Application encipherment protection method of card reader
A technology for application programs and card readers, which can be used in program/content distribution protection, instruments, inductive record carriers, etc., and can solve the problem of high equipment cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
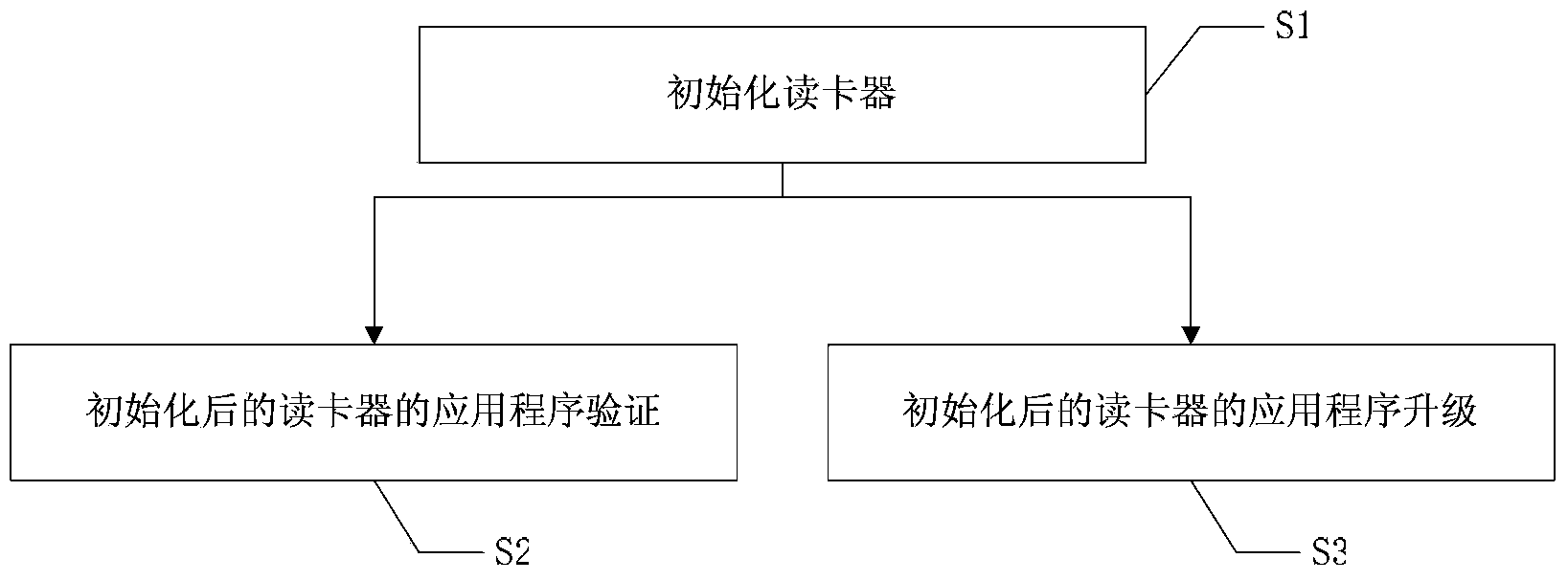
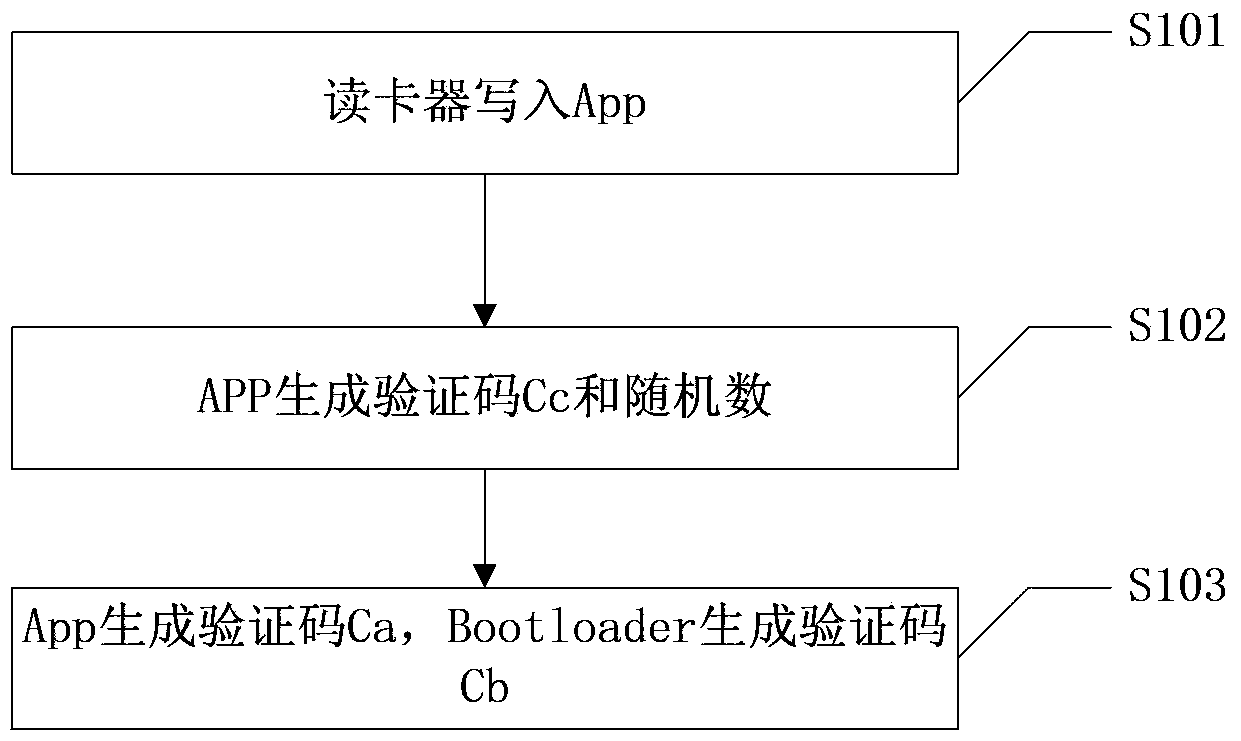
[0066] In the following, the present invention will be further described in conjunction with the drawings and specific embodiments.
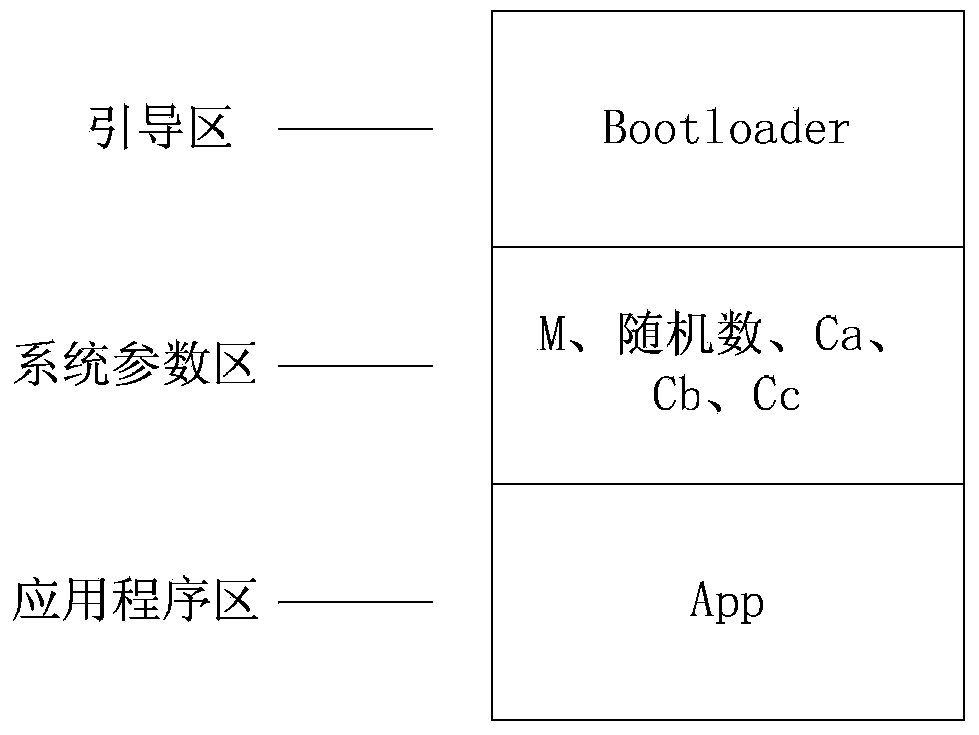
[0067] Such as figure 1 As shown, the logical partition of the FLASH memory of the card reader is the same as that of the prior art, including a boot area, a system parameter area and an application program area. Bootloader is stored in the boot area, M, random numbers, Ca, Cb, and Cc are stored in the system parameter area, and App is stored in the application program area.
[0068] In order to describe the aspect, the nouns involved in the present invention are firstly explained.
[0069] Bootloader: start the bootloader;
[0070] App: Application, application program;
[0071] CID: ChipIndentify, the unique identification number of the chip, which is a unique read-only serial number of 96 bits;
[0072] M: Startup code, which is a variable and is used to identify the program operation mode. There are three operation modes, namely App oper...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com