Flash bug detection method based on virtual execution mode
A virtual execution and vulnerability detection technology, applied in the direction of program/content distribution protection, platform integrity maintenance, etc., can solve problems such as low efficiency, achieve high efficiency, high correct rate, and low false positive rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
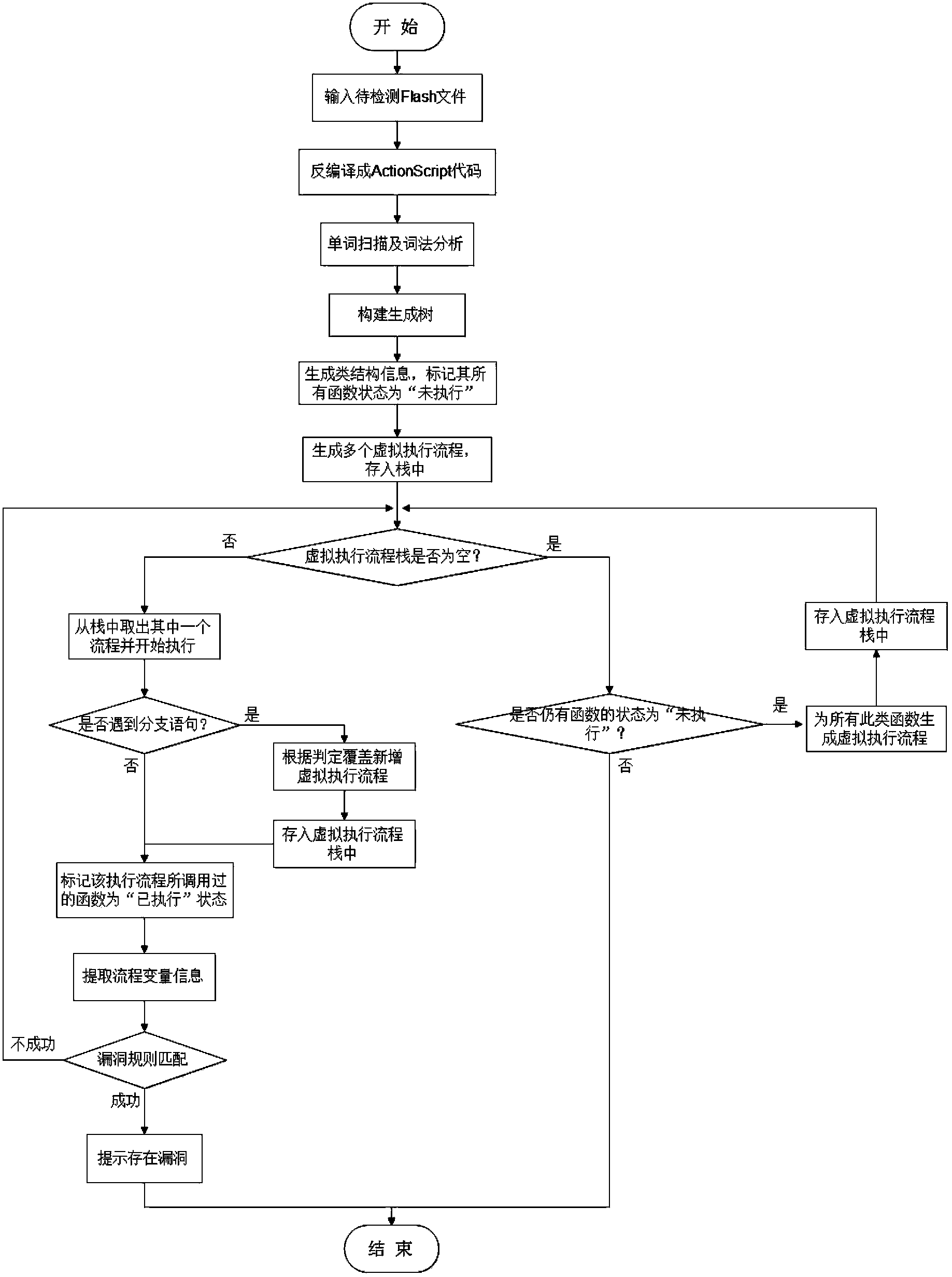
[0081] figure 1 It is a flowchart of the present invention, and the steps are as follows:
[0082] (1) Decompile the Flash file to get the ActionScript code
[0083] Since the Flash compiler converts ActionScript code into an intermediate code format called "bytecode" when compiling ActionScript code, it needs to be decompiled first.
[0084] (2) Word scanning and lexical analysis
[0085] After decompiling the ActionScript code, in order to facilitate subsequent analysis and virtual execution, the code needs to be scanned for words, that is, the ActionScript code is converted into a word stream, and the type of each word is analyzed.
[0086] For example, for the following statement: var num:int=10;, after word scanning and lexical analysis, the following word stream should be generated ("var", reserved word), ("num", identifier), (":", symbol) , ("int", reserved word), ("=", symbol), ("10", number), (";", symbol).
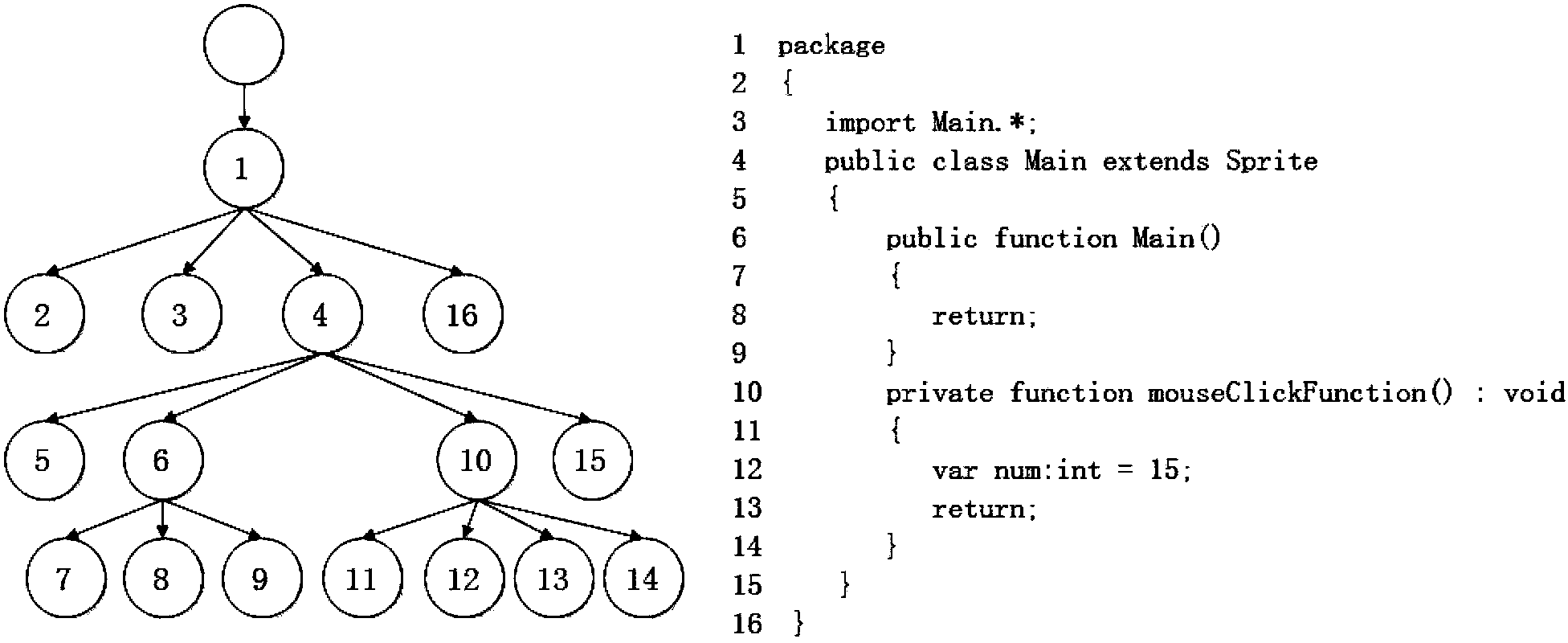
[0087] (3) Build a spanning tree
[0088] To facilitate ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com