A Method of Generating Dynamic Password Using Static Password as Source
A technology of dynamic password and static password, applied in the direction of encryption device with shift register/memory, etc., can solve the problems of static password theft, easy to be stolen, and cracked by special algorithm for dynamic verification code, so as to reduce the number of stolen passwords. , the effect of improving safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
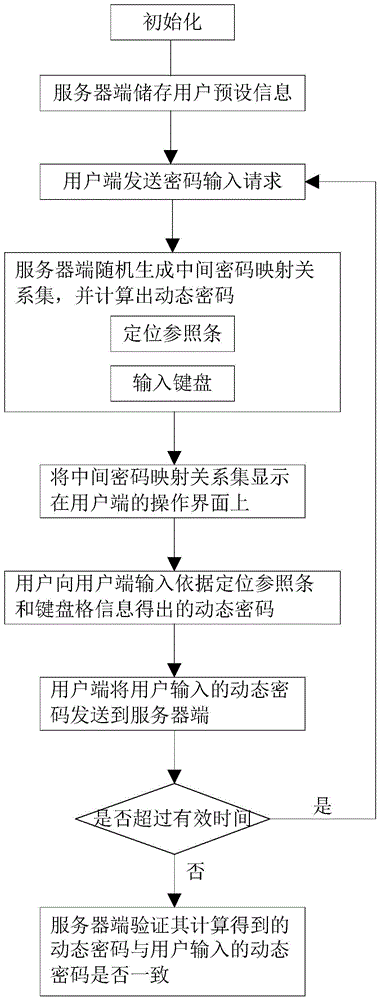
[0046] Such as figure 1 and Figure 4 As shown, the method for generating a dynamic password using a static password as a source in Embodiment 1 of the present invention includes the following steps:
[0047] (S1) The server stores the static password and index code preset by the user;
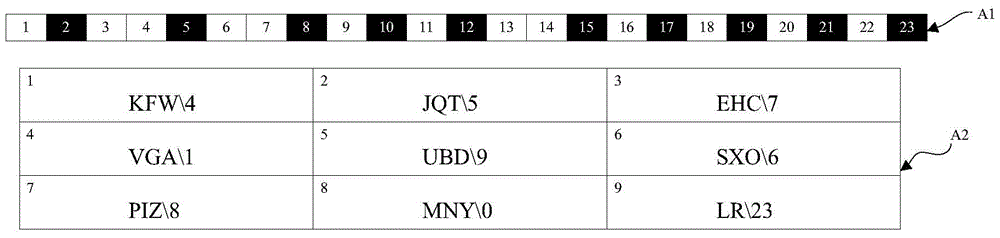
[0048] (S2) Every time the server receives a password input request sent by the user through the user terminal, it randomly generates an intermediate password mapping relationship set, and the index code is used as one of the password mapping relationships in the intermediate password mapping relationship set to select The base point is used to designate one of the intermediate password mapping relationship sets as the intermediate password used for the current password input, and then generate a dynamic password through the dynamic password mapping relationship between the intermediate password and the input keyboard; and, the server randomly generates The password mapping relationship set ...
Embodiment 2
[0066] The method for generating a dynamic password using a static password as a source in Embodiment 2 of the present invention is basically the same as Embodiment 1, and their difference lies in that in Embodiment 2, it is not necessary to use the index code to calculate the positioning reference bar through a specific calculation rule. Instead, use the index code +1 as the first mapping mark of the static password on the positioning reference bar. At this time, the index code is any natural value. Of course, you can also directly use the value of the index code as the static code. The first bit of the password on the positioning reference bar is mapped to the marker bit, but at this time the index code should be preset to any natural value other than 0, and this method will not be described for example.
[0067] The following is an example to illustrate the specific operation steps for the user to use the index code to obtain the dynamic password through the password mapping...
Embodiment 3
[0074] The method for generating a dynamic password from a static password in Embodiment 3 of the present invention is basically the same as Embodiment 1, and their difference lies in that the input keyboard in Embodiment 3 includes ten keyboard grids. In addition, the input keyboard can also include eleven or more keyboard grids, and English characters are added as the numbers of the keyboard grids. The implementation principle is the same as that of the third embodiment, and will not be repeated here.
[0075] In the following, an example is used to illustrate the specific operation steps for the user to use the index code to obtain the dynamic password through the password mapping relationship set displayed on the operation interface of the user terminal in the third step (S3) of this embodiment:
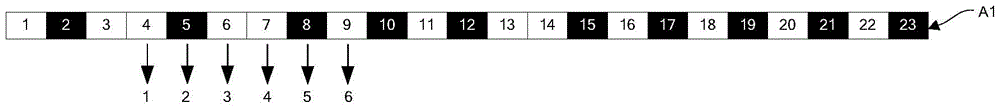
[0076] Such as Figure 9 As shown, when the server receives the password input request sent by the user through the client, the password mapping relationship set is randomly gene...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com