Method for implementing start-up protection on mobile terminal
A mobile terminal and power-on password technology, which is applied in the field of information security, can solve the problems of users' private information leakage and mobile terminal unusability, and achieve the effect of avoiding leakage and facilitating after-sales maintenance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] In order to facilitate the understanding of those skilled in the art, the present invention will be further described below with reference to the accompanying drawings.
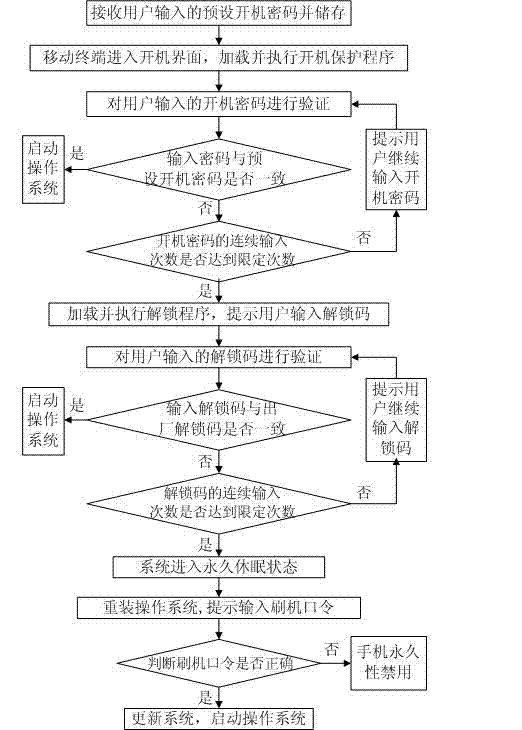
[0026] A method for mobile terminal to realize boot protection, as attached figure 1 As shown, the method includes:
[0027] Step 001: Receive and store the preset power-on password input by the user;
[0028] Step 002: When the mobile terminal enters the boot interface, load and execute the boot protection program, and prompt the user to enter the boot password;
[0029] Step 003: Verify the power-on password entered by the user. When the input password is consistent with the preset power-on password, load and execute the boot program, that is, start the operating system, otherwise go to step 004;
[0030] Step 004: Detect whether the number of consecutive input of the power-on password has reached the preset limited number of times, if not, prompt the user to continue to enter the power-on password and repeat ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com