Method and device for security configuration optimization
A technology for securely configuring and optimizing devices, which is applied in the field of network security and can solve problems such as low usability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
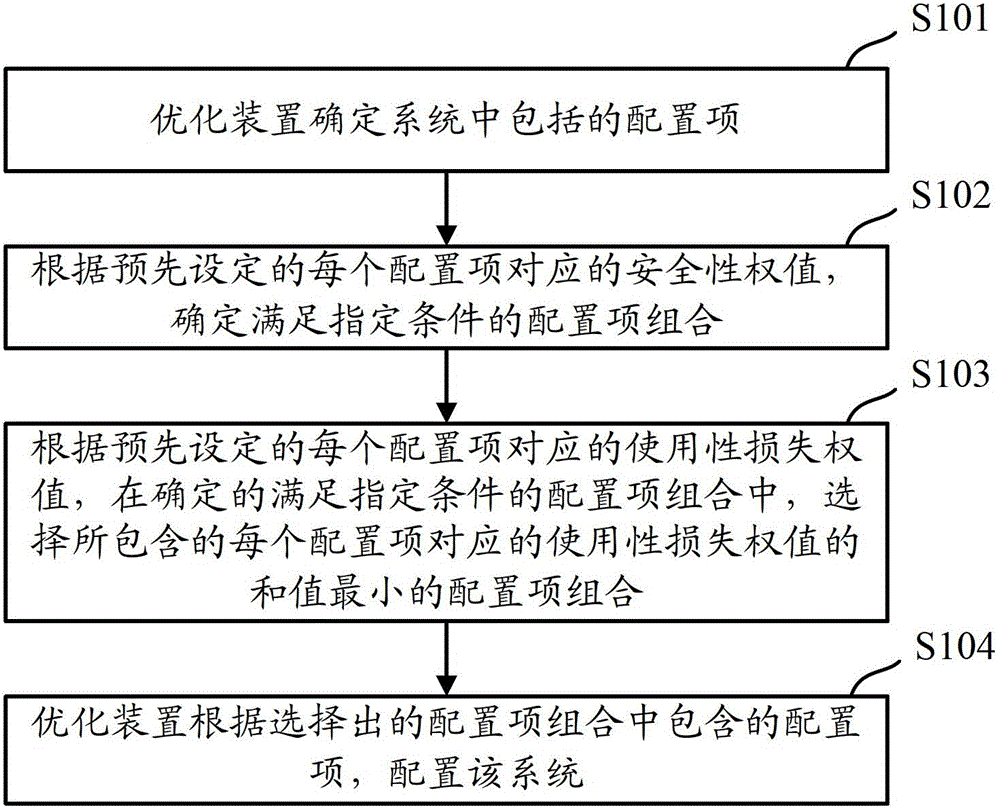
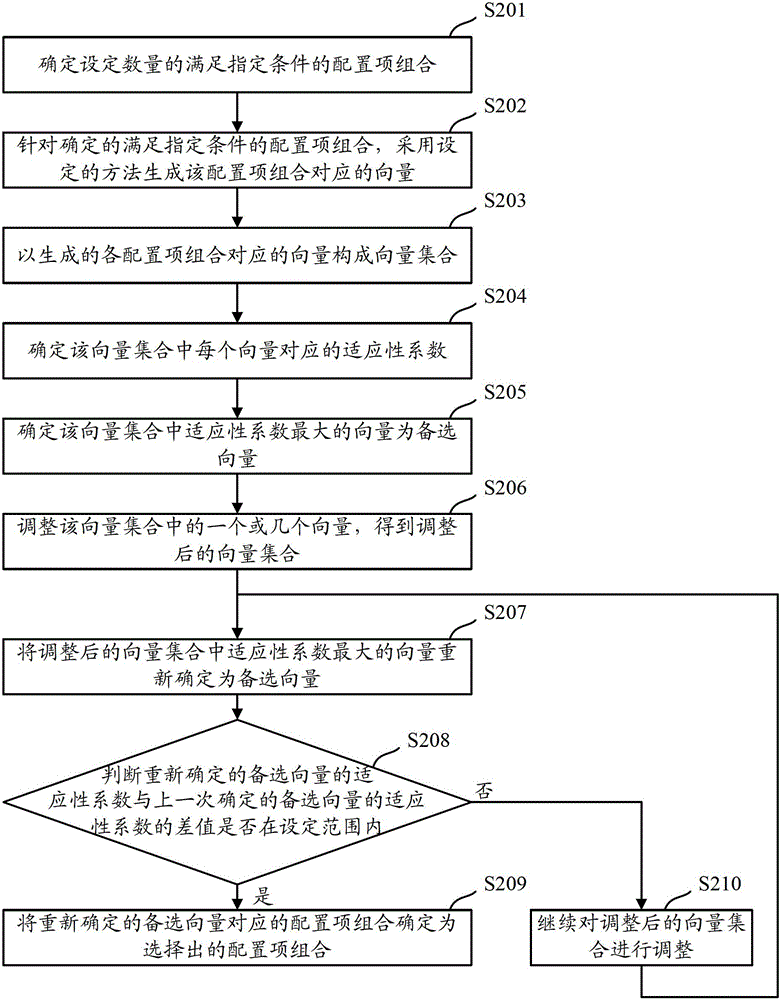
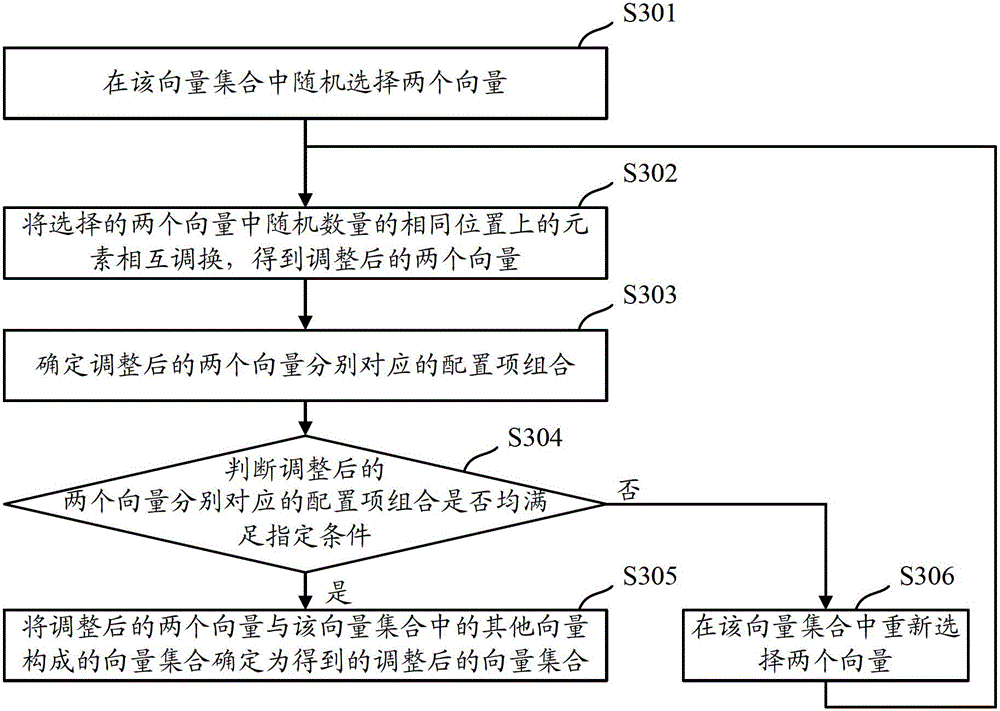
[0023] When configuring the configuration items in the system in the prior art, only the impact of the configuration items on the system security is considered, and the impact of the configuration items on the usability of the system is not considered, so the configured system often meets the safety requirements requirements, but very low usability. The embodiment of the present invention aims to select a combination of configuration items that minimizes the reduction in system usability from the configuration items included in the system under the premise of meeting the system security requirements, and configure the configuration according to the selected configuration item combination After the system is installed, the configured system can be configured to maximize the usability of the system on the premise of meeting the security requirements.
[0024] Embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings.
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com