Palm print information coding, encryption and application method
An encryption method and application method technology, which is applied in the direction of instruments, character and pattern recognition, computer components, etc., can solve security problems and limit the large-scale promotion and application of biometric identification technology, and achieve high security effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
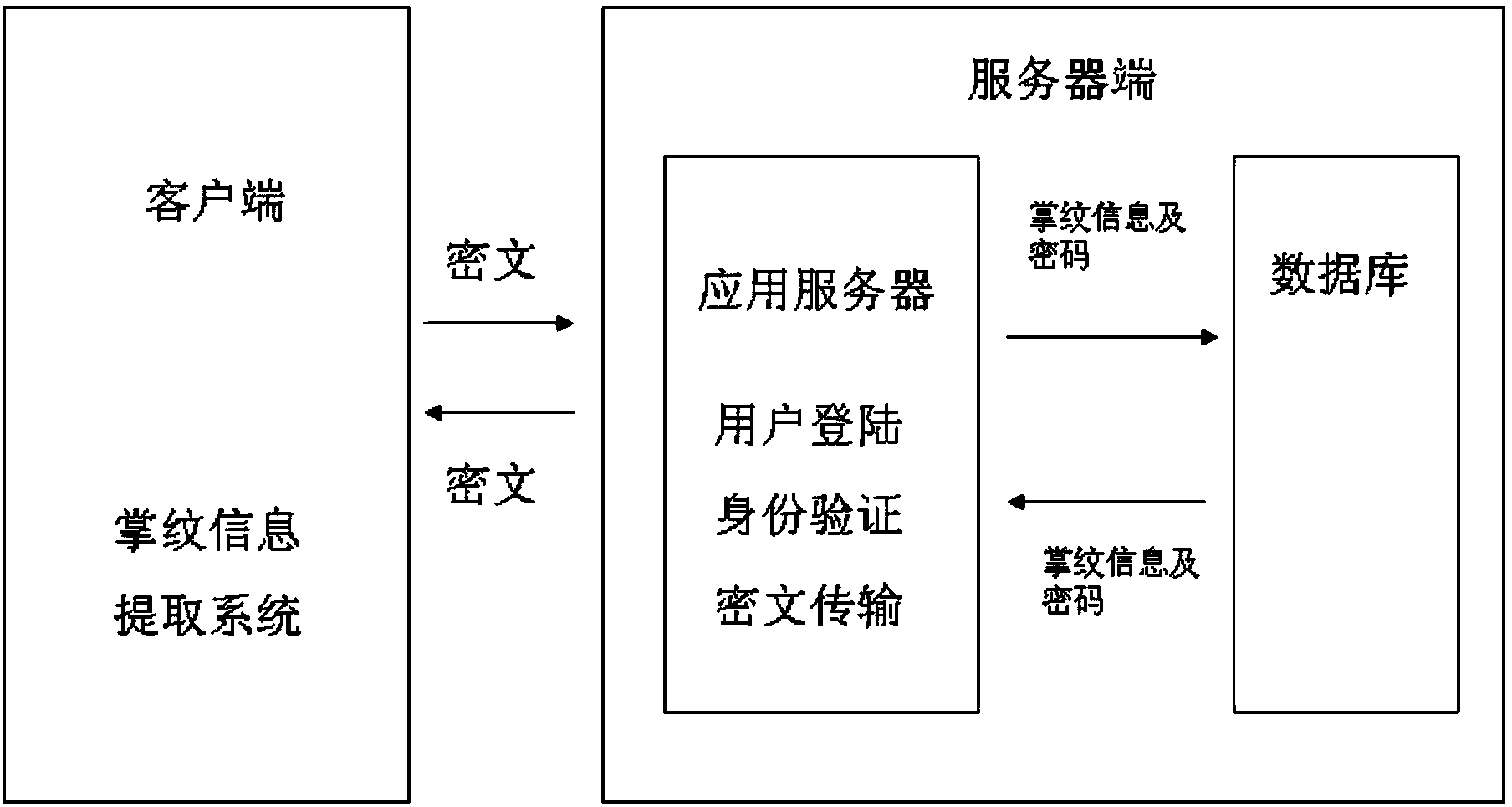
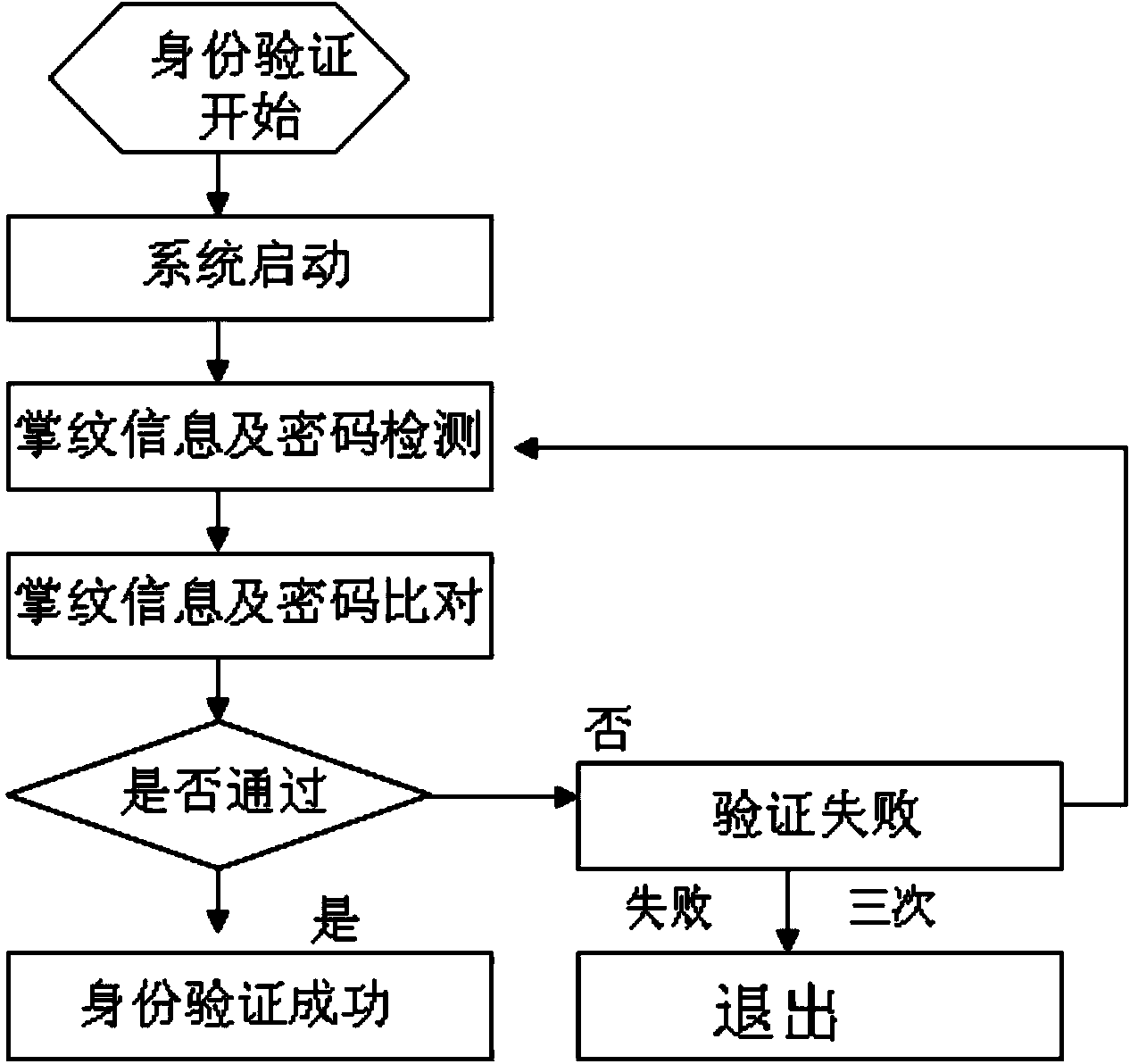
[0025] The user Zhang San first sets up an account in the bank and submits the palmprint information of the two hands and the 0-1 sorting and coding method of the left and right hands selected by him, and is formed by six palm extension codes of 1, 1, 0, 0, 1, 0 The identity verification password, the alarm password formed by stretching the palm three times 1, 1, 0 and the backup password formed by stretching the palm five times 1, 0, 1, 0, 1 are included in the database of the bank server. Then Zhang San needs to pay for online shopping through the client installed on the mobile phone. After logging into the bank account, he first captures the image of palm stretching six times through the camera of the mobile phone, and sends the ciphertext obtained through the symmetric encryption algorithm to the bank server, and the bank server stretches it six times. After feature extraction and template extraction of the palm image, the palmprint information of the six stretched palms wa...
Embodiment 2
[0030] After the access control system network is set up in a certain prison system, first collect the palmprint information of the two hands submitted by the prison guards, the sorting and encoding method of 0 to 1 of the left and right palms, and the identity verification of the selected 1, 1, 1 Password, 1, 0, 1 three-time stretch alarm password to be included in the database of the access control system server. Prison guard A usually goes to work by using the client terminal with capacitive palmprint sensors installed at each prison door to use the palmprint information selected by him for three times and the identity verification password formed by it through the ciphertext obtained by the asymmetric encryption algorithm. Verify to enter and exit the prison access control system. If the prison guard is threatened by criminals, an alarm will appear through the palm print information formed three times and the password formed to inform other prison guards to provide support,...
Embodiment 3
[0032] Li Si installed an ultrasonic palmprint sensor authentication system on the safe, so that the safe can only be opened after successful identity verification. Then Li Si submitted the palmprint information of his two hands and the 0-1 sorting method he selected from right to left and the 0, 0, 1 identity verification password formed by stretching his palms three times, and the 1, 1 password formed by stretching his palms twice. The alarm password and the 1, 0, 1, 0, 1 backup password formed by stretching the palm five times are recorded in the database of the safe server. At this point the client and server are merged together. When Li Si later needs to open the safe, he can log in and verify his identity through the palm print information of his selected hand and the password information formed.
[0033] When Li Si forgot his identity verification password, he could log in through the palm print information of the selected hand and the backup password formed by it and ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com