PEACH platform extension method for GUI-based protocol state machine modeling
A protocol state and state machine technology, applied in the computer field, can solve problems such as error-prone, unintuitive protocol state machine, increased workload, etc., to reduce the difficulty, avoid trivial details, and facilitate the implementation of operations.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
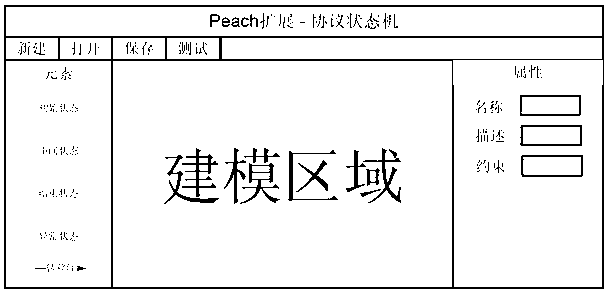
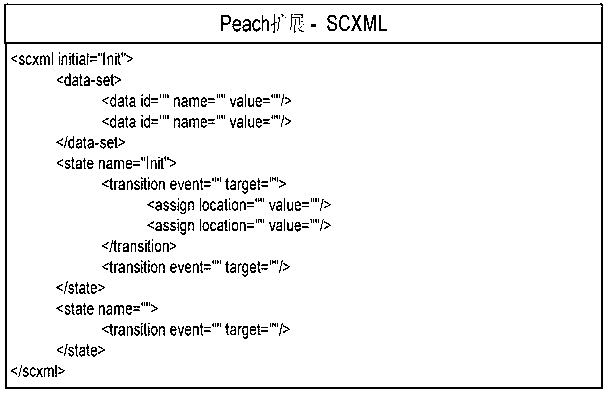
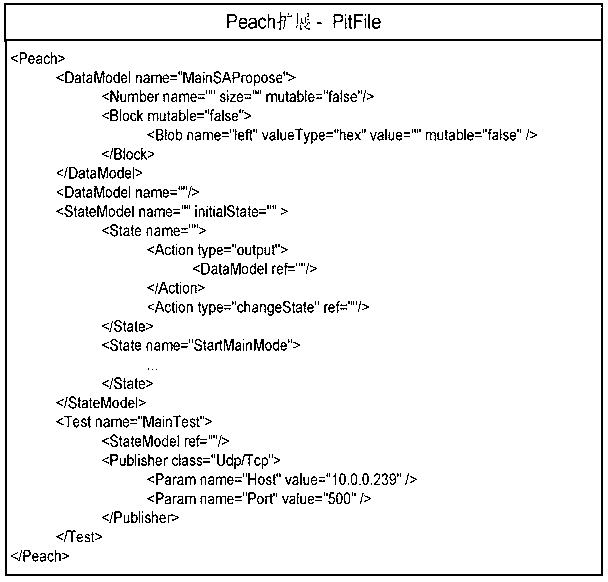
[0021] In order to clearly illustrate the technical solution of the present invention, specific usage examples are given below and detailed descriptions are given in conjunction with the accompanying drawings.
[0022] The present invention assumes that the protocol state transitions are definite, that is, definite input or output messages correspond to definite state transitions, and there is no probability jump problem between states. Here, take the ISAKMP (Internet Security Association and Key Management Protocol) protocol as an example to illustrate the specific usage steps of the present invention:
[0023] Step 1: Refer to the ISAKMP protocol specification and build a corresponding test environment so that network entities can communicate normally based on the ISAKMP protocol.
[0024] Step 2: When the network entity is in normal communication, use wireshark to capture its communication traffic, and save each message as a file in xml format. For specific format s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com