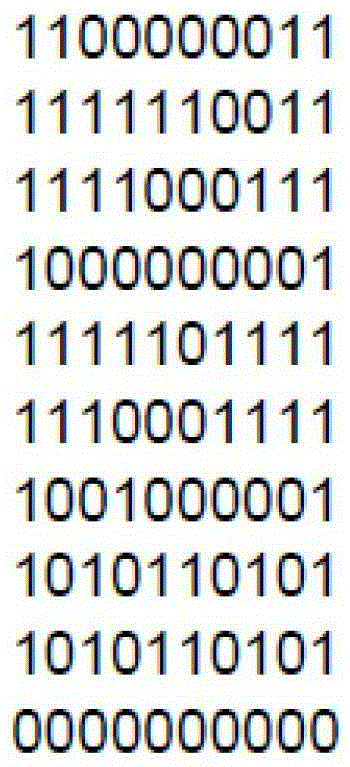Embedding and Extraction Method of Digital Watermark in Text Document
A text document, digital watermarking technology, applied in the direction of digital data protection, program/content distribution protection, etc., can solve the problems of insufficient confidentiality, not easy to delete, easy to break the defense line, etc., to improve security, enhance confidentiality, Good crime prevention effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] The specific steps of the present invention are described below according to the drawings.
[0021] The specific steps of the present invention are as follows:
[0022] ⑴ Make watermark:
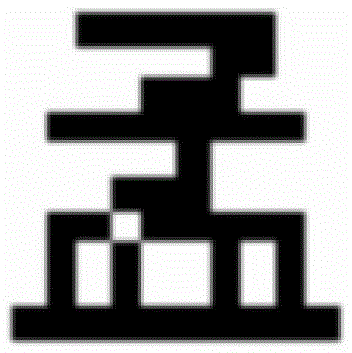
[0023] Use general drawing tool software (such as photoshop, drawing board in windows attachment, etc.) to make the original information into a binary image, such as figure 1 As shown (the binary image can be a binary image, bitmap image or GRB, etc.), then use matlab, C, C++ language programming software to read the binary image, and get a one-to-one correspondence with the binary image "01" matrix, such as figure 2 As shown, the "01" matrix is used as watermark information.
[0024] ⑵Generate watermark key: Write the two binary code characters "0" and "1" into the font library of the TrueType word-making program, and generate the key; the specific operation of this step can be found in Chinese Patent ZL201110396024.X The first step.
[0025] ⑶Watermark embedding: open a image 3 As shown...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com