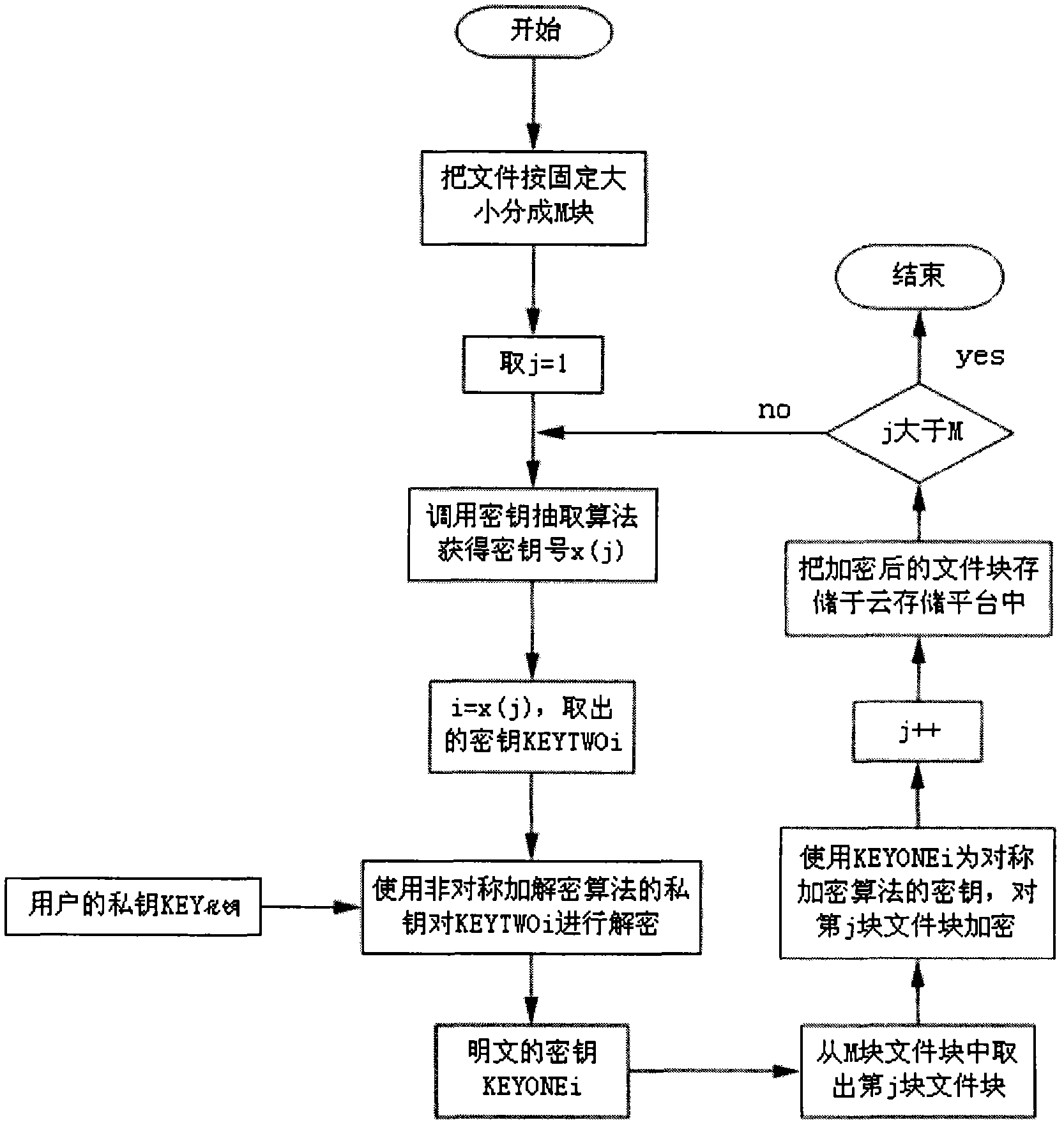
[0057] Example 3. Block encryption of files
[0058] The process of file block encryption refers to the attached picture image 3 , the specific process of file block encryption is introduced below.
[0059] (1) The user selects the file to be encrypted and stored in the terminal, and divides the file (FILE) into several file blocks FILEj (1≤j≤M) according to a fixed size. The last block may be smaller than the fixed size, and j is equal to 1.
[0060] (2) Take the jth (1≤j≤M) file block FILEj from the file block, the block number j of the file block is used as j in the key extraction algorithm, and the key number i=x( j).
[0061] (3) Take out the ciphertext key KEYTWOi (1≤i≤N) from the user’s ciphertext key pool, and use the private key (KEY 私钥 ) and asymmetric encryption algorithm (ECC or RSA) to decrypt KEYTWOi to generate key KEYONEi.
[0062] (4) Use KEYONEi as the key of a symmetric encryption algorithm (such as AES) to encrypt the jth file block FILEj, and store it...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com