Method for achieving data center security system based on cloud computation
A cloud data center, data center technology, applied in transmission systems, electrical components, etc., can solve the problems of omissions and losses in protection, complex relationship between applications and hardware, network and operating system, etc., to strengthen security and improve security. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
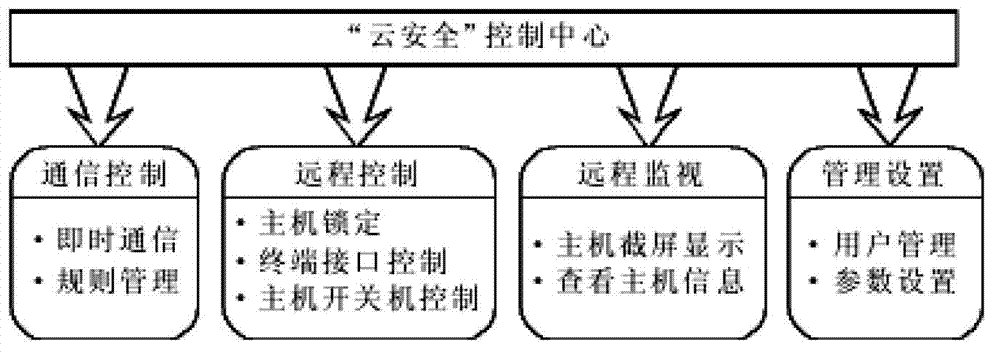
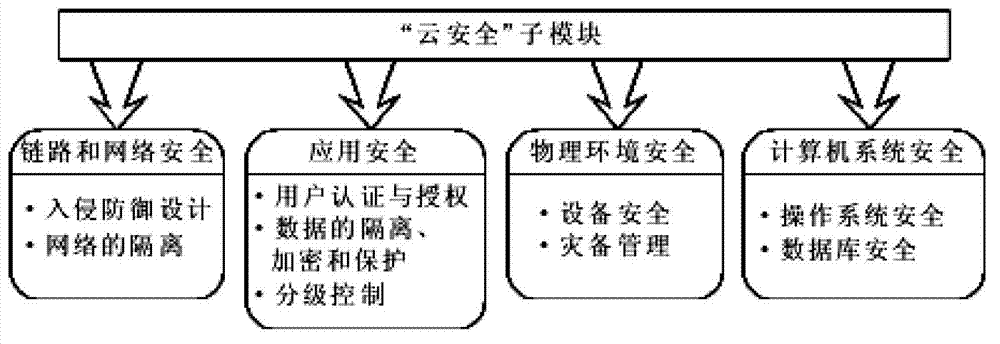
[0026] The realization of the present invention mainly includes the following steps:
[0027] Step 1: Implement the "cloud security" control center: the controlled party runs a program that listens to the port and receives data packets, and the control party sends data packets to the controlled party port through its own port. According to the principle, two systems should be constructed, one is the controlling party "(cloud security" control center), and the other is the controlled party "(cloud security" submodule), the controlled party waits for the controller to send instructions and perform corresponding operations .
[0028] Step 2: Implement WCF communication. First, Client calls Service Request from Client to Service. Service starts to perform the operation. After the operation is completed, Service sends a Callback Request to Client and displays the result on the client side. After the Client completes the Callback Request operation, it will The Service sends a Callback R...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com