Public audit design method for multi-write model of cloud data security
A design method and multi-writing technology, applied in the field of cloud computing security, can solve problems such as high communication costs, weak credibility, and unsupported auditing, and achieve the effect of reducing computing costs and communication costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
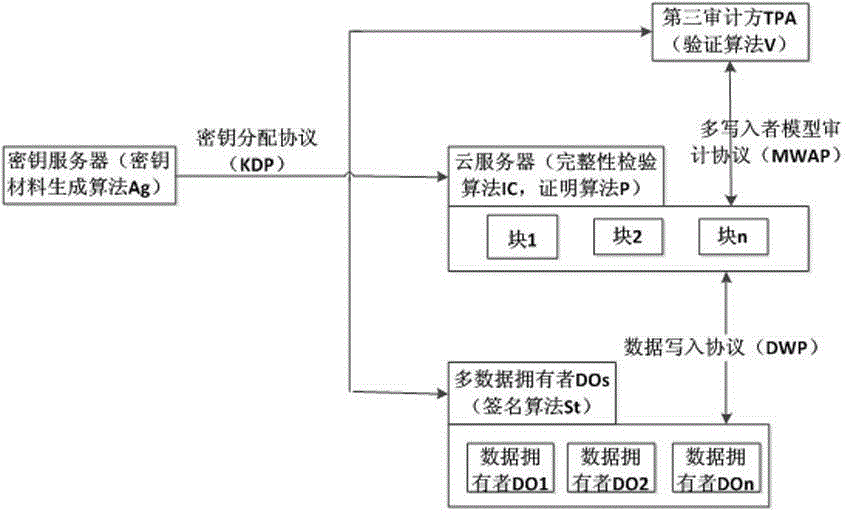
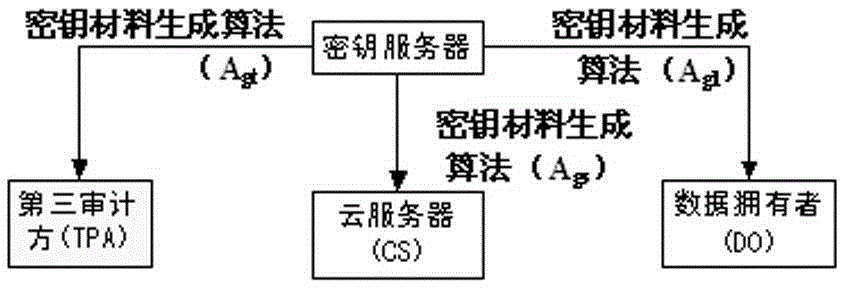
[0047] This embodiment is designed to complete key distribution. The purpose of the key distribution is to distribute respective key materials to the cloud server CS, the third auditor TPA and the data owner DO. Including but not limited to the following steps (expressed in a table):
[0048] step content 100 The key server constructs an elliptic curve and Lagrangian interpolation function, and generates authentication and audit keys from the parameters of the elliptic curve. 102 The key server calculates the key material corresponding to the data owner DO according to the Lagrangian interpolation function, and distributes it to the data owner DO. 104 The key server calculates the key material corresponding to the cloud server CS according to the Lagrangian interpolation function, and distributes it to the data owner cloud server CS. 106 The key server distributes the key material corresponding to the third auditor TPA to the TPA.
...
Embodiment 2
[0056] The design of this embodiment completes the data writing stage. The purpose of this stage is: the data owner DO signs the data block and verifies the integrity of the signature. Including but not limited to the following steps (expressed in a table):
[0057] step content 108 The data owner DO signs the data block and sends the signature result and related data to the cloud server CS. 110 The cloud server CS checks the validity of the signature through an integrity check algorithm, thereby deciding whether the cloud server CS stores the data.
[0058] The protocol flow of this embodiment is as follows Figure 4 shown.
[0059] The steps and the protocol flowchart in Embodiment 2 are described as follows:
[0060] (1) Step 108: When a certain data owner ( is a collection of all data owners, represents an element in the collection) to give the block ( Represents the set of all data blocks) when signing (if the signature is ),...
Embodiment 3
[0063] This embodiment is designed to complete the multi-write model audit stage. The purpose of this stage is: to realize the audit of the shared data block set on the cloud server CS by the third auditor TPA. Including but not limited to the following steps (expressed in a table):
[0064] step content 112 The third auditor TPA selects a set of flag data and sends it to the cloud server CS. 114 After receiving the flag data, the cloud server CS uses the proof algorithm to generate Sent to the third auditor TPA. 116 The third auditing party TPA audits the data written by multiple data owners DOs using the verification algorithm.
[0065] The protocol flow of this embodiment is as follows Figure 5 shown.
[0066] The steps in Embodiment 3 and the protocol flow chart are described as follows:
[0067] (1) Step 112: When the third auditor TPA wants to audit the data written by multiple data owners DOs, he selects a set of appropriate f...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com