Safe protecting method and device for Web verification code with combined picture and characters
A security protection and verification code technology, applied in the field of information security, can solve problems such as high difficulty, difficult to recognize by human eyes, and limited application scope, and achieve the effect of reducing the automatic recognition rate, not easy to read the wrong answer, and improving the recognition rate.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
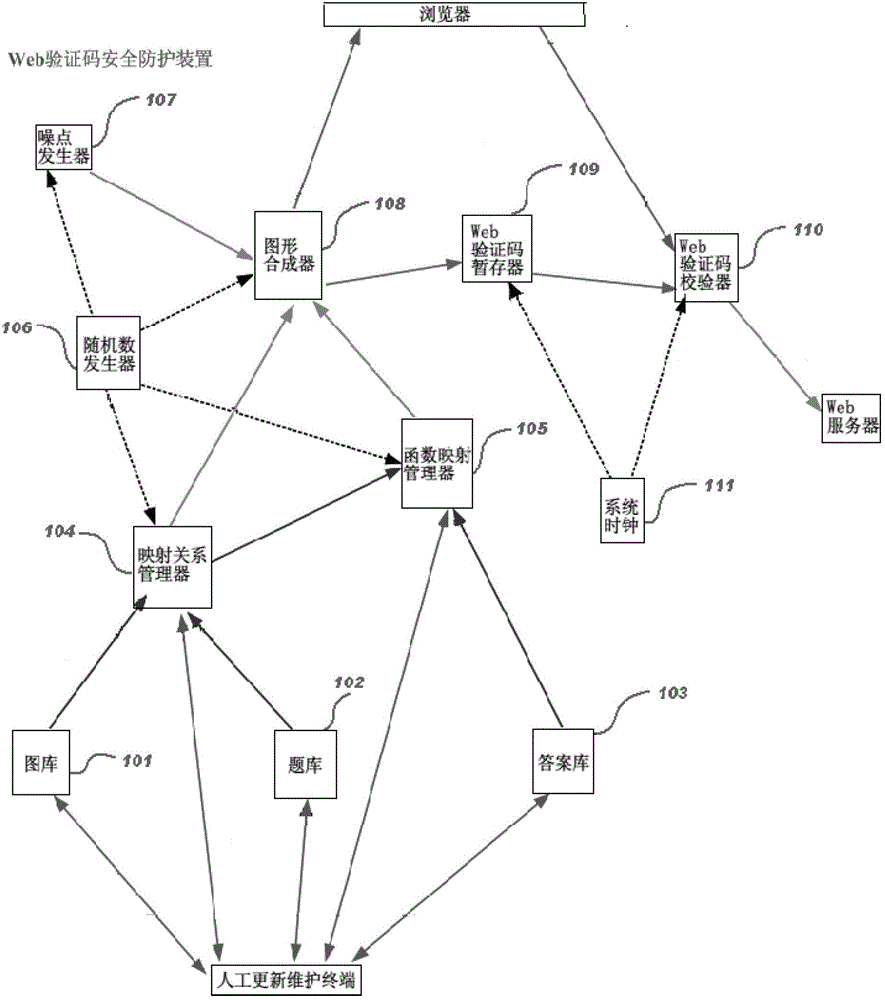
[0056] Such as figure 1 As shown, a graphic-text combined web verification code security protection device includes:
[0057] Gallery 101, used to store and manage pictures related to Web verification codes;
[0058] Question bank 102, used for storing and managing questions related to pictures;
[0059] Answer library 103, used for storing and managing answers related to questions;
[0060] Mapping relationship manager 104, used to store and manage the many-to-many relationship between pictures and questions;
[0061] The function mapping manager 105 is used to store and manage the function mapping relationship between pictures, question pairs and answers, that is: many-to-one mapping relationship;
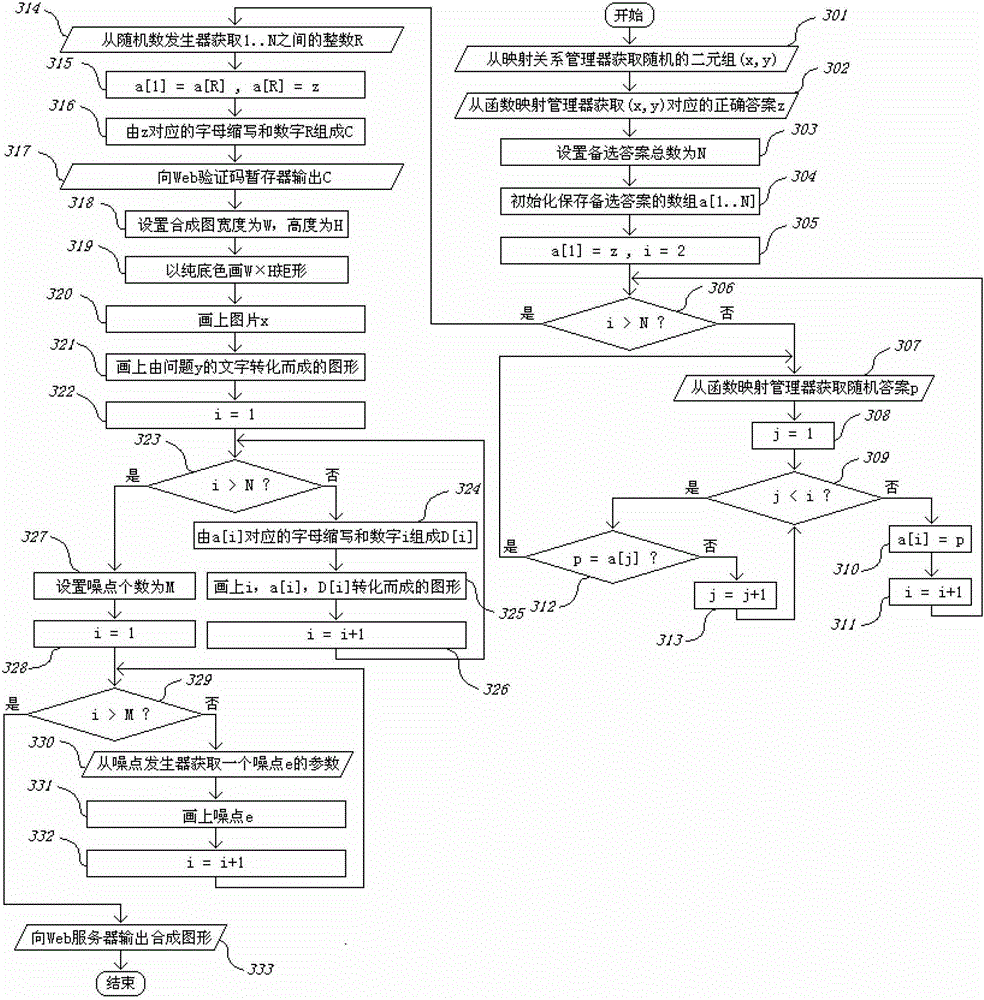
[0062] The random number generator 106 is used to generate a plurality of random numbers, which are respectively provided to the mapping relationship manager 104 to screen pictures and question pairs, and to the function mapping manager 105 to screen the correct answer and oth...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com