Method for rapidly inputting and discovering hidden danger of underground coal mine
A technology for hidden dangers and coal mines, which is applied in the field of information management of underground safety, can solve the problems of inability to collect hidden dangers, slow entry speed, delayed processing speed of hidden dangers, etc., and achieve the effect of shortening the entry of hidden dangers.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] The present invention will be further described below in conjunction with the accompanying drawings, but the present invention is not limited to the scope of the described embodiments.
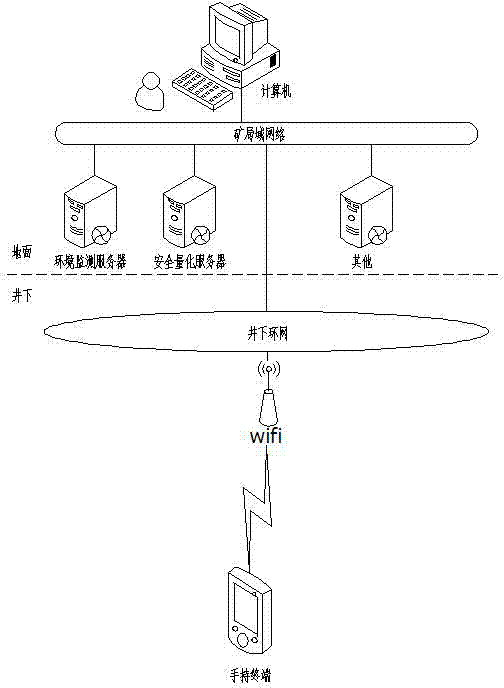
[0036] Such as figure 1 As shown, a hidden danger management system for coal mine safety production includes multiple servers such as a ground computer host, an environmental monitoring server, a security quantification server, and other servers, as well as a handheld terminal for underground inspection, and a local area network is constructed between the computer host and the multiple servers; A Wifi communication ring network is built underground to realize network connection with the local area network, and the handheld terminal can realize data transmission through the Wifi communication ring network and the local area network; the management system can automatically enter the hidden danger treatment management process based on the inspection results.
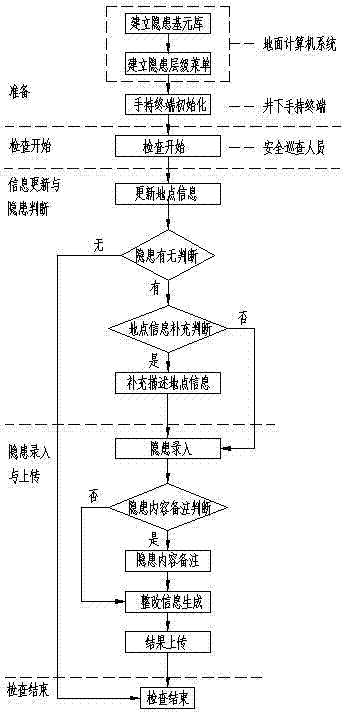
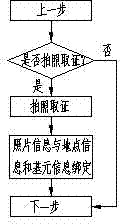
[0037] Such as figure 2 wi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com