Security certificate method and system of credible TV terminal
A TV terminal and security authentication technology, applied in the field of TV, can solve the problems of low concealment, easy to be deciphered, poor security, etc., and achieve the effect of high concealment, improved hardware architecture and system integrity, and not easy to leak
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0054] It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
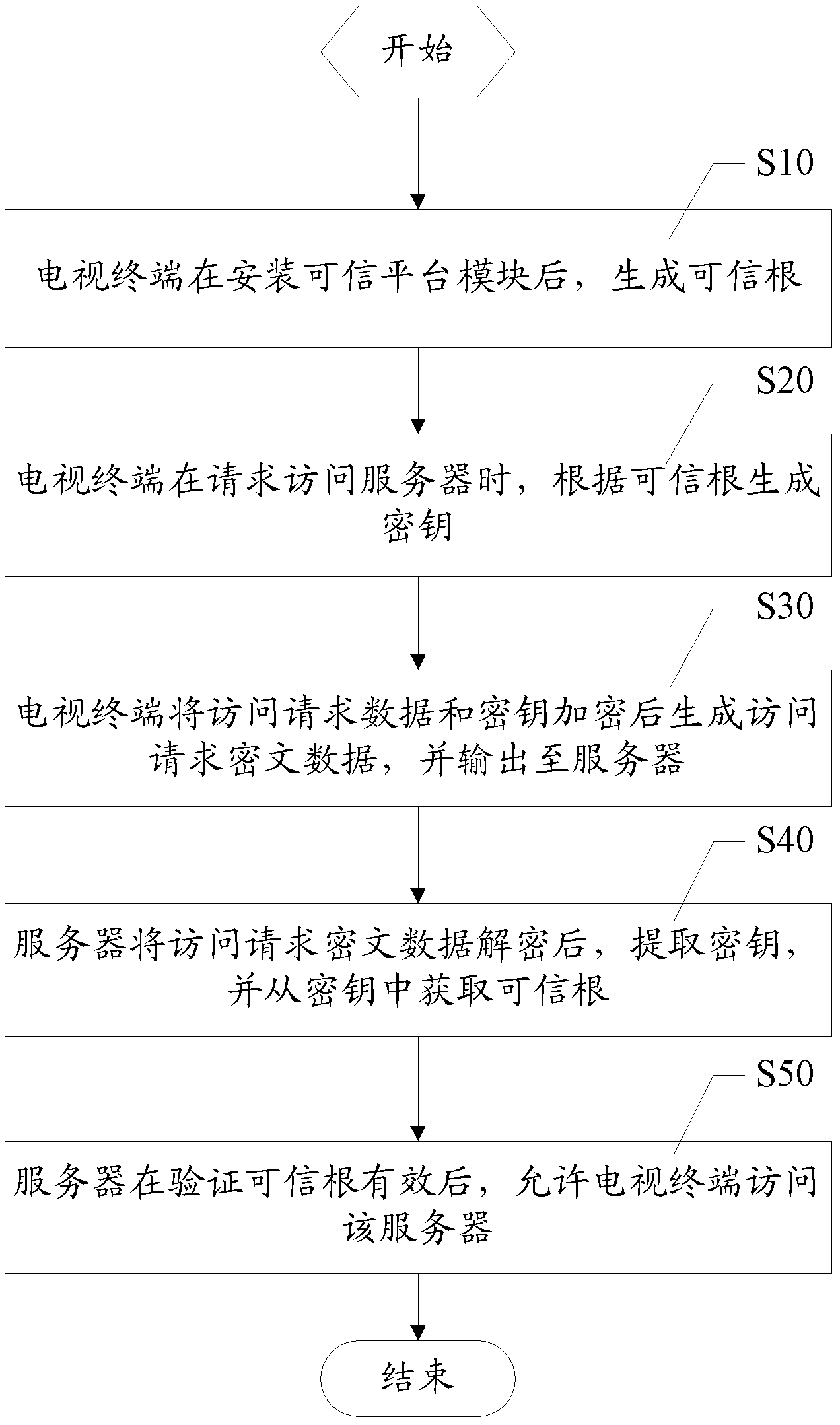
[0055] Such as figure 1 as shown, figure 1 It is a flow chart of the trusted TV terminal security authentication method in the first embodiment of the present invention. The trusted TV terminal security authentication method mentioned in this embodiment includes:
[0056] Step S10, the TV terminal generates a root of trust after installing the trusted platform module;
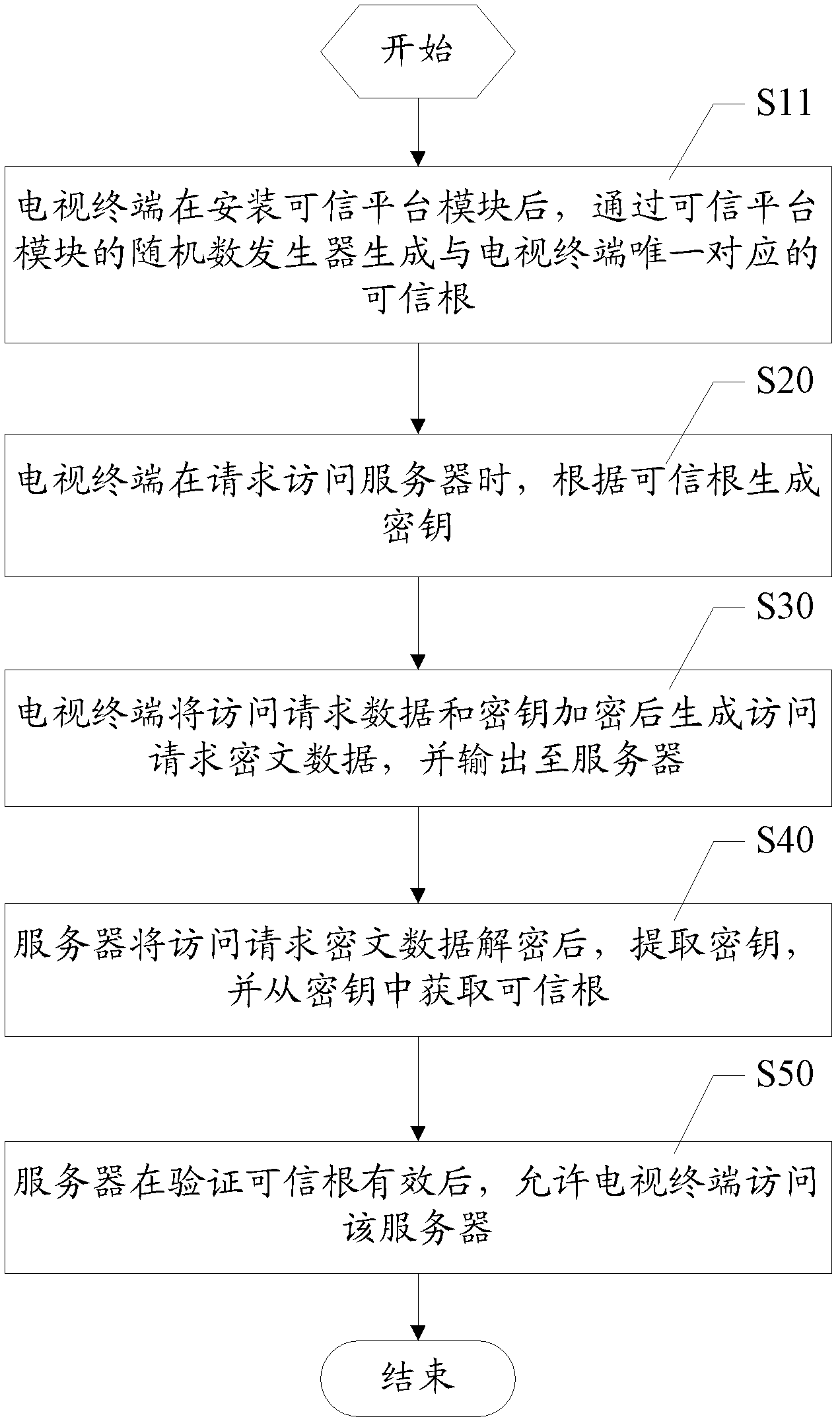
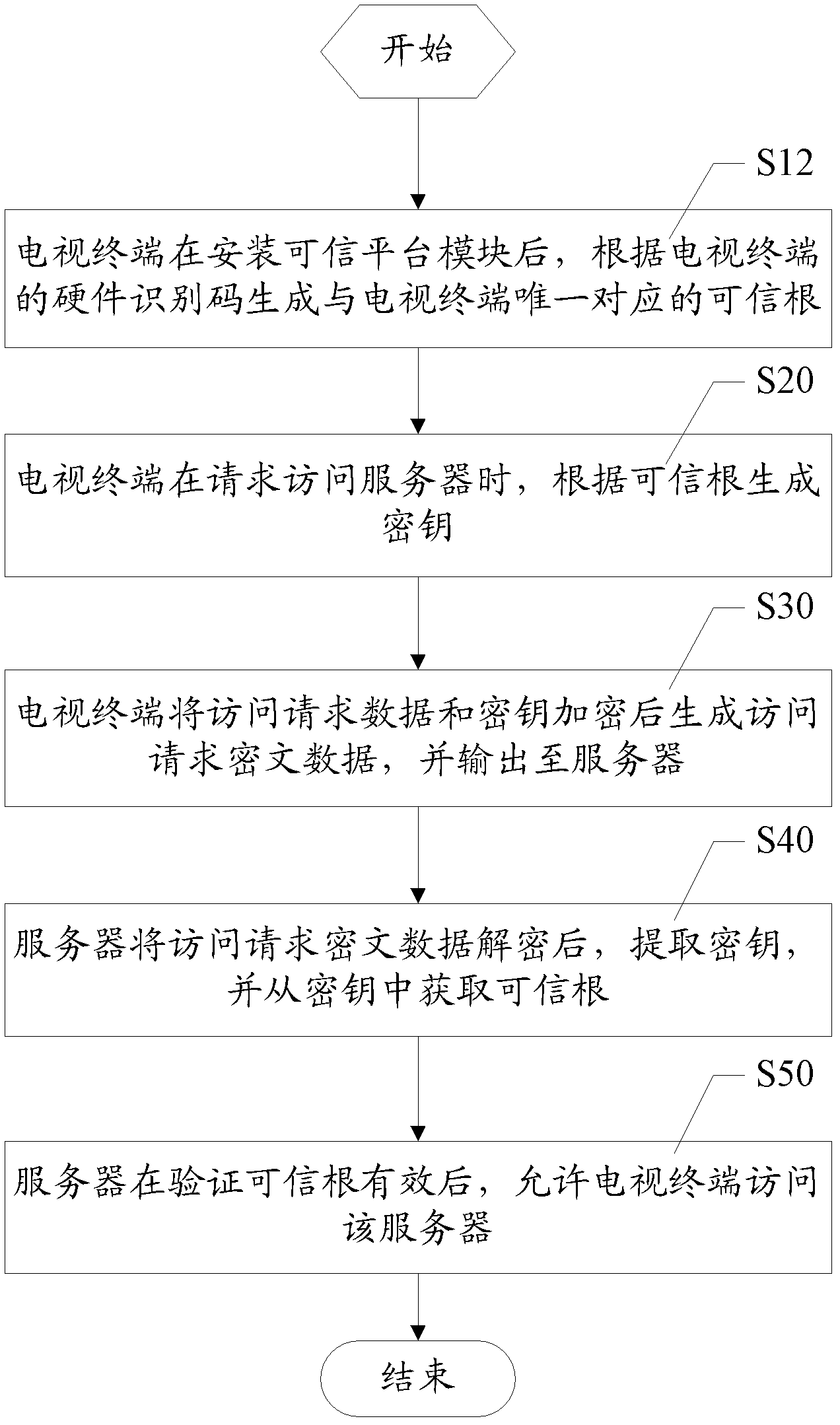
[0057] In this embodiment, during the TV production process, a TPM (Trusted Platform Module, Trusted Platform Module) security chip is installed on the TV hardware platform. Since the TPM includes components such as a cryptographic operator and a memory, a series of passwords can be provided. Processing functions, such as RSA accelerator, algorithm engine, random number generator, and key storage functions, after the trusted platform module is loaded...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap