A Potential Function Based Malicious Node Identification Method for Smart Meter System
A smart meter and malicious node technology, applied in the direction of measuring electrical variables, measuring devices, instruments, etc., can solve problems such as attacks, achieve low calculation and additional traffic, high recognition degree, and improve the detection success rate.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The technical solution of the present invention will be further described in detail below in conjunction with the accompanying drawings, but the protection scope of the present invention is not limited to the following description.
[0029] A potential function-based smart meter system malicious node identification method, it includes the following steps:
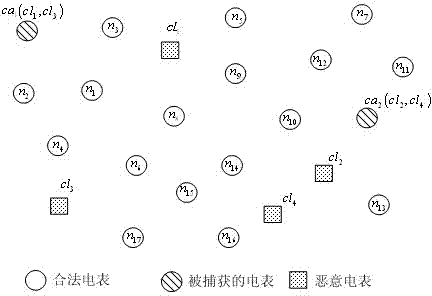
[0030] S1: Divide the smart meters in the smart meter system into a test group and a witness group, denoted as test nodes and witness nodes The smart meter in the smart meter system periodically plays the role of the node to be tested and the witness node;
[0031] S2: The witness node broadcasts request information R to the nodes under test within the communication range w , the node to be tested replies with the response message R in the following format c :
[0032] R c = {node ID, pilot}; (2)
[0033] S3: node cl i and cl j The proximity of the position at time t is represented by Indicates that the w...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com