Method and system for building multi-source safety relevance
A security association and establishment method technology, applied in the field of multi-source security association establishment methods and systems, can solve the problems of inability to adapt to security backup, low security, high hardware requirements, etc., and achieve the goal of ensuring real-time seamless switching and enhancing security performance Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0053] see image 3 , which is a principle flowchart of the method for establishing a multi-source security association provided in Embodiment 1 of the present invention, specifically as follows:
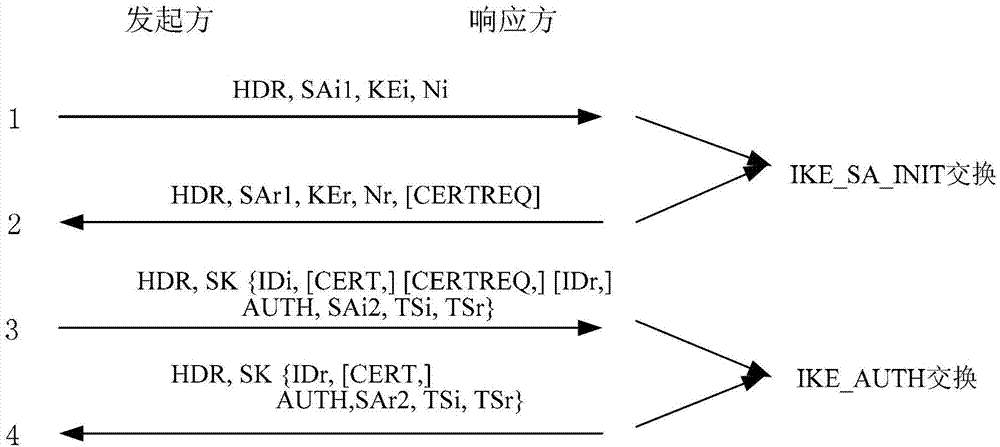
[0054] Step 10, in IKEv2 communication, during the IKE_AUTH message negotiation process, the gateway sends a message carrying flag payload Hai, advertisement payload N[IPi] and N traffic selector payloads TS2i.
[0055] This embodiment is essentially a scheme for establishing a multi-source security association based on IKEv2, and it is necessary to expand and modify the third and fourth messages of IKEv2, that is, it is necessary to extend the negotiation process of the IKE_AUTH message. The sender (gateway) adds at least HAi load, N[IPi] load and N TS2i loads to the third message, where N is a natural number greater than 1. Among them, HAi is a payload of flags, which is used to confirm that this sent message carries multi-source security association information. In addition to ...
Embodiment 2
[0073] The embodiment of the present invention provides a specific method for establishing a multi-source security association, see Figure 6 ,details as follows:
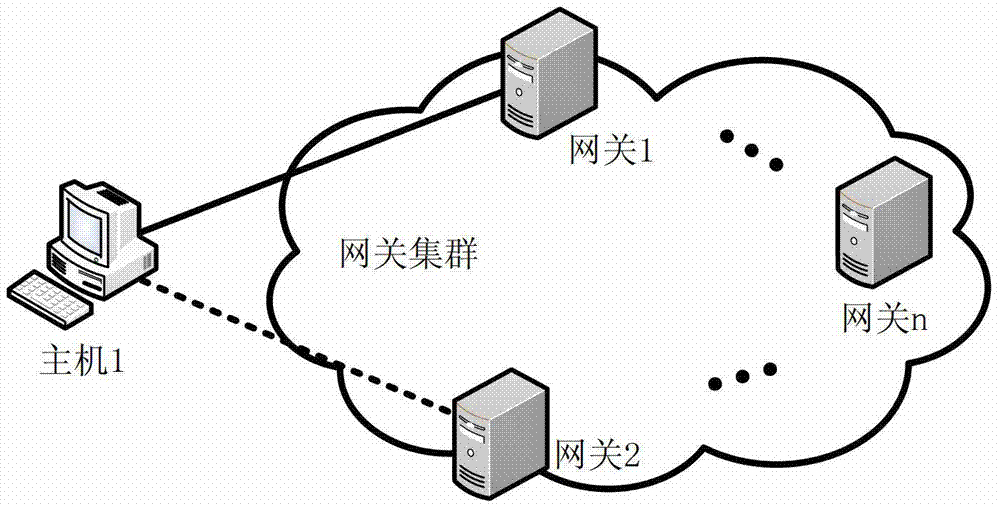
[0074] Host 1, gateway 1 and gateway 2 form the system, gateway 1 is the main gateway, and gateway 2 is the backup gateway. IKE negotiation is performed between gateway 1 and host 1. Gateway 2 is a trusted host and uses a fixed IP. Gateway 1 can directly send authentication information to gateway 2. If gateway 2 is untrustworthy, gateway 1 sends encrypted authentication information to gateway 2. The encryption algorithm can use existing encryption algorithms, such as signature Algorithm and so on one or more. The specific implementation includes the following steps:
[0075] When gateway 1 sends the third message to host 1, in addition to the identity of gateway 1, identity information such as the IP address of gateway 2 is also included. Wherein, the gateway 2 may select one or more hosts. In addition to send...
Embodiment 3
[0091] see Figure 9 , the embodiment of the present invention provides a multi-source security association establishment system, the system includes a terminal, a gateway and at least one backup gateway, specifically as follows:
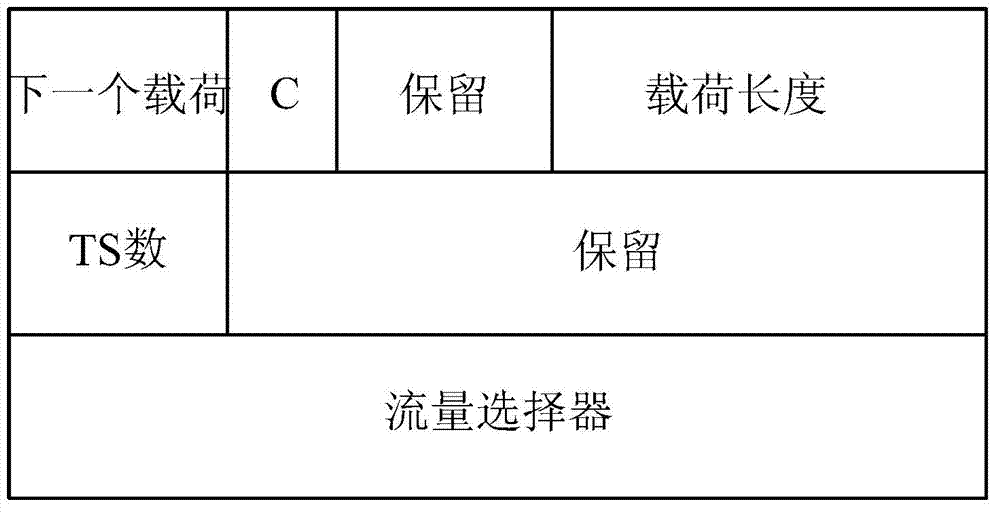
[0092] The gateway is used to carry flag payload Hai, notification payload N[IPi], and N traffic selector payloads TS2i in the sent message; among them, the flag payload Hai is used to confirm that this sent message carries multi-source security association information; N is backup The number of gateways; N[IPi] is the IP address of the backup gateway; TS2i is the traffic protected by each backup gateway.
[0093] The terminal is used to carry the flag bit confirmation payload HAr and N traffic selector payloads TSr in the return message; wherein, the flag bit confirmation payload HAr is used to identify the terminal to confirm the establishment of a multi-source security association; the N traffic selector payloads TSr correspond to receiving The ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com