Solution for potential safety hazards in VPN (virtual private network)
A technology of virtual private network and security risks, which is applied in the direction of network interconnection, data exchange through path configuration, electrical components, etc., and can solve problems such as constraints, security passivity, and leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0071] The following describes in detail the embodiments of the solution to the hidden security risks in the virtual private network in conjunction with the accompanying drawings.
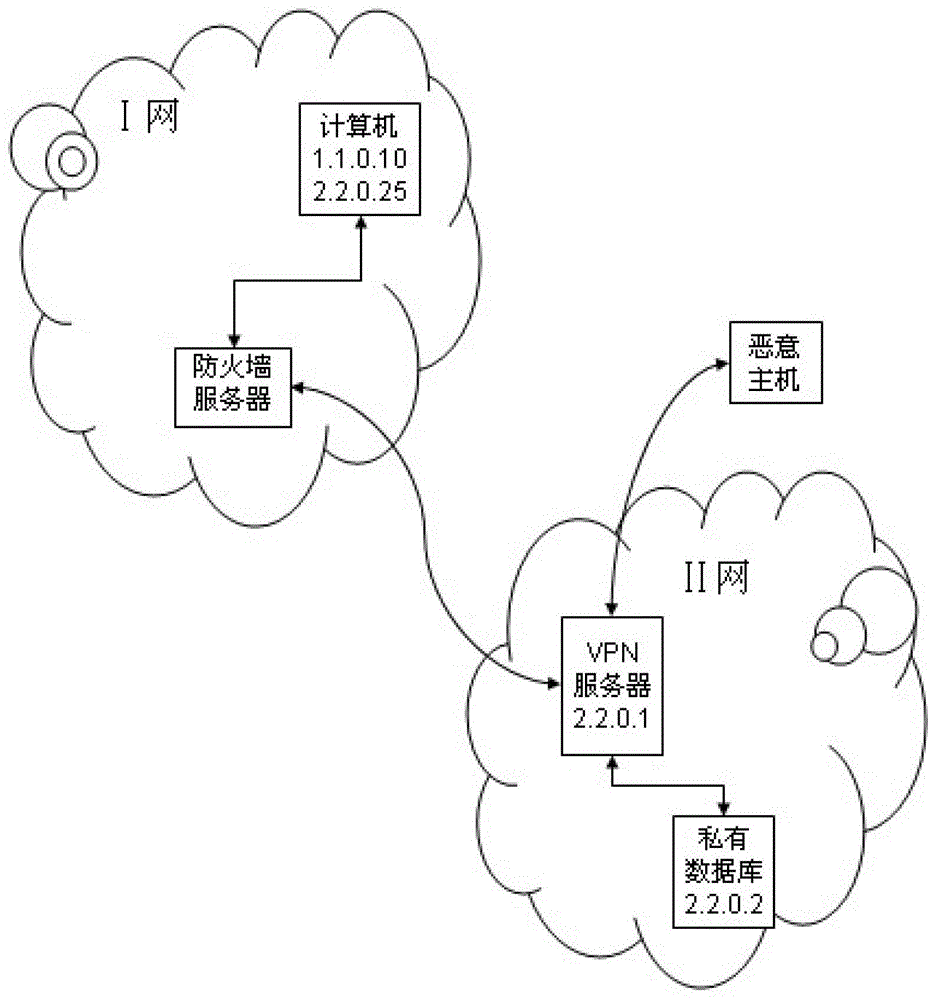
[0072] figure 1 Shown is the connection and communication situation of the virtual private network established on the basis of the public network in the embodiment of the solution to the hidden danger in the virtual private network, figure 1 The Ⅰ network and the Ⅱ network are two local networks; there is a firewall server in the Ⅰ network, the IP address of a computer in the Ⅰ network is 1.1.0.10, and the IP address of a roaming user on the Ⅱ network is 2.2.0.25. The computer can The firewall server in the I network is connected to the computer in the II network for communication. There is a VPN server (IP address 2.2.0.1) in the Ⅱ network, and a confidential private database (IP address 2.2.0.2) is connected to the VPN server. When the private database in the II network communicates with the compu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com