Mobile security financial terminal and financial transaction method
A technology for financial terminals and financial transactions, which is applied in the field of mobile security financial terminals and financial transactions, can solve the problems that users cannot be absolutely guaranteed not to be intercepted, and it is difficult to guarantee the security of the underlying I/O and display output of the system, so as to eliminate malware and Viruses threaten transaction security, improve confidence in use, and guarantee the effect of products
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0107] In this embodiment, the financial transaction of mobile payment is completed through the mobile security financial terminal, specifically the process of completing order payment.
[0108] Image 6 It shows the whole flow chart from acquiring mobile payment data (order generation, order entry) to completing mobile payment when the mobile security financial terminal of this embodiment is used for mobile payment.
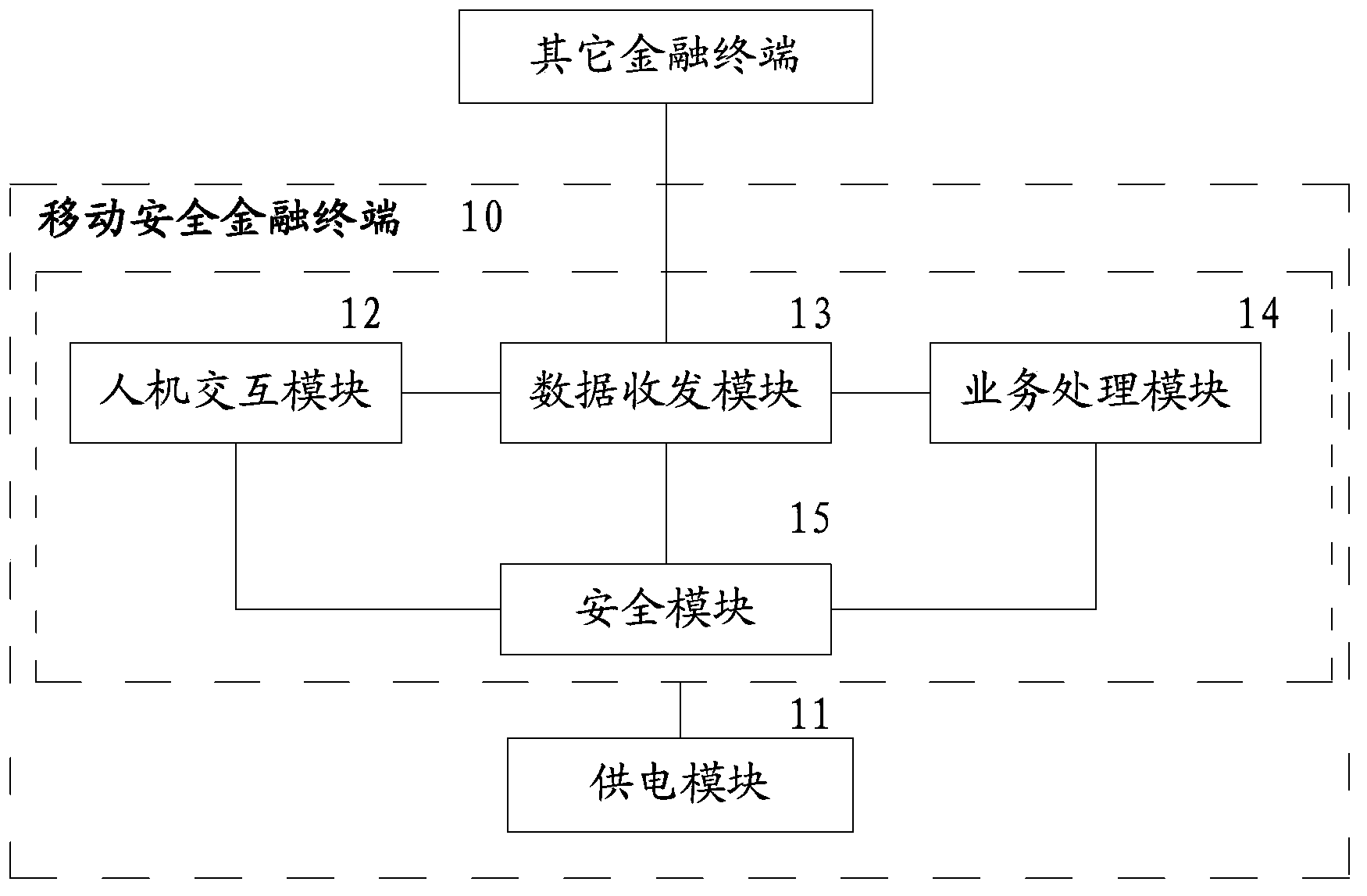
[0109] First, the data transceiving module 13 acquires the mobile payment data required to complete the order payment. The mobile payment data in this embodiment mainly refers to the order number and the order amount. Depend on Image 6 It can be seen from the figure that there are many ways to obtain the above mobile payment data, which can be obtained from computer online shopping, from mobile phones, or from QR codes printed on shelves. When order payment is made, the terminal only completes the payment link, that is to say, the terminal operation starts fr...
Embodiment 2
[0111] In this embodiment, the financial transaction of the network banking service is completed through the mobile security financial terminal, specifically the process of bank transfer.
[0112] When the financial transaction is completed, the mobile security financial terminal can directly communicate with the bank background to obtain the required bank transfer data, and of course the user can also directly input the terminal. The bank transfer data in this embodiment mainly refers to the transfer account number and transfer amount, etc. After the terminal obtains the data, it selects the transaction method, and then enters the account password and other information according to the requirements of the transfer business with each bank, and the terminal actively initiates with the bank background Transfer interaction process and confirm the transaction result.
[0113] The mobile security financial terminal described in the present invention is issued through unified certif...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com