Flash malicious file detection method and flash malicious file detection device
A malicious file and detection method technology, applied in the field of data security, can solve the problems of low detection efficiency and precision of flash files, achieve accurate identification and detection, improve accuracy and efficiency, and improve accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0051] refer to figure 1 , showing the first embodiment of the flash malicious file detection method of the present application, comprising the following steps:
[0052] Step 101, analyze the flash file, and extract the bytecode of the virtual machine therein.
[0053]The flash file is composed according to the tag structure, and a frame in the flash is composed of some tags containing graphic data and some tags containing audio data, as well as tags containing ActionScript code. ActionScript is a programming language for the Adobe Flash Player runtime environment that follows the fourth edition of ECMAscript. It implements interactivity, data processing, and other functions in flash content and applications. Adobe Flash Player has a built-in AVM virtual machine, and the AVM virtual machine converts the ActionScript bytecode (ActionScript Bytecode) in the flash file into corresponding instructions according to different platforms before running.
[0054] When parsing the fla...
example 1
[0069] Example 1: Assume that the pre-analysis shows that the int type "0x90909090" characteristic bytecode basically does not exist in normal flash files, but this characteristic appears in malicious flash files due to special code writing requirements The number of bytecodes is very high, so you can use "0x90909090" as a parameter at this time, and set the threshold for the number of occurrences, and write the following judgment function:
[0070]
[0071] This section of source code counts the number of occurrences of int type parameters of 0x90909090 in the virtual machine bytecode of a flash file to be detected. When such parameters appear more than a threshold value, it will match a virtual machine bytecode feature, and it is considered The flash file to be detected is a malicious file.
example 2
[0072] Example 2, the key string in the malicious flash file is often encrypted by XOR (exclusive OR) encryption, then the encryption method can be added to the judgment function to realize the judgment. The specific judgment function written is as follows:
[0073]
[0074]
[0075] This piece of source code converts a string that executes malicious commands into 256 sets of XOR (exclusive OR) encrypted strings, which can intelligently match encrypted malicious commands that often appear in malicious flash files, as long as the malicious command meets 256 sets of strings Any one of them, then it can be judged that the flash file is a malicious file, which improves the accuracy of the detection result. There will be no misjudgment due to encryption or not. At the same time, one judgment function can be realized without adding multiple functions for multiple judgments, which can save detection time and space.
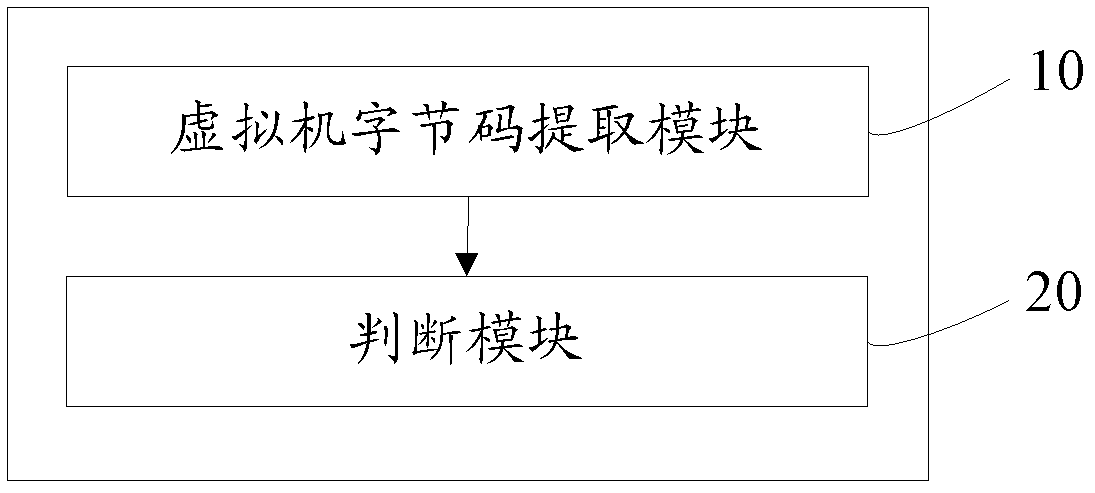
[0076] refer to figure 2 , shows Embodiment 1 of an apparat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com