Method and system for protecting software authorization
A software authorization, software technology, applied in the direction of program/content distribution protection, digital data authentication, instruments, etc., can solve problems such as negative impact
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
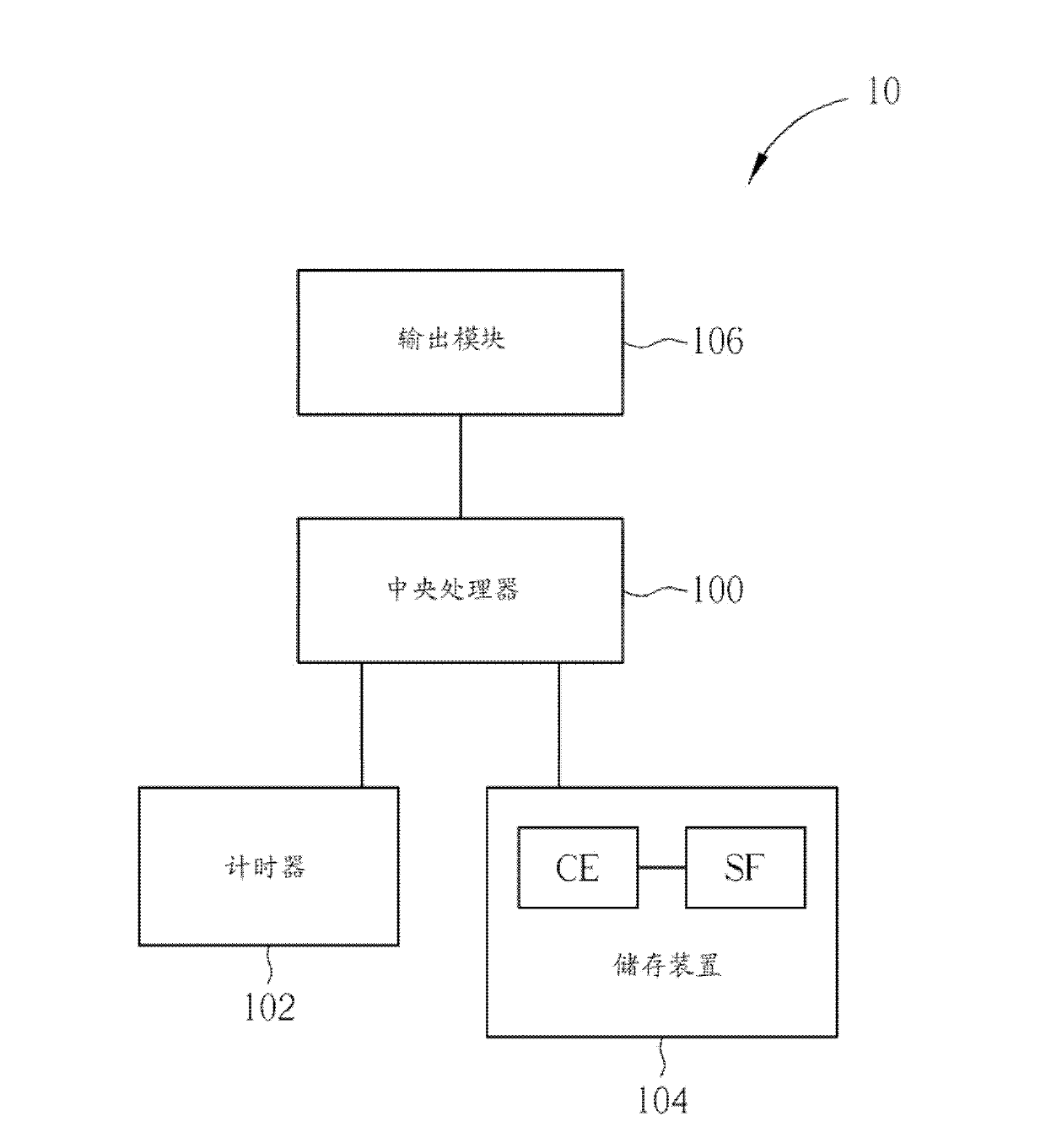
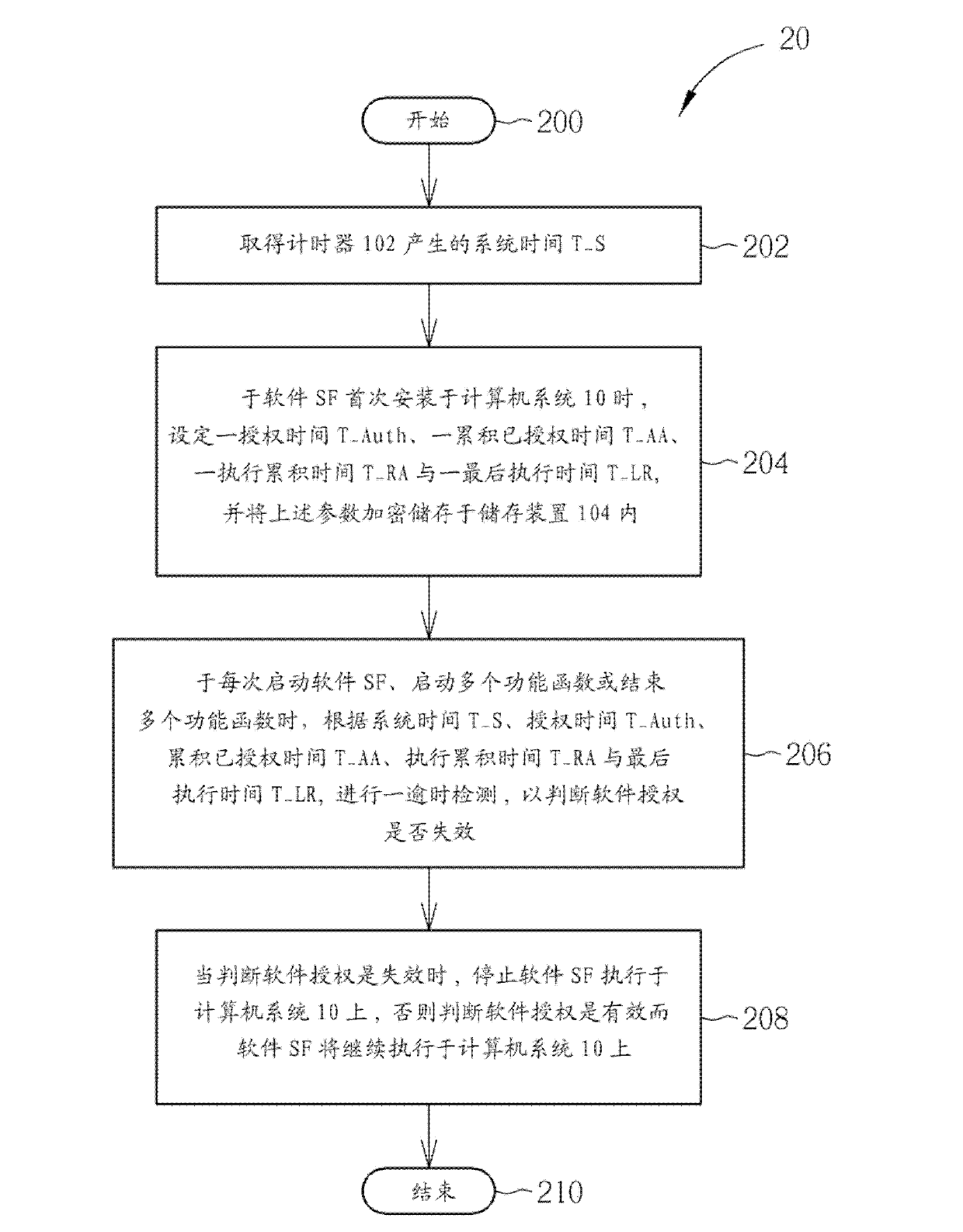
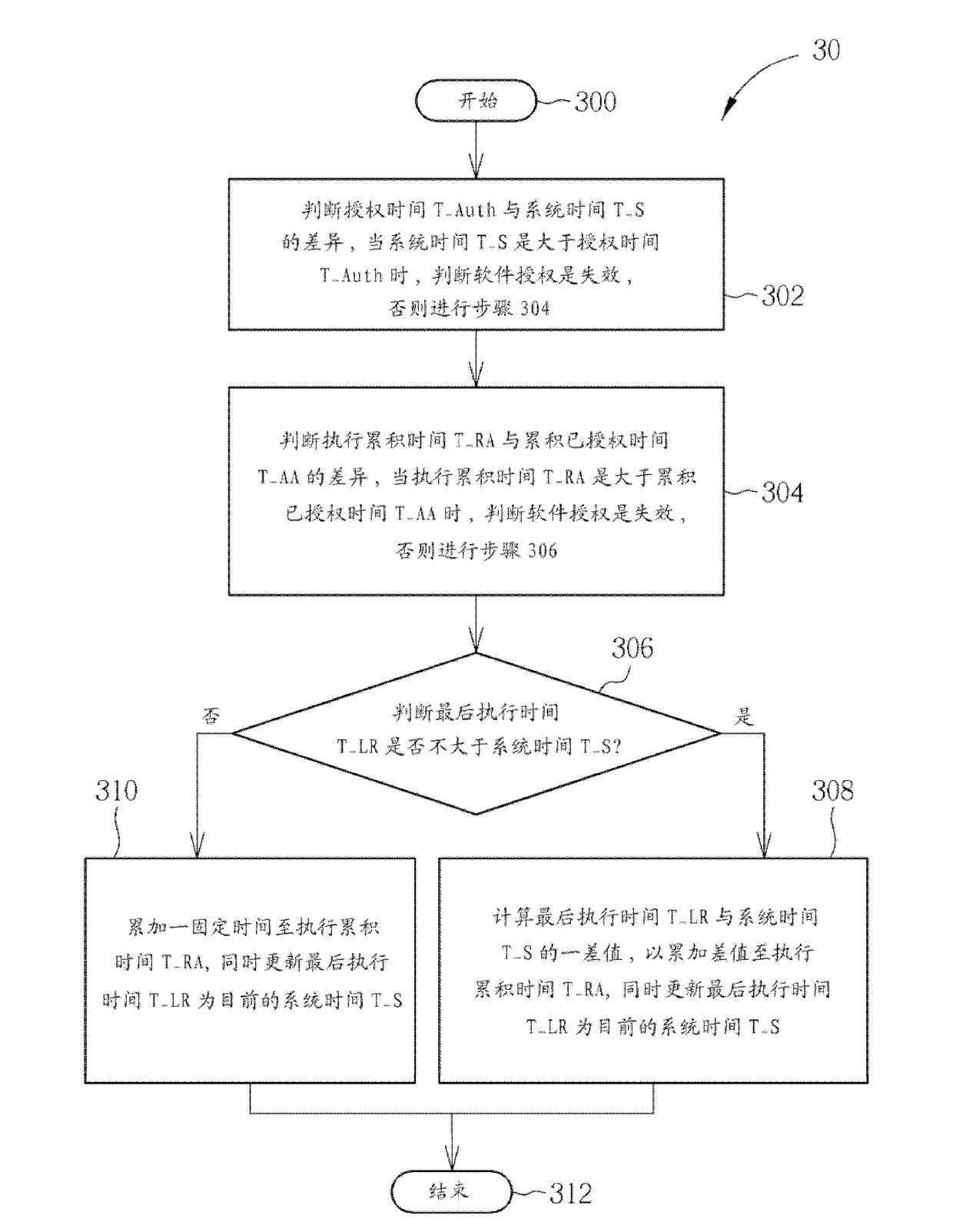
[0020] Please refer to figure 1 , figure 1 It is a schematic diagram of a computer system 10 that can protect a software license according to the present invention. Such as figure 1 As shown, the computer system 10 includes a CPU 100 , a timer 102 , a storage device 104 and an output module 106 . The timer 102 is used to generate a system time, and the system time is synchronized with the GMT in different regions, and correspondingly input to the CPU 100 . The storage device 104 correspondingly stores at least one software SF and one program code CE according to different requirements of users. The program code CE is used to instruct the central processing unit 100 to execute various operations of the computer system 10, which includes a software authorization process for executing the protection software SF, as for the software SF, a timeout detection process is performed under the protection of the software authorization process, and The operations of the software SF and...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com