Method for detecting network anomaly of wireless sensor based on trust evaluation
A wireless sensor and detection method technology, applied in wireless communication, electrical components, security devices, etc., can solve problems such as failure to consider the reliability of recommended nodes, high misjudgment rate, and inability to detect attack types well
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
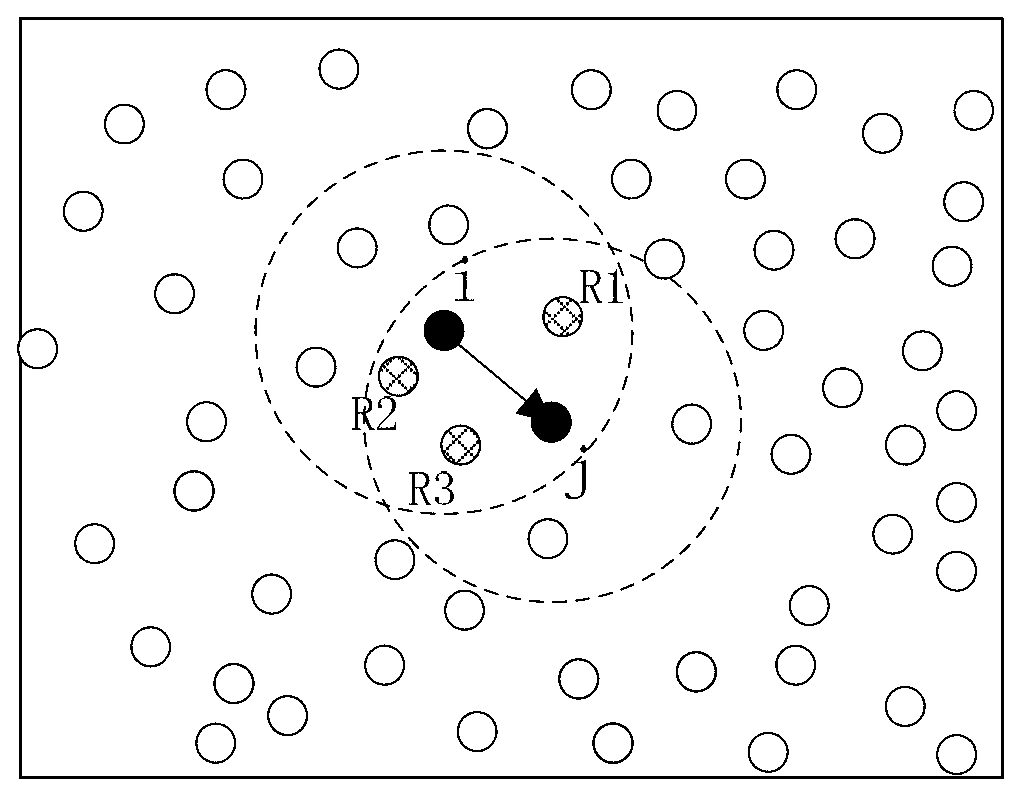
[0067] Such as figure 2 As shown, node i in the figure conducts trust evaluation on node j, and the dotted circle represents the transmission range of the node. Node j must be within the communication range of node i. And node i only receives recommendation information about node j from recommending nodes R1, R2, R3, that is, common neighbor nodes of node i and node j. This is because the more hops the evaluation node receives from the evaluation node's recommendation information, the lower its authenticity. In order to prevent internal attacks such as bad mouth attacks, the trust model in the present invention only receives recommended information with a total hop count of two hops (the recommended information within the range of one hop is essentially direct monitoring information).
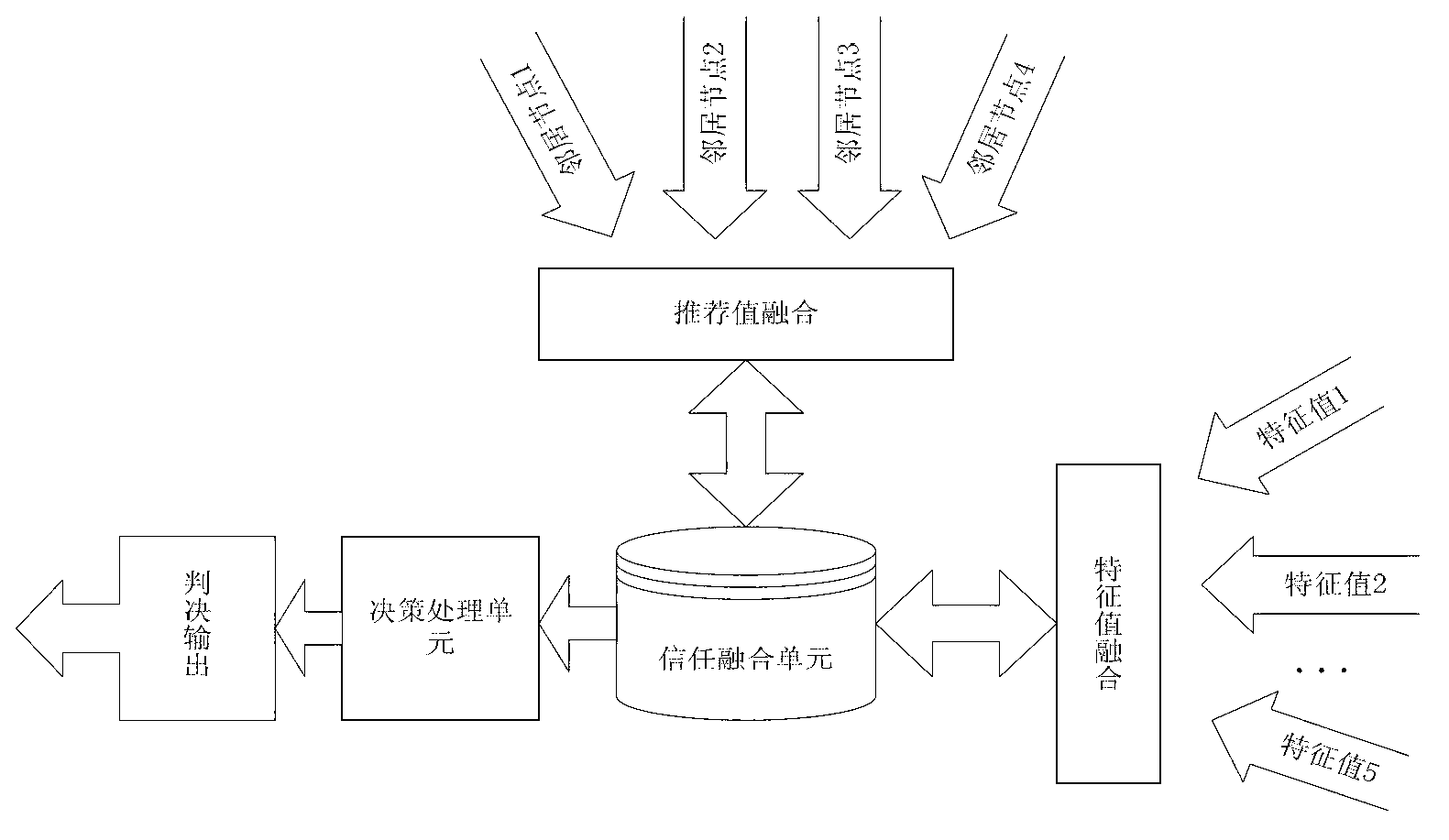
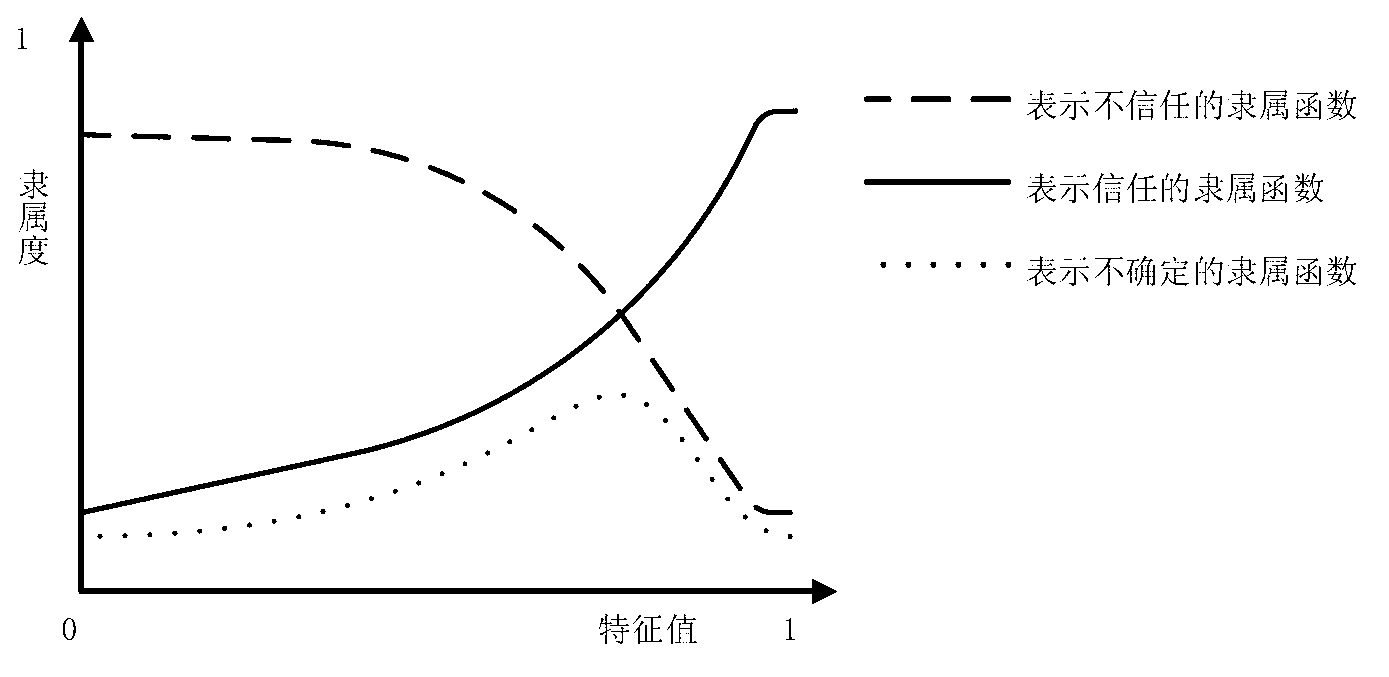
[0068] The trust model of the present invention consists of 5 stages. Including monitoring stage, fuzzy stage, DS fusion stage, recommendation information processing stage, judgment stage. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com