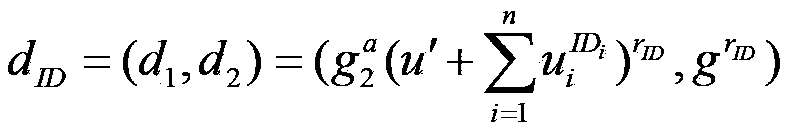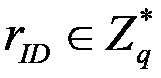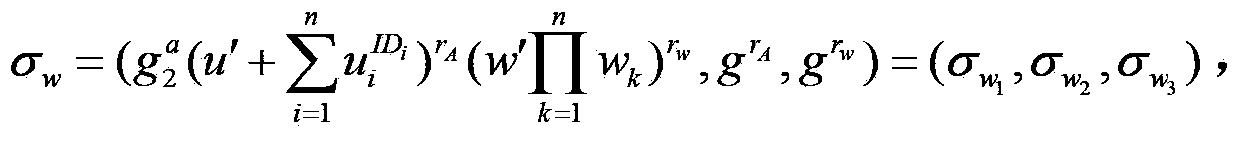Sanitizable agent signature method in standard model
A proxy signature, standard model technology, used in electrical components, user identity/authority verification, transmission systems, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0043] A purifiable proxy signature method of the present invention under the standard model, the method is implemented according to the following steps:
[0044] Step 1. System Setup
[0045] 1) Let user ID, authorization certificate W and message M be a bit string of length n, where n is a natural number;
[0046] 2) Select prime number q order cyclic group G 1 ,G 2 , g∈G 1 , the bilinear map is e:G 1 ×G 1 →G 2 ;
[0047] 3) PKG randomly selected calculate g 1 =g a ∈ G 1 .
[0048] 4) Randomly select u′∈Z q , v′∈G 1 , w′∈G, random number u i ,m j ,w k ∈ G 1 . n-dimensional vector U=(u i ), V=(v j ),W=(w k ). Then the public parameters of the system are params=(G 1 ,G 2 ,e,q,g,g 1 , g 2 ,u′,v′,w′,U,V,W), the master key is .
[0049] Step 2. Generic User Key Generation
[0050] 1) Assume that the user ID is a bit string ID of length n 1 ,...ID n . is the set of sequence number i with ID[i]=1;
[0051] 2) PKG randomly selected and calculate ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com