Enterprise and public institution information leakage preventing method based on cloud architecture
An enterprise and cloud architecture technology, applied in the field of computer security, can solve problems such as inability to encrypt files, inability to guarantee file ciphertext, and inability to set permissions for different files to different enterprises and institutions, so as to facilitate mutual communication and communication. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] The present invention will be described in detail below in conjunction with the accompanying drawings. As a part of this specification, the principle of the present invention will be described through embodiments. Other aspects, features and advantages of the present invention will become clear at a glance through the detailed description.
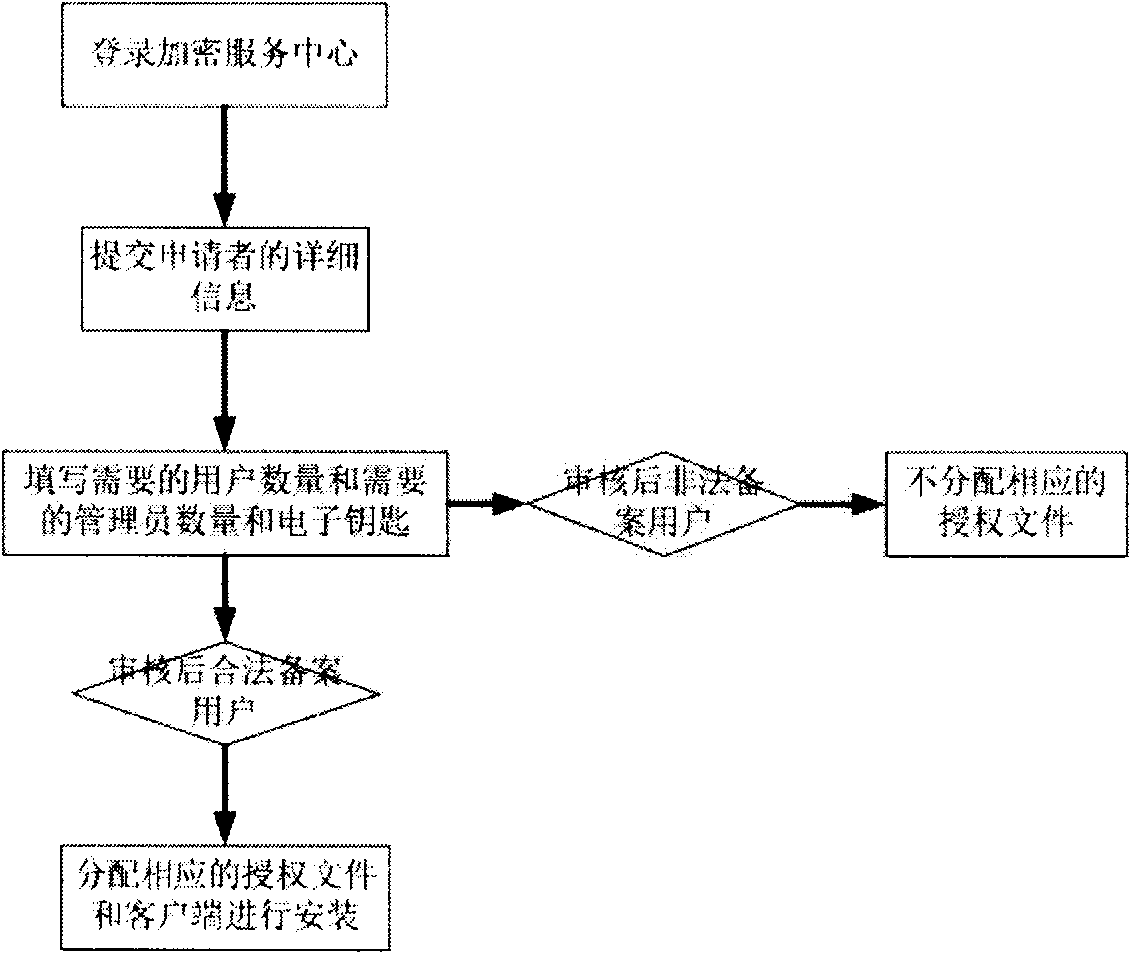
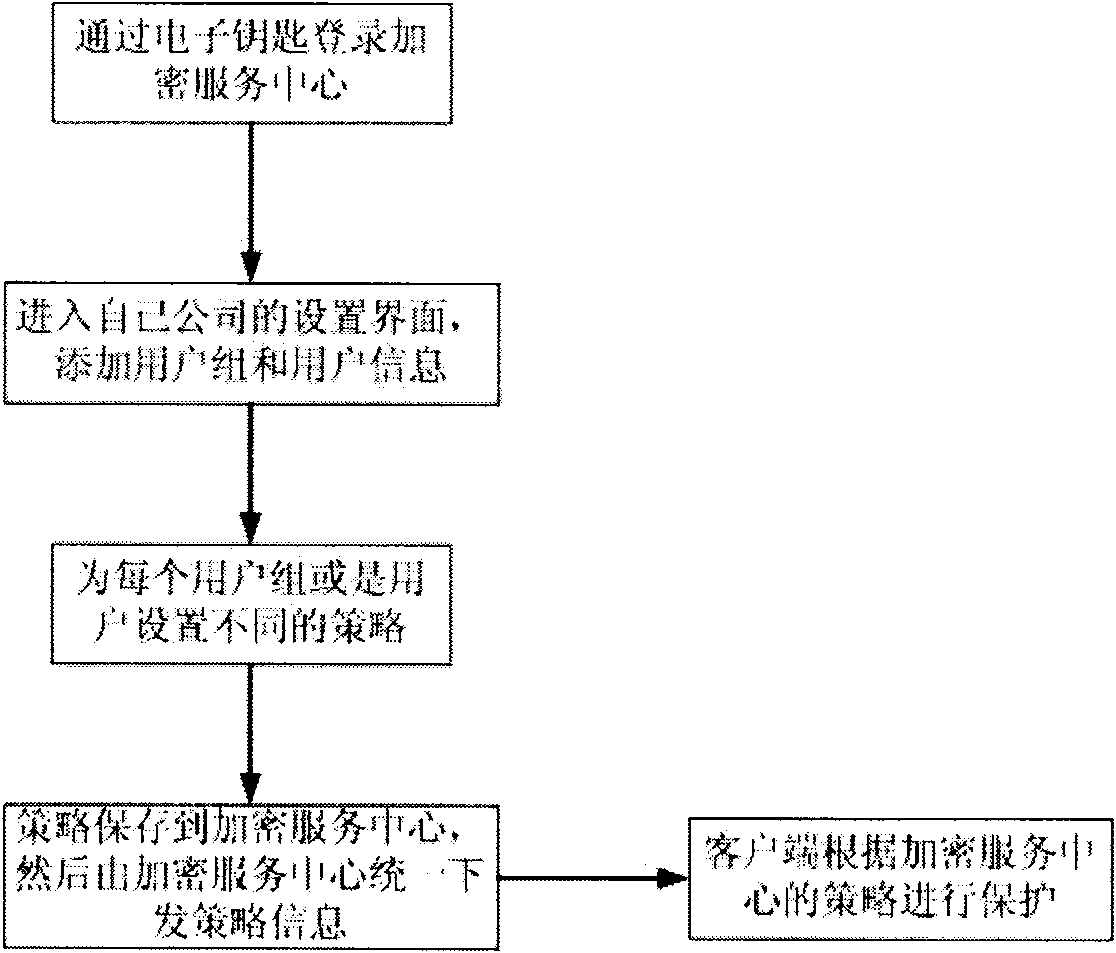
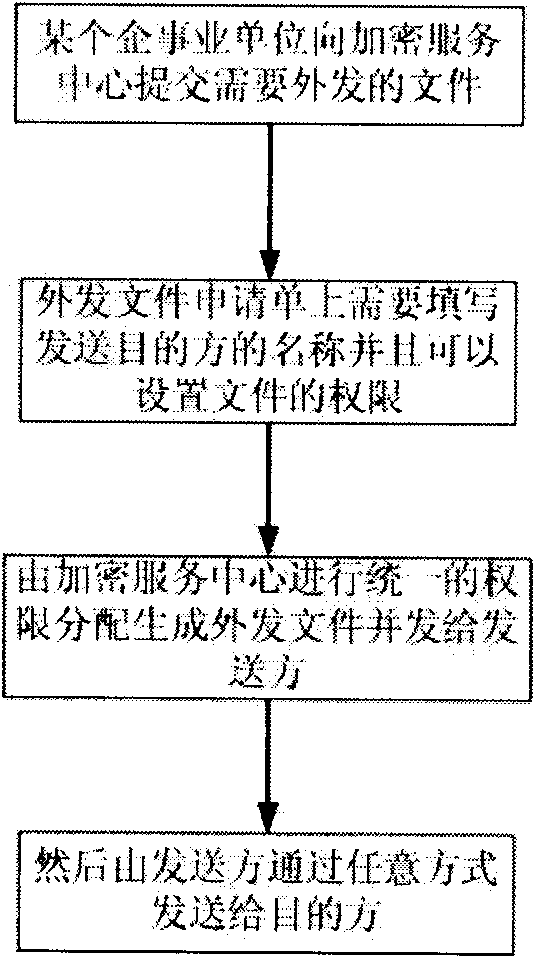
[0023] A method for preventing information leakage of enterprises and institutions based on cloud architecture provided by the present invention, wherein the steps are as follows:
[0024] (1) Establish a large-scale IDC (Internet Data Center) hosting computer room that provides encryption services on the Internet, that is, an encryption service center. All enterprises and institutions apply to the encryption service center for encryption services using different algorithms and the number of user groups that need services and the number of users,
[0025] (2) The encryption service center uniformly distributes different encryption a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com