802.1X authentication method and equipment
An authentication method and AP device technology, applied in the communication field, can solve the problems of not being able to perceive the client and difficult management of the client, and achieve the effect of precise management and control
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
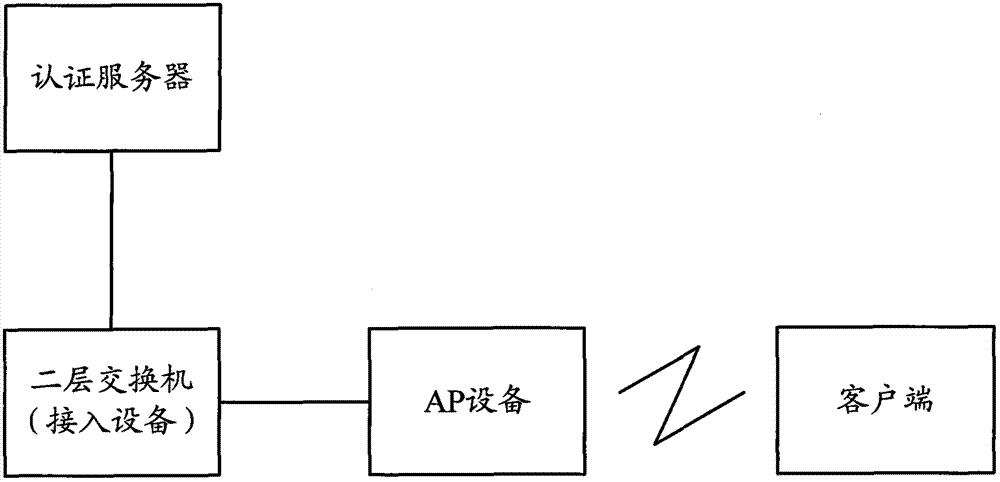
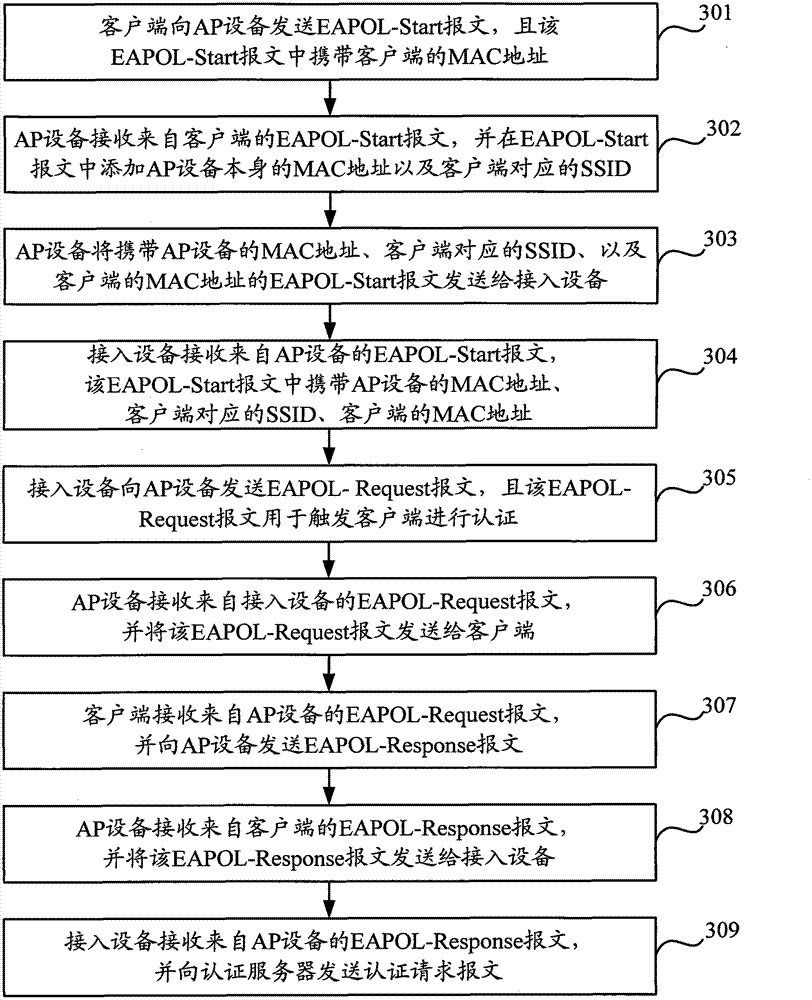
[0041] by figure 2 It is a schematic diagram of the application scenario of the present invention. When the 802.1X authentication function is configured on the access device (that is, the Layer 2 switch), the 802.1X protocol message will be issued to report the discarding rule of the unknown source MAC address. When the client fails to pass the authentication , only the 802.1X protocol packets are sent to the upper-layer 802.1X module, and other packets will be discarded; after the client passes the authentication, it will issue the MAC forwarding entry. Exists, if it exists, forward the packet normally.
[0042] in the above figure 2 In the application scenario shown, after the client and the AP device are successfully connected, the AP device only forwards the packet. Therefore, when the authentication packet reaches the access device, the access device cannot know exactly whether the client is connected wirelessly. It is still connected in a wired way, and it is impossi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com