Method and device for deleting Child SAs
A technology of equipment and peer equipment, which is applied in the field of communication and can solve problems such as deletion errors
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
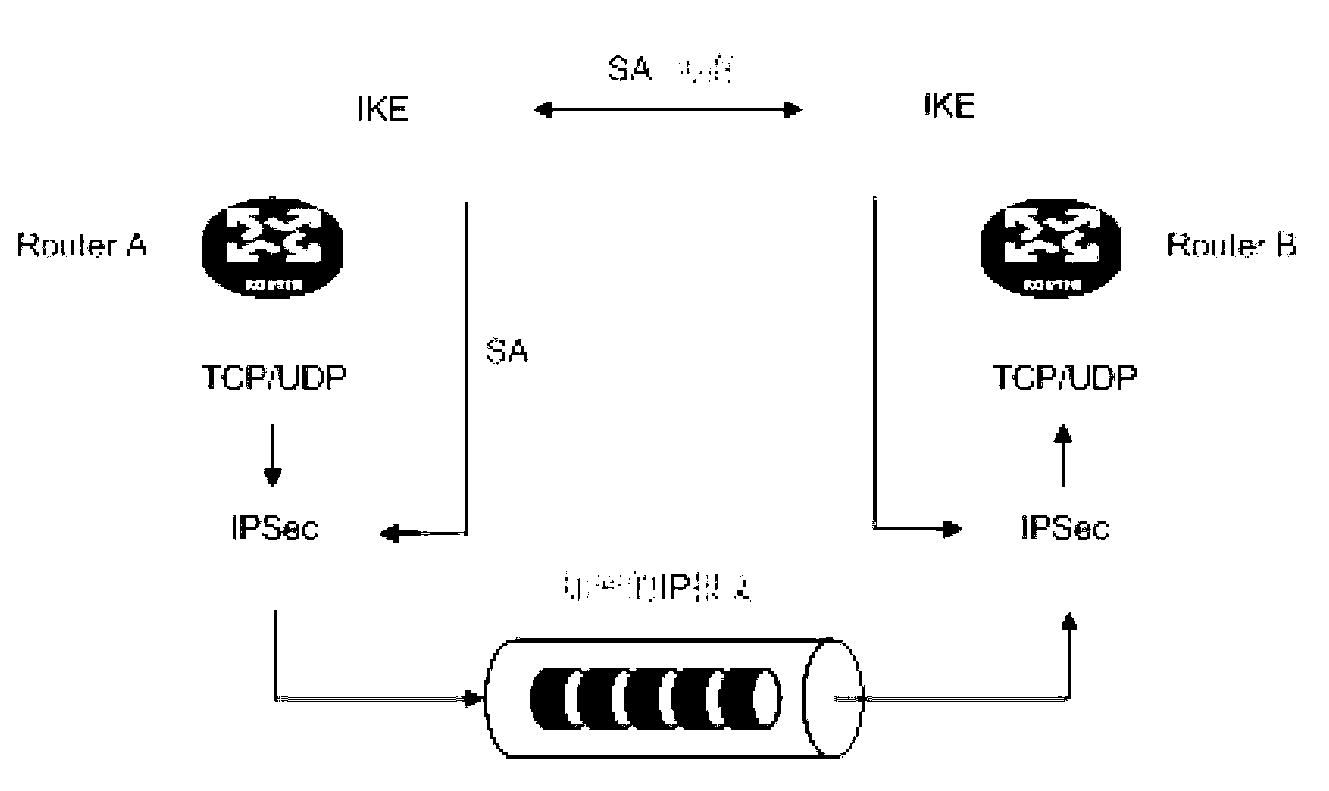
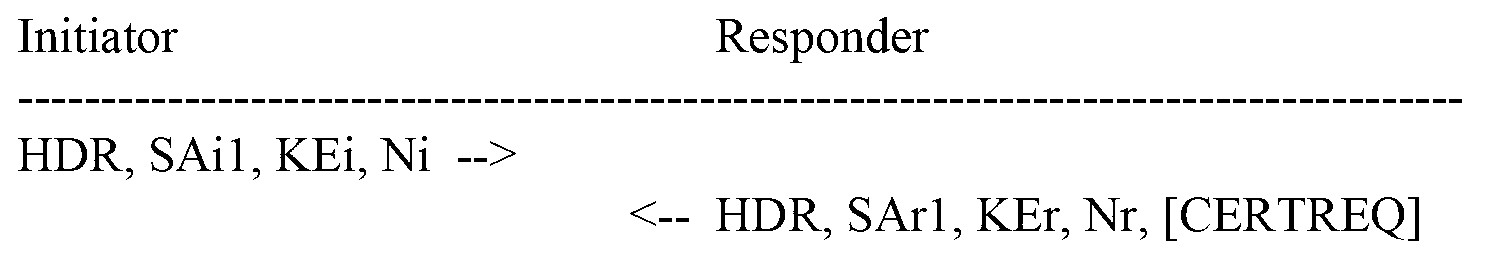
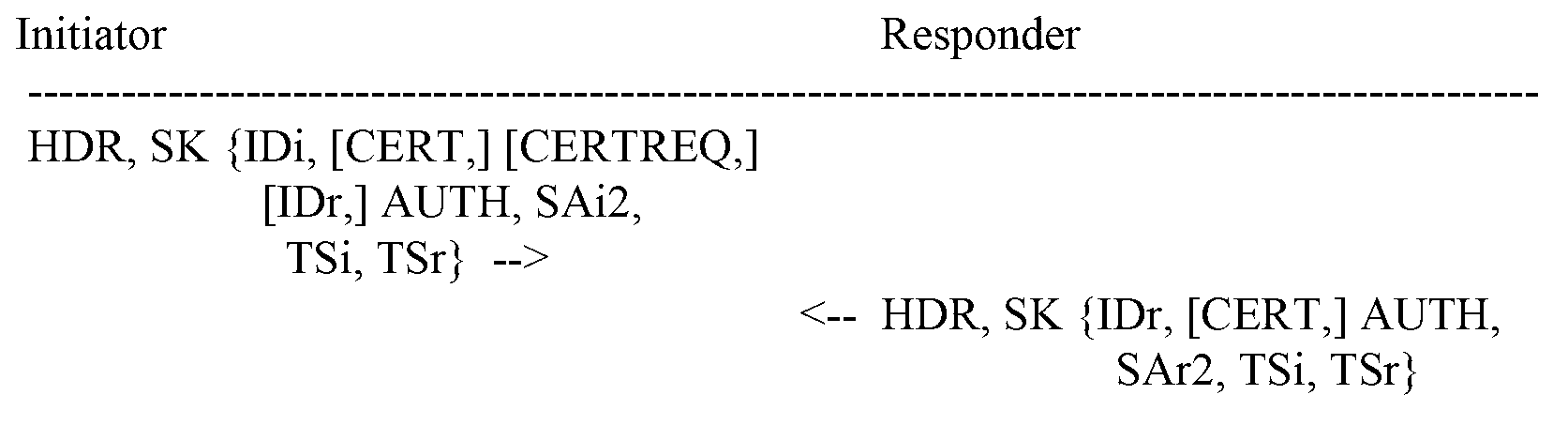
[0058] Aiming at the above-mentioned problems existing in the prior art, the embodiment of the present invention provides a technical solution of Child SA deletion. In this technical solution, when a device needs to delete a Child SA, the device sets the outbound direction Child SA corresponding to the Child SA to be deleted as unavailable, and sends a message carrying the SPI and security protocol of the Child SA to be deleted to the peer device. Delete message; when the device receives the delete response message returned by the peer device, the device deletes the Child SA to be deleted and the outbound Child SA corresponding to the Child SA to be deleted.
[0059] Among them, when the peer device receives the delete message, it can query the corresponding Child SA (outgoing Child SA) according to the SPI and security protocol carried in the delete message, and query the inbound Child SA corresponding to the Child SA, and delete the query to the Child SA (including the outbo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com