Method and device for executing commands, intelligent card and mobile terminal
A mobile terminal and command execution technology, applied in the protection of internal/peripheral computer components, digital data authentication, etc., can solve problems such as unusable, USBKey and data card loss, waste of PC port resources, etc., to achieve high practicability and energy saving The effect of excellent resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
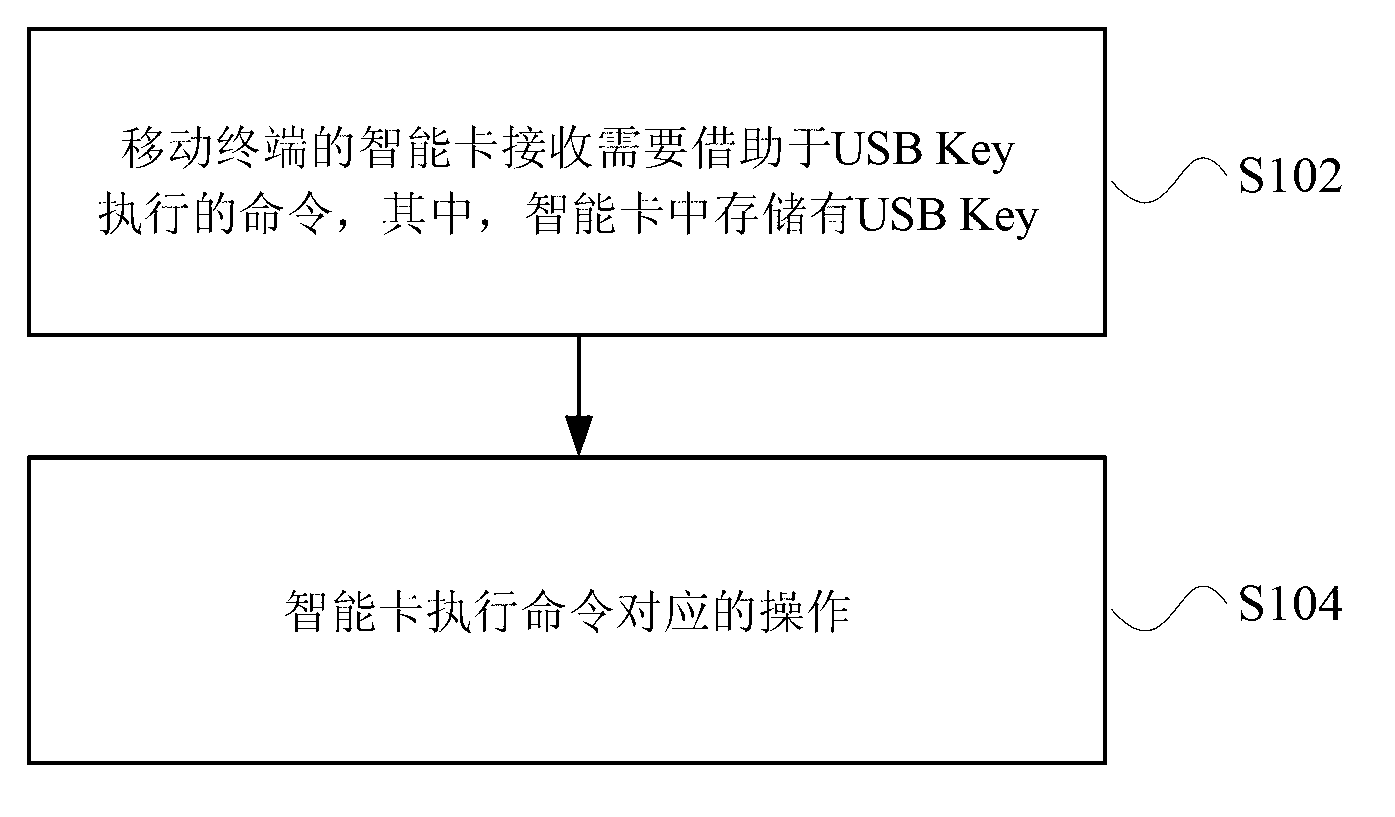
[0046] Based on the problem that the USB Key and the data card are usually separated in the related art and need to occupy two USB sockets, this embodiment implants the encryption and decryption functions of the existing USB Key into the SIM card, that is, the encryption and decryption process is performed by the SIM card. Finish. As a bridge between the USB Key function operation interface and the SIM card, the data card is responsible for analyzing and transmitting encrypted and decrypted data.
[0047] The modules involved in this embodiment include: a SIM card, a data card driver module, a data card Application Protocol Data Unit (Application Protocol Data Unit, APDU for short) processing module, and a user operation interface. The method provided in this embodiment includes the following processes.
[0048] The user operates on the USB Key PC operation interface and issues related commands, such as encryption, decryption, and key pair generation.
[0049] The data card ...
Embodiment 2
[0053] This embodiment relates to a system with a USB Key function and a method for implementing an interaction process based on the system. In this embodiment, the operation requirements of the user interface are analyzed by the data card side driver module, and the software module inside the data card is converted into an APDU string that can be recognized by the corresponding SIM card, and the APDU command is sent to the SIM card, and the process is performed inside the SIM card. Encryption and decryption of data, and return the execution result. Through the cooperative use of the SIM card and the data card, it has a USB Key function.
[0054] A SIM card is a smart card containing a large-scale integrated circuit, which is used to register user identification data and information. APDU is an instruction for interaction between the terminal and the SIM card. In order to enable the SIM card to have the USB Key function, it is first necessary to create a new application insi...
Embodiment 3
[0075] Combining the data card and USB Key into one has gradually become the customization requirement of this part of users. The integrated mobile terminal provided by this embodiment can save the USB interface of the PC, and the encryption and decryption functions of the USB Key can be completed inside the SIM card, and only the internal software of the SIM card needs to be modified when designing the SIM card. In this way, the hardware cost of the original USBKey can be saved; the SIM card itself has a PIN1, PIN2 code protection mechanism, which further enhances the security of USB Key-related operations; It provides security support and can also be applied to other scenarios that require the use of USB Keys, thereby bringing more convenient, secure and efficient services to users.
[0076] The system architecture of this embodiment can be as follows Figure 5 As shown, the execution process can be as follows Figure 7 As shown, the flow shows the specific implementation ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com