Protecting and tracking method for primary information of mobile terminal based on user behavior pattern
A mobile terminal, privacy protection technology, applied in the direction of digital data protection, protection of storage content to prevent loss, prevention of unauthorized use of memory, etc., to achieve ideal user experience, low energy consumption, and simple technology.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
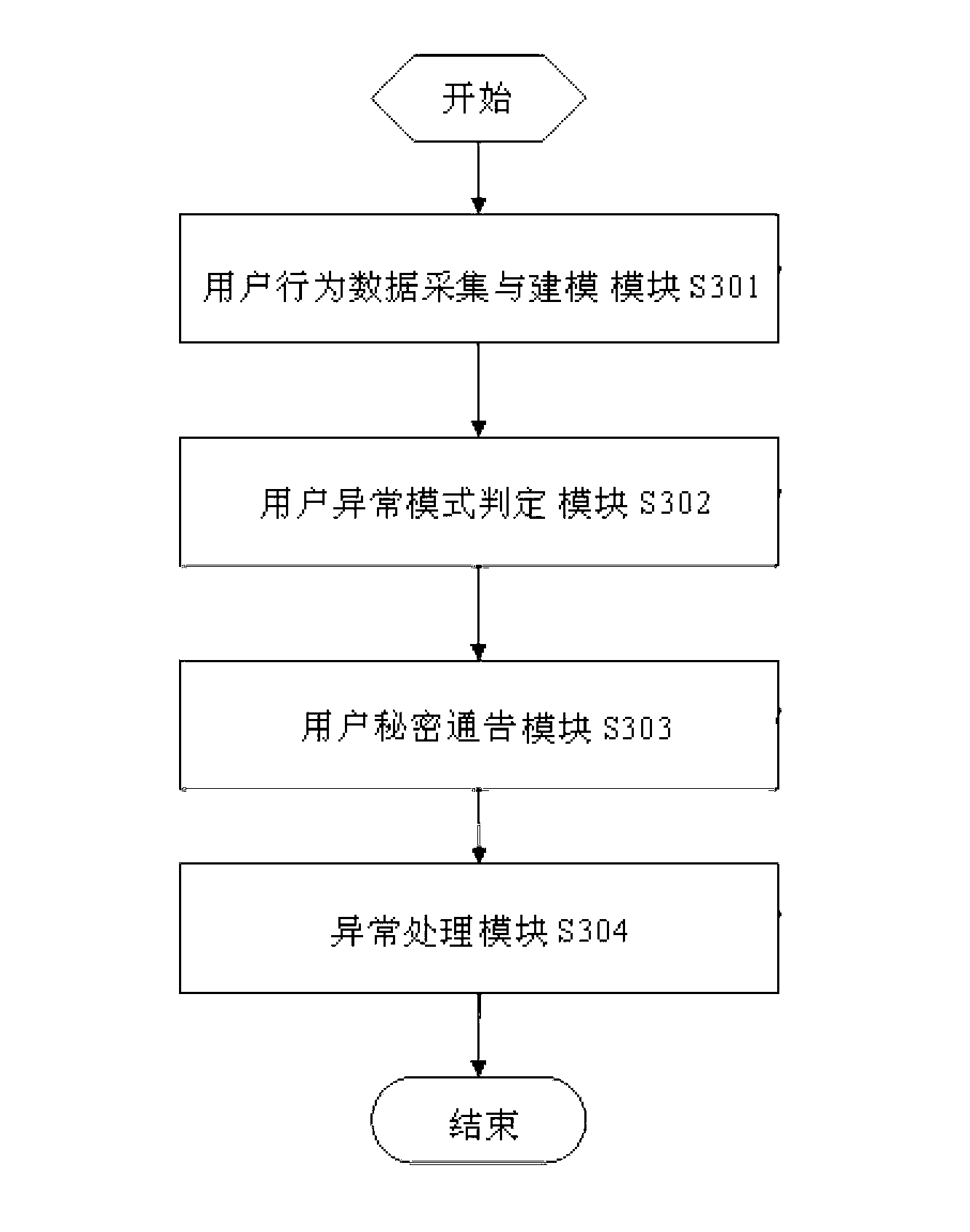
[0049] Embodiment 1: The present invention provides a mobile terminal privacy protection and tracking method based on user behavior patterns. Now taking a user A as an example, the steps of the user mobile terminal privacy protection and tracking method are as follows: figure 1 Shown:
[0050] (1) Firstly, the user A behavior data collection and modeling stage is carried out, the user A behavior data collection and establishment module S301A, this module collects the user's behavior pattern, quantifies the user's behavior pattern, and generates these behavior data Statistical results, build user behavior pattern library;
[0051] Assuming that a sampling period is 24 hours, through self-learning of 30 sampling periods (that is, 30 days), the user behavior data collection and modeling stage is carried out. User behavior data collection takes three aspects of behavior patterns, such as the time of using the application Patterns, patterns of frequency of use of applications, pat...
Embodiment 2
[0082] Embodiment 2: The present invention provides a mobile terminal privacy protection and tracking method based on user behavior patterns. Now take a user B as an example, and the steps are as follows:
[0083] (1) Firstly, the user B behavior data collection and modeling stage is carried out, the user B behavior data collection and establishment module S301B, this module collects the user's behavior pattern, quantifies the user's behavior pattern, and generates these behavior data Statistical results, build user behavior pattern library;
[0084] Assuming that a sampling period is 24 hours, through self-study of 60 sampling periods (that is, 60 days), the user behavior data collection and modeling stage is carried out. User behavior data collection takes two aspects of behavior patterns, such as browsing behavior patterns, phone calls Behavioral patterns.
[0085] Usually, the user's browsing behavior in the mobile terminal has fixed characteristics, showing that he likes t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com