Method and system for sharing network disk data
A data and network disk technology, applied in the Internet field, can solve problems such as user inconvenience, and achieve the effect of reducing the difficulty of operation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
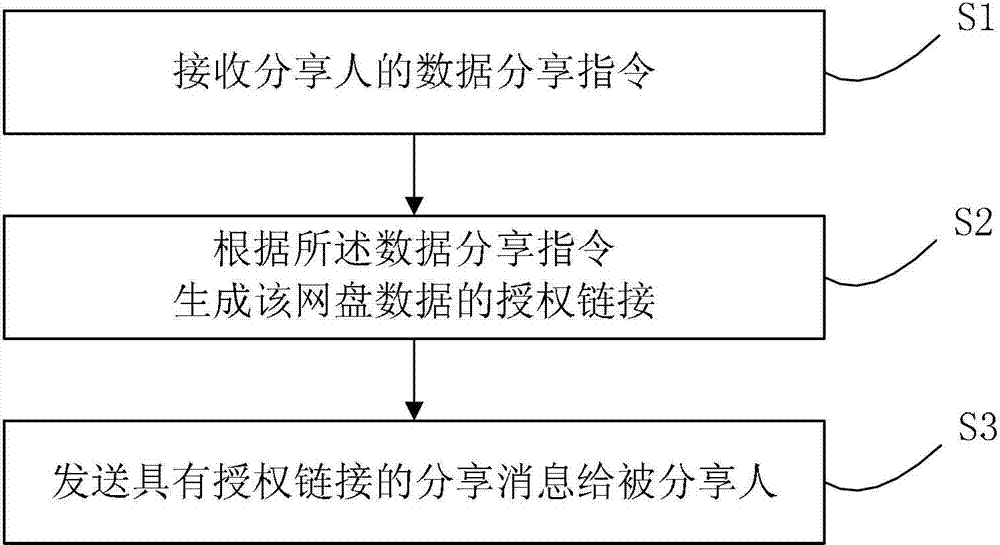
[0080] figure 1 It is a flow chart of the sending method of shared network disk data. Such as figure 1 As shown, when the sharer needs to share the network disk data to the shareee, the method of sending the shared network disk data includes:
[0081] S1. Receive a data sharing instruction from the sharer; the data sharing instruction at least includes the data information of the shared network disk;
[0082] The shared network disk data information includes at least the network address of the network disk data. In addition, the shared network disk data information may also include: network disk data name, creator information, etc., so that the shared person can clearly understand the relevant information of the shared network disk data.
[0083] S2. Generate an authorization link of the network disk data according to the data sharing instruction; the authorization link is used to verify the authorization of the network disk data;
[0084] Here, the authorization link is d...
Embodiment 2
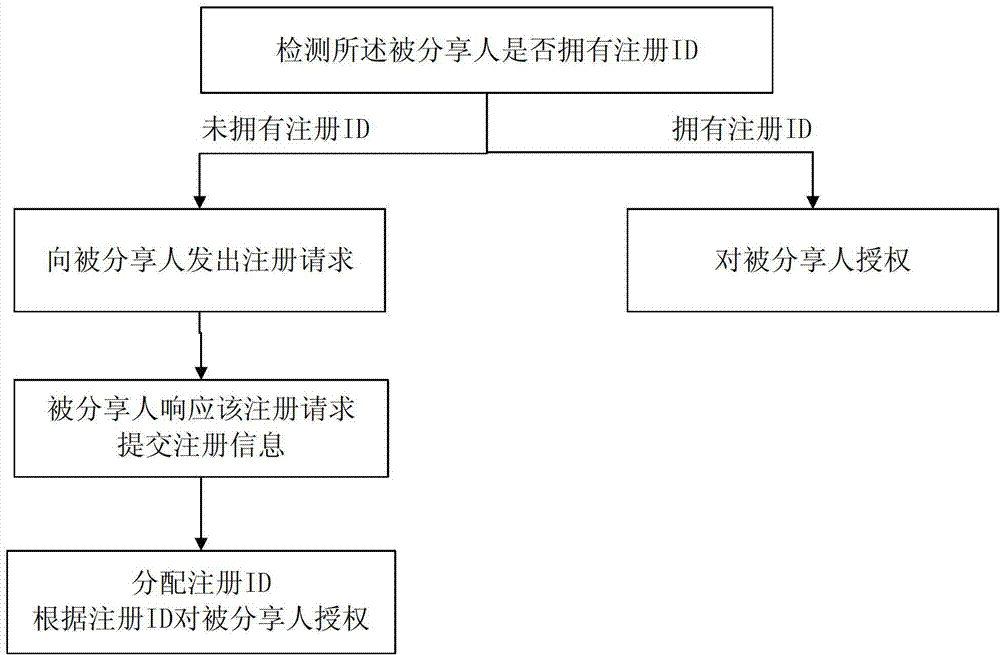
[0088] Based on the aforementioned design of setting access rights list for network disk data, we can assign different access rights to different users in the access rights list. For example, a read-only user can only read the data of the network disk but cannot modify the data of the network disk; a read-write user can read and modify the data of the network disk; In addition to user functions, it can also add, delete, and manage users in the access list. Based on this, the sharer can also set the access rights of the shareee while sharing the network disk data.
[0089] In the step of receiving the data sharing instruction from the sharer, the data sharing instruction further includes: authorization authority information; the authorization authority information is the access authority authorized by the sharer.
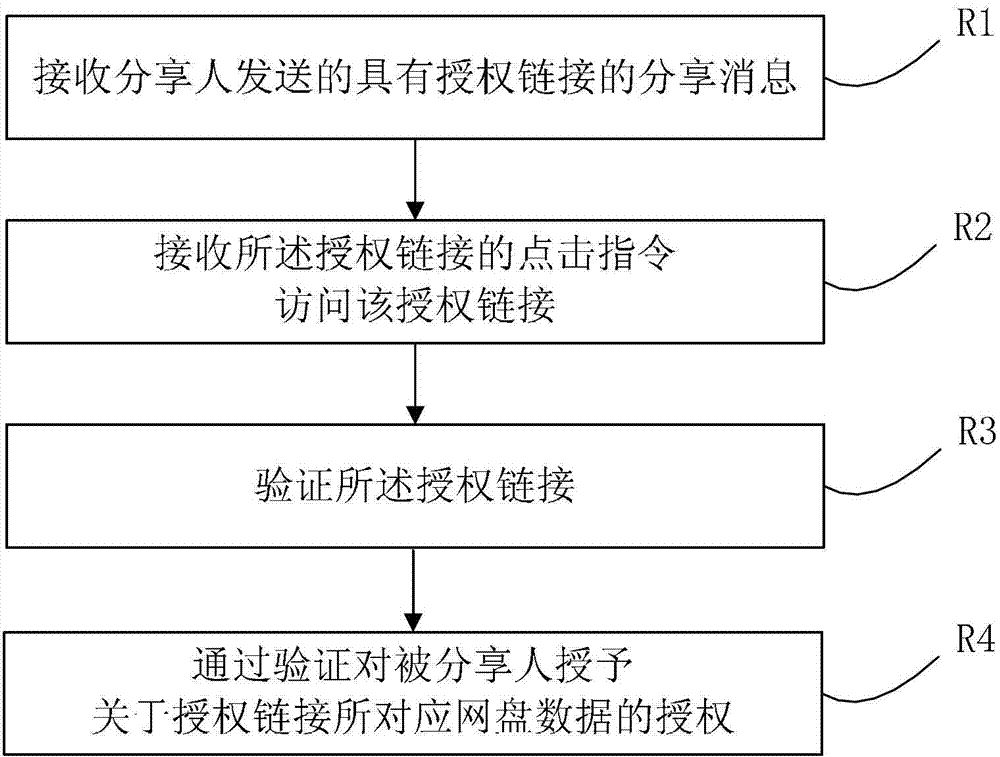
[0090] In step S2, a corresponding authorization link is generated according to the authorization authority information in the data sharing instruction. When the s...
Embodiment 3
[0094] In this embodiment, we further provide sharers with a management solution for the timeliness of the generated authorization links.
[0095] In the step of receiving the data sharing instruction from the sharer, the data sharing instruction further includes: authorization link expiration information; the authorization link expiration information is used to limit the expiration date of the generated authorization link.
[0096] The authorization link expiration information may limit the validity period of the generated authorization link. The shareee who clicks on the authorization link within the validity period can obtain the corresponding access authorization, and will no longer be authorized beyond the validity period.
[0097] The authorization link aging information may also limit the authorization times of the generated authorization link. The generated authorization link can only be used for a limited number of authorized sharers to obtain the corresponding acces...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com