Method and device for detecting suspicious progresses
A process and suspicious technology, applied in the field of information security, can solve the problems of virus false positives and false negatives, user losses, user-triggered virus detection lag, etc., to avoid attacks and improve security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0067] In order to make the above objects, features and advantages of the present application more obvious and comprehensible, the present application will be further described in detail below in conjunction with the accompanying drawings and specific implementation methods.
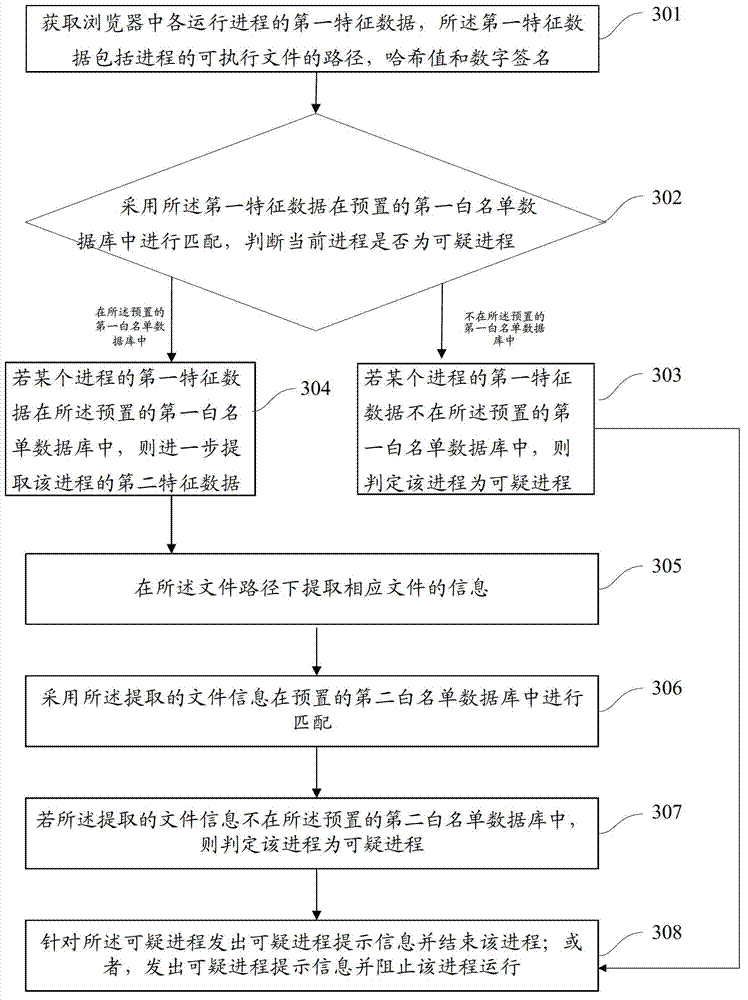
[0068] One of the core concepts of the embodiments of the present application is to propose a mechanism for whitelist detection of processes running in the browser, and to effectively prevent suspicious processes running in the browser by using the "white or black" feature of the whitelist. Improve the security of users surfing the Internet.
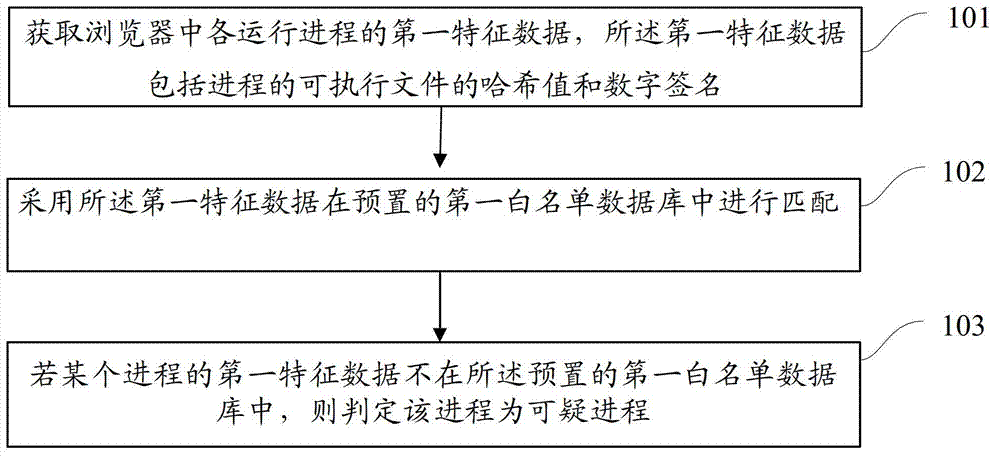
[0069] refer to figure 1 , shows a flow chart of the steps of Embodiment 1 of a suspicious process detection method of the present application, which may specifically include the following steps:
[0070] Step 101, acquiring the first feature data of each running process in the browser, the first feature data including the hash value and digital signature of the e...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com