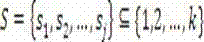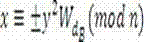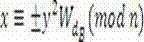Ad Hoc network key management method
A management method and network key technology, which are applied in the field of Ad Hoc network key management, can solve the problem that the key management scheme is no longer applicable, and achieve the effects of high reliability, low communication volume and strong robustness.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0023] An Ad Hoc network key management method, through the identity recognition protocol, that is, the prover P does not reveal his secret identity, nor does he prove to V the legitimacy of P's public identity, but by showing that V has P's secret knowledge of the identity, thus proving that V knows P's secret identity and the legitimacy of his public identity.
[0024] Wherein, the described identity recognition protocol is secretly selected by a trustworthy center in the form of 4r+3 two large prime numbers of p , q , making n=pq is computationally difficult to decompose, and then publish n Modulo all users, P's secret identity is given by k Number c 1 ,c 2 ,…,c k Composition, P's public identity is d 1 ,d 2 ,…,d k , k ,and , , in the initial state, V knows the public n and P's public identity , now P wants to prove to V that P knows his secret identity without revealing his secret identity information, perform the following steps:
[0025] 1. P ra...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com