Method for mobile internet malicious application software detection based on support vector machines
A support vector machine and mobile Internet technology, applied in the field of mobile Internet malicious application software detection, can solve the problems of end user infringement, malicious application software detection method is not mature enough, processing speed is slow, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the accompanying drawings and the experimental conditions of the examples.
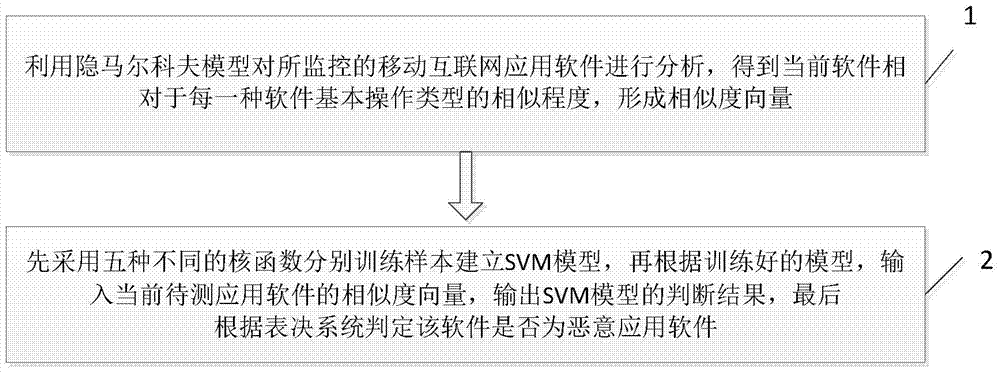
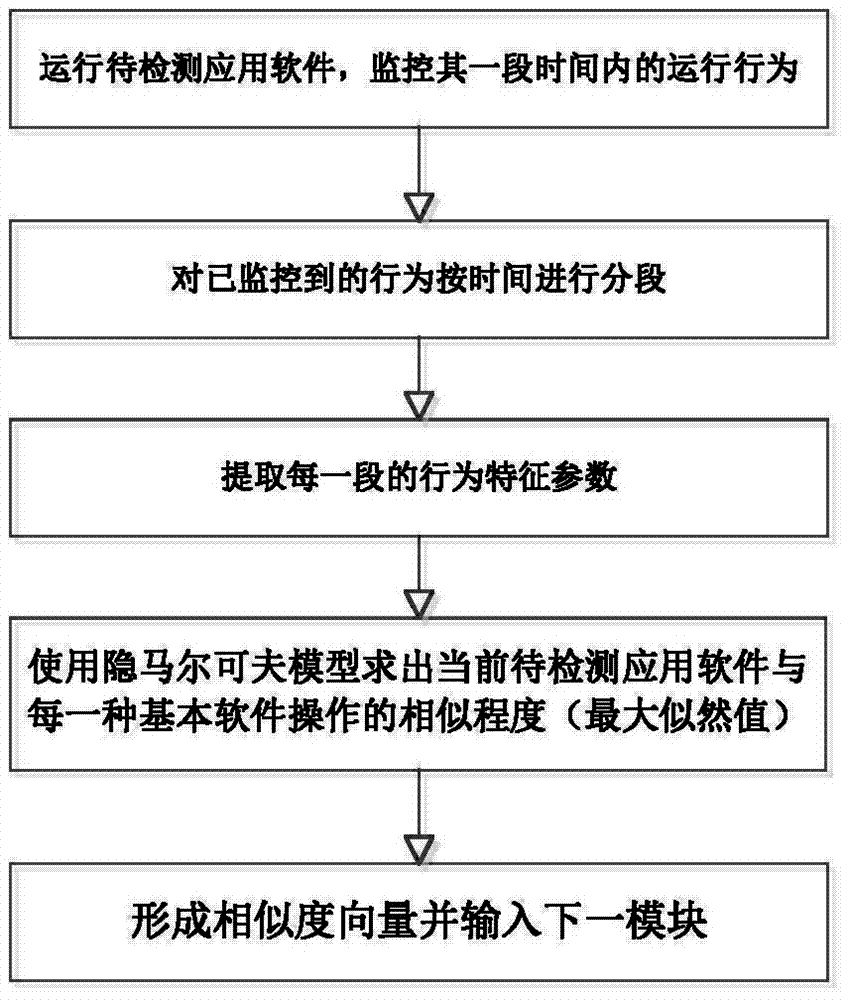
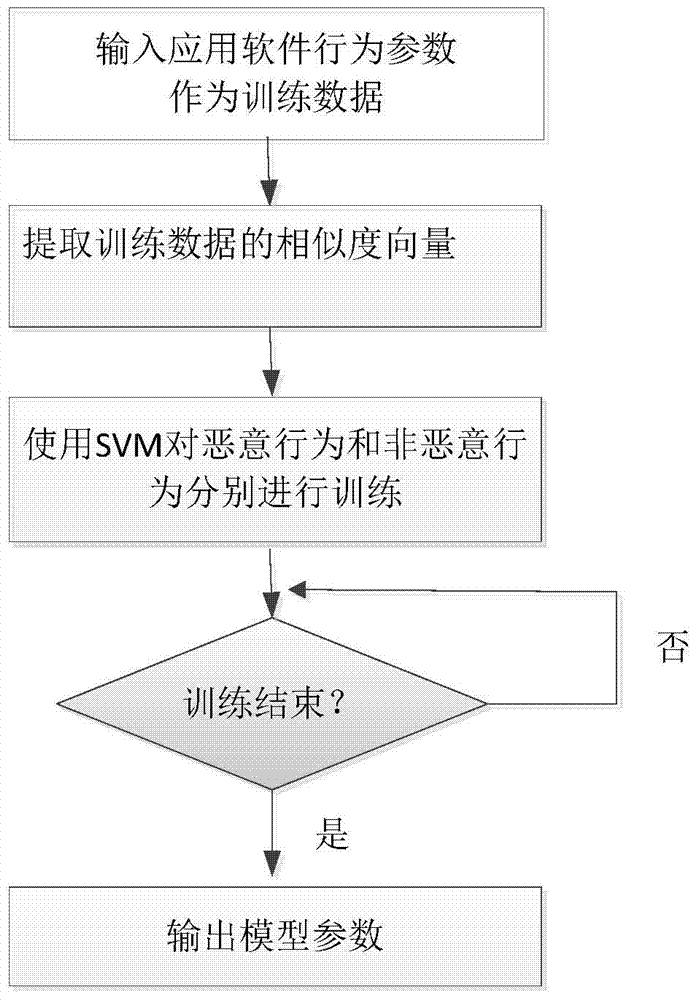
[0039] The present invention is a mobile Internet malicious application software detection method based on a support vector machine. The method first runs the application software to be detected and extracts the characteristic parameters of the software running for a period of time, and then uses these parameters and several basic software operation types Hidden Markov models are compared to obtain similarity vectors. Finally, on this basis, five SVM models are used for voting analysis to judge whether the current application software to be detected is a malicious application software. When detecting malicious application software, the present invention can overcome the shortcomings of incomplete definition of malici...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com