Method and server for monitoring network user behavior
A network user and server technology, applied in the computer field, can solve problems such as inaccurate network user behavior monitoring and complex user behavior execution, and achieve the effect of reducing impact and ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
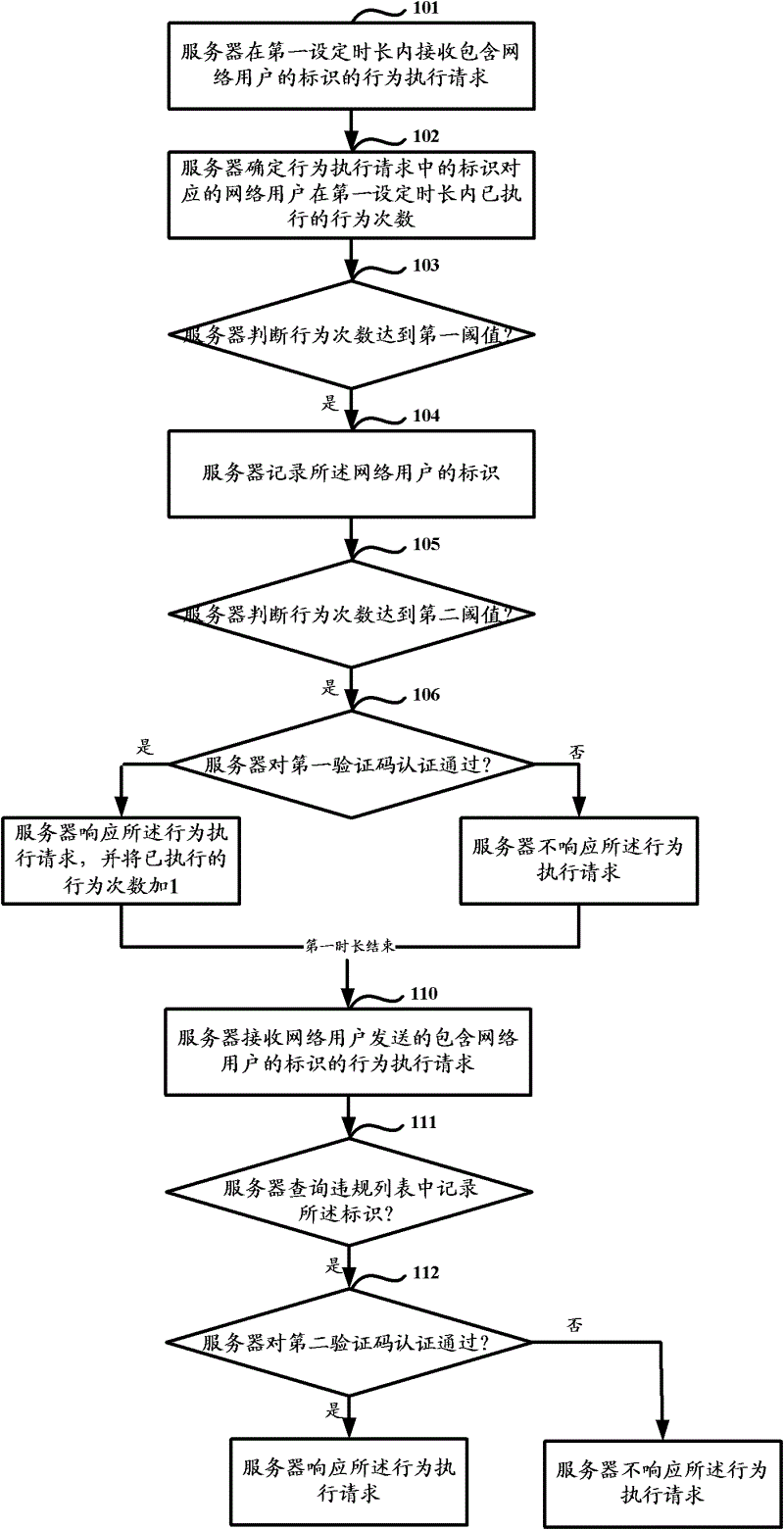
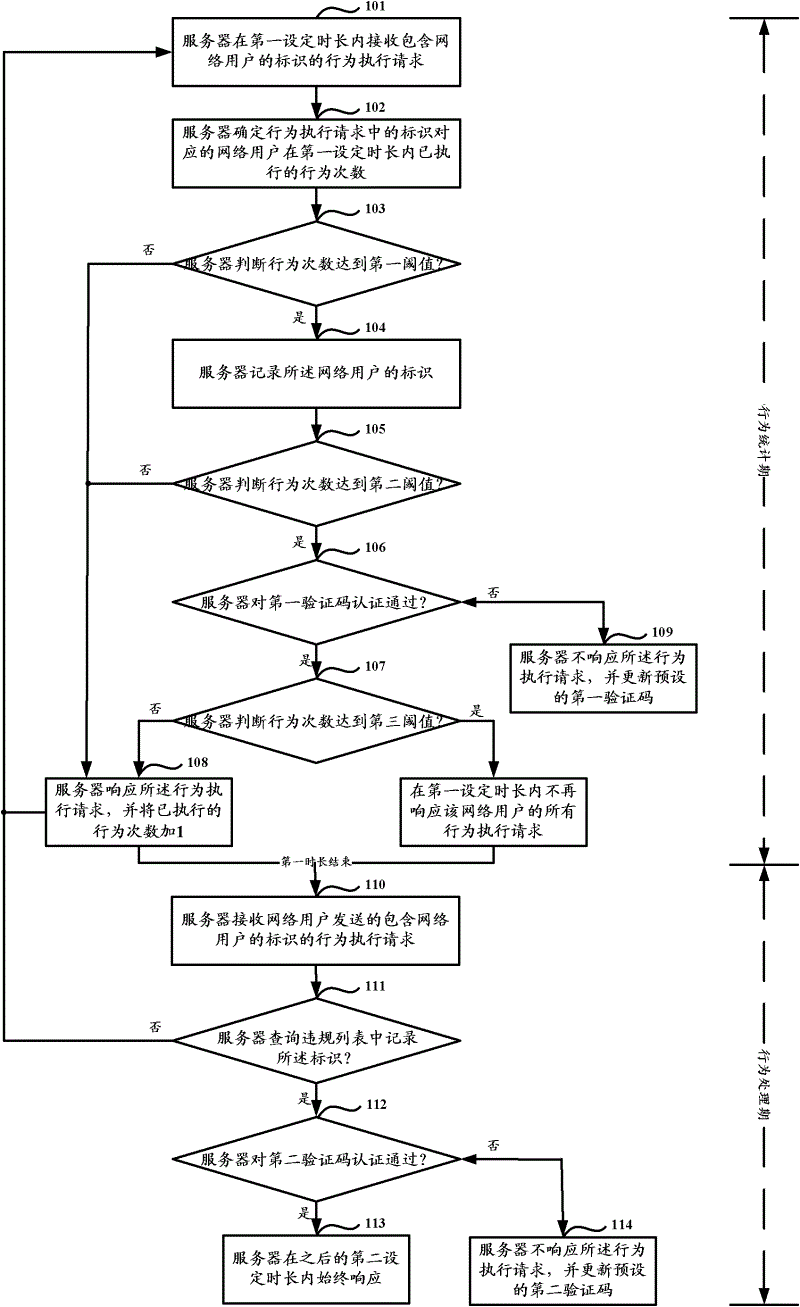
[0031] Embodiment 1 of the present application provides a method for monitoring network user behavior, as shown in FIG. 1(a) and FIG. 1(b), the method includes a behavior statistics period and a behavior processing period. The behavior statistics period is the process of collecting statistics on the behavior of network users within the set period of time, and the behavior processing period is the process of processing network users according to the violation information determined within the set period of time after the set period of time ends.
[0032] The specific description of the behavior statistics period is as follows:
[0033] Step 101: The server receives an action execution request including the identifier of the network user within a first set time period.
[0034] In this step, before a network user accesses the network server or sends information to other network users, he needs to first send a behavior execution request containing his own identity to the server. ...
Embodiment 2
[0064] Embodiment 2 of the present application describes the scheme of Embodiment 1 in detail through a specific example.
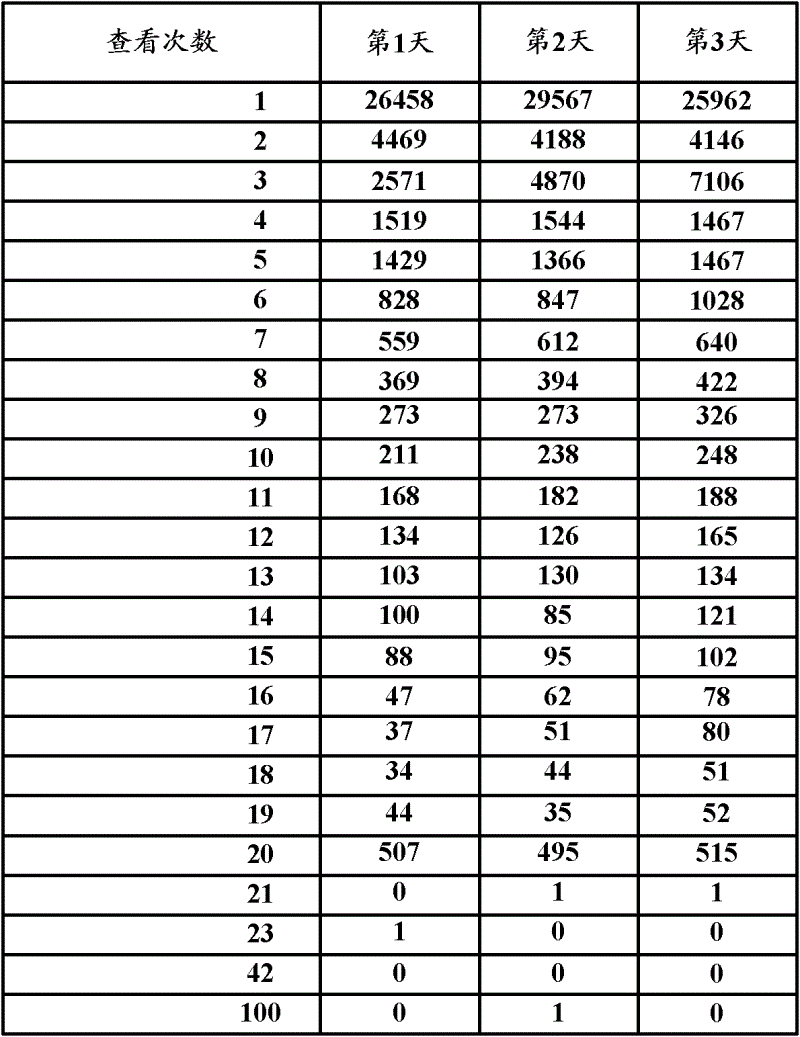
[0065] Assume that the behavior of the network user in the second embodiment is that the instant messaging client checks the buddy list, such as figure 2 As shown, it is the number of people corresponding to different viewing times within three days. Taking 1 viewing as an example, 26,458 people viewed it once on the first day, 29,567 people viewed it once on the second day, and 25,962 people viewed it on the third day 1 time.
[0066] from figure 2 It can be seen from the figure that the vast majority of network users check the friends list within 14 times a day, and a small number of network users check the friends list 15-19 times a day, but when the number of times they check the friend list is 20 times a day , the number of people suddenly increased, it can be considered that the number of times to check the friends list is 20 times a day is the cr...
Embodiment 3
[0099] As shown in Figure 3 (a), it is a schematic diagram of the server structure of a network user behavior monitoring provided in Embodiment 3 of the present application, including a number determination module 11, a first judgment module 12, a second judgment module 13 and a verification module 14 , wherein: the number of times determination module 11 is used to determine the number of behaviors that the network user corresponding to the identifier has performed in the first set time period when receiving a behavior execution request that includes the network user identifier within the first set duration; the first The judging module 12 is used to judge whether the number of times of the behavior reaches the first threshold, and when the first threshold is reached, record the identification of the network user, and trigger the second judging module 13; the second judging module 13 is used to judge the Whether the execution times reach the second threshold, and trigger the v...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com