Implementation method for safety link of internet lottery ticket system based on public key
A public key, system security technology, applied in transmission systems, electrical components, marketing, etc., can solve the problems of user personal information to ensure high-level business security, inability to prevent intrusive operations, and inability to prevent misappropriation of distributed denial of service attacks. , to achieve the effect of strengthening safety certification, ensuring reliability and stability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
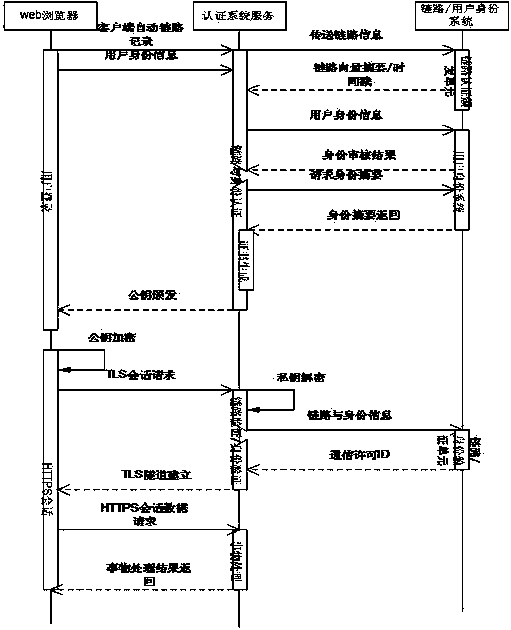
[0025] Such as figure 1 As shown, a method for implementing a public key-based Internet lottery system security link, the specific implementation steps are as follows:
[0026] (1) Combination of public key, private key, security certificate and user identity system generated by independent authentication and authorization methods;
[0027] (2) HTTPS protocol processing of self-authentication credentials, before the TLS link is established, use the user identity system and dynamic link vector to perform identity authentication and link authentication;
[0028] (3) At the initial stage of the session, check whether the authentication vector comes from the authorized network, and then check whether the user identity system is a subscriber. At the initial stage of the session, check whether the authentication vector comes from the authorized network, and then check whether the user identity system is a subscriber. If not, then The web browser jumps to the registrati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com