Remote security monitoring system and method based on android embedded type thin client end
A thin client and embedded technology, applied in the field of electronic information, can solve the problems of high price, inconvenient use, large scale, etc., and achieve the effect of breaking through the complexity of equipment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
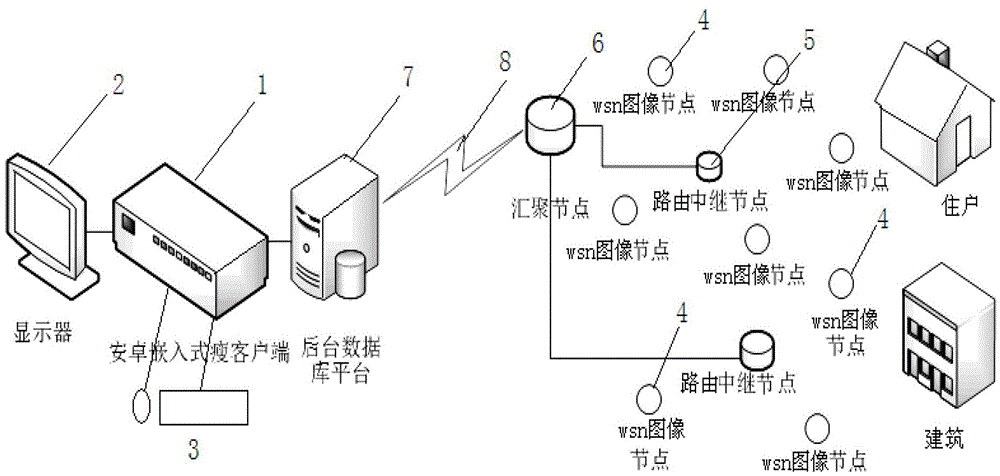
[0030] Embodiment 1 of the present invention such as figure 1 As shown, it includes a thin client 1, a monitor 2, a mouse and keyboard 3, a wsn image node 4, a routing relay node 5, a convergence node 6 and a background database platform 7, and it is characterized in that the wsn image node 4 and the routing relay node 5 Arranged in the area where remote security monitoring is required, the routing relay node 5 is connected to the sink node 6 via radio frequency signals; the sink node 6 is connected to the background database platform 7 via the Internet 8, and the information is uploaded to the background database platform through the sink node 6 7; the thin client 1 is connected with the background database platform 7, and the thin client 1 passes on-demand to the background database platform 7, and the video information of the background database platform is transmitted to the thin client 1 through the Internet 8; the display 2 and the thin client 1 Connect, through the thin...
Embodiment 2
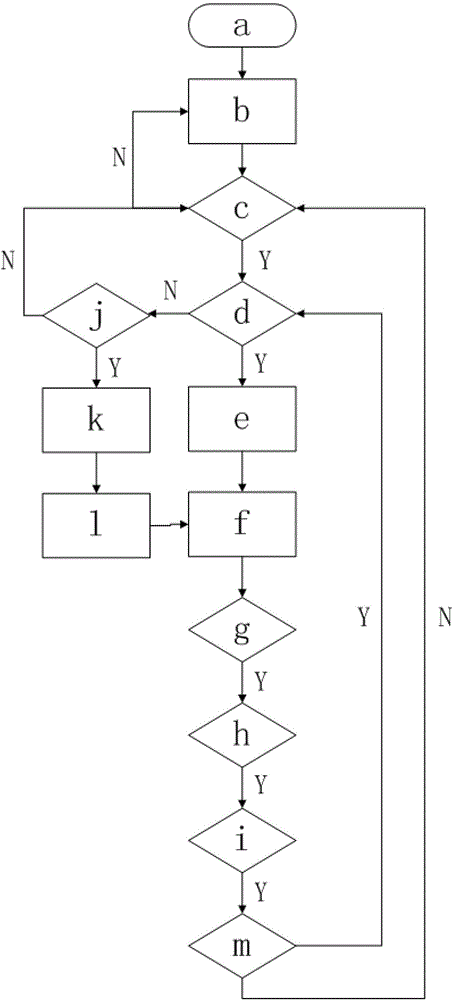
[0033] Such as figure 2 As shown, a method for remote security monitoring using the above monitoring system, the thin client performs on-demand monitoring video through the streaming media RTSP protocol, the on-demand video is compressed into H.264 format, and finally transmitted to the thin client through the RTP protocol end; the video transmitted to the thin client is decoded by the thin client hardware, and the thin client comes with browser software, which is output to the monitor through the thin client image output module in real time for display. The steps of the method are as follows:
[0034] a start;
[0035] b. hardware resource initialization; hardware resources include initialization of each module in wsn image node, routing relay node and aggregation node;
[0036] c. The wsn image node requests to join the system network, if successful, go to the next step, and if not successful, go to step b;
[0037] d. The wsn image node waits for an abnormal signal or us...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com