Identity authentication method based on Web user behavior model
An identity authentication and user technology, applied in the field of identity authentication, can solve problems such as account theft, and achieve the effect of improving accuracy and ensuring property safety.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0014] The technology will be further described below in conjunction with the accompanying drawings and examples.
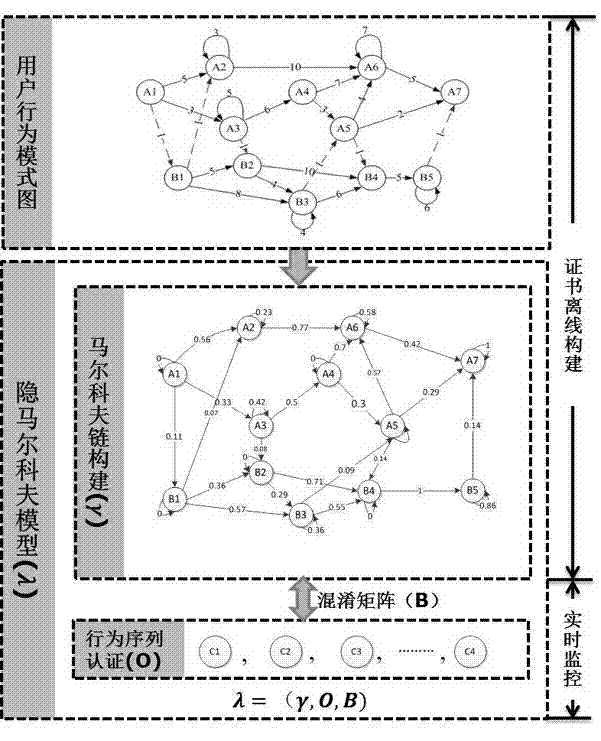
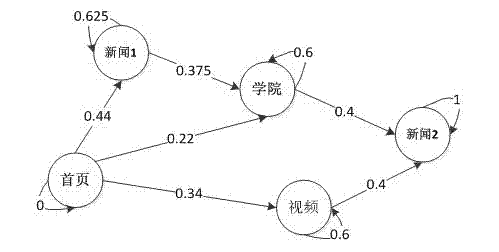
[0015] figure 1 The overall construction process and operating mechanism of the method of the present invention are shown. It mainly includes two stages: offline and online; the work in the offline stage includes user behavior pattern mining and construction, Markov model construction, and generation of confusion probability matrix. The online stage mainly includes observation sequence implementation monitoring and Web user behavior authentication process. the following Figure 2-Figure 4 The implementation details of each part of the technology of the present invention are described separately.
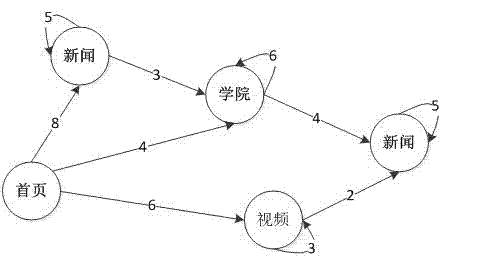
[0016] figure 2 is the constructed user behavior pattern diagram, and the construction process has the following steps:
[0017] Step 1 is a data mining process; collect web page browsing records of web users for at least 30 days, and obtain the order of web page ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com