Method for realizing secure transmission of data in cloud storage system
A cloud storage system and data security technology, applied in transmission systems and key distribution, can solve problems such as multi-resources, system throughput performance impact, unsuitable for large data transmission environments, etc., to achieve the effect of ensuring privacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0015] The method of the present invention is described in detail below with reference to the accompanying drawings.
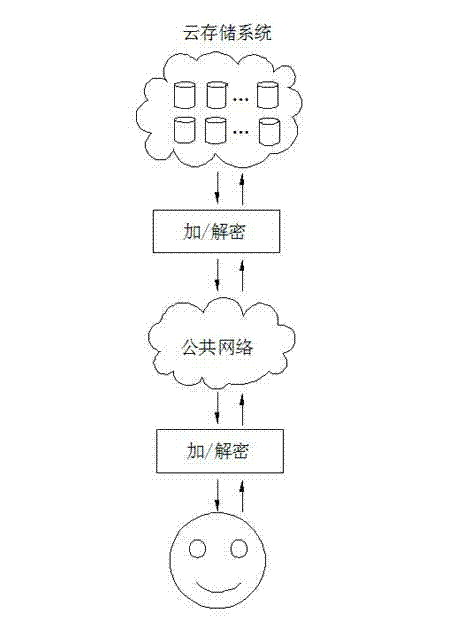
[0016] A method for a data security transmission policy in a cloud storage system relates to the security and efficiency of the cloud storage system during transmission. The specific steps of the data security transmission method are as follows:
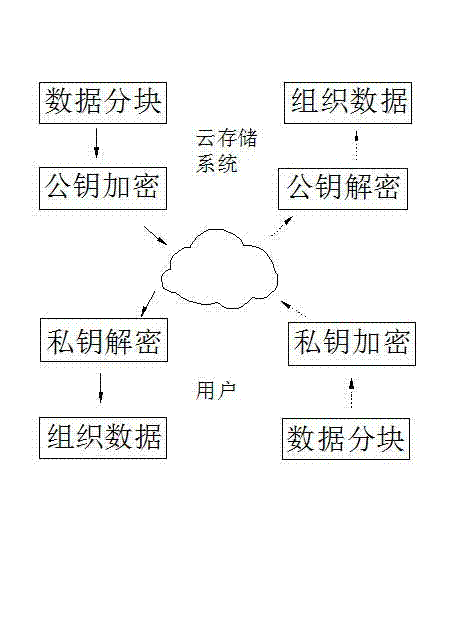
[0017] (1) During actual data transmission, symmetric or asymmetric algorithms can be used to encrypt data according to the size of the transmitted data. When a large amount of data is transmitted, in order to ensure throughput, the data is encrypted and decrypted using a symmetric algorithm. For a small amount of data, asymmetric algorithms can be used. Symmetric algorithm encrypts data;
[0018] (2) When the symmetric algorithm is used, the key is randomly created before data transmission, and the asymmetric algorithm is used to encrypt and decrypt the key for the negotiation and exchange process of the key, so a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com