Fast encoding method of access control list (ACL) behavior set
An access control list and fast coding technology, applied in digital transmission systems, data exchange networks, electrical components, etc., can solve problems such as multi-time, affecting hash table query table compilation time, and experience degradation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0017] The technical solution of the present invention will be described in detail below in conjunction with the accompanying drawings and specific embodiments.
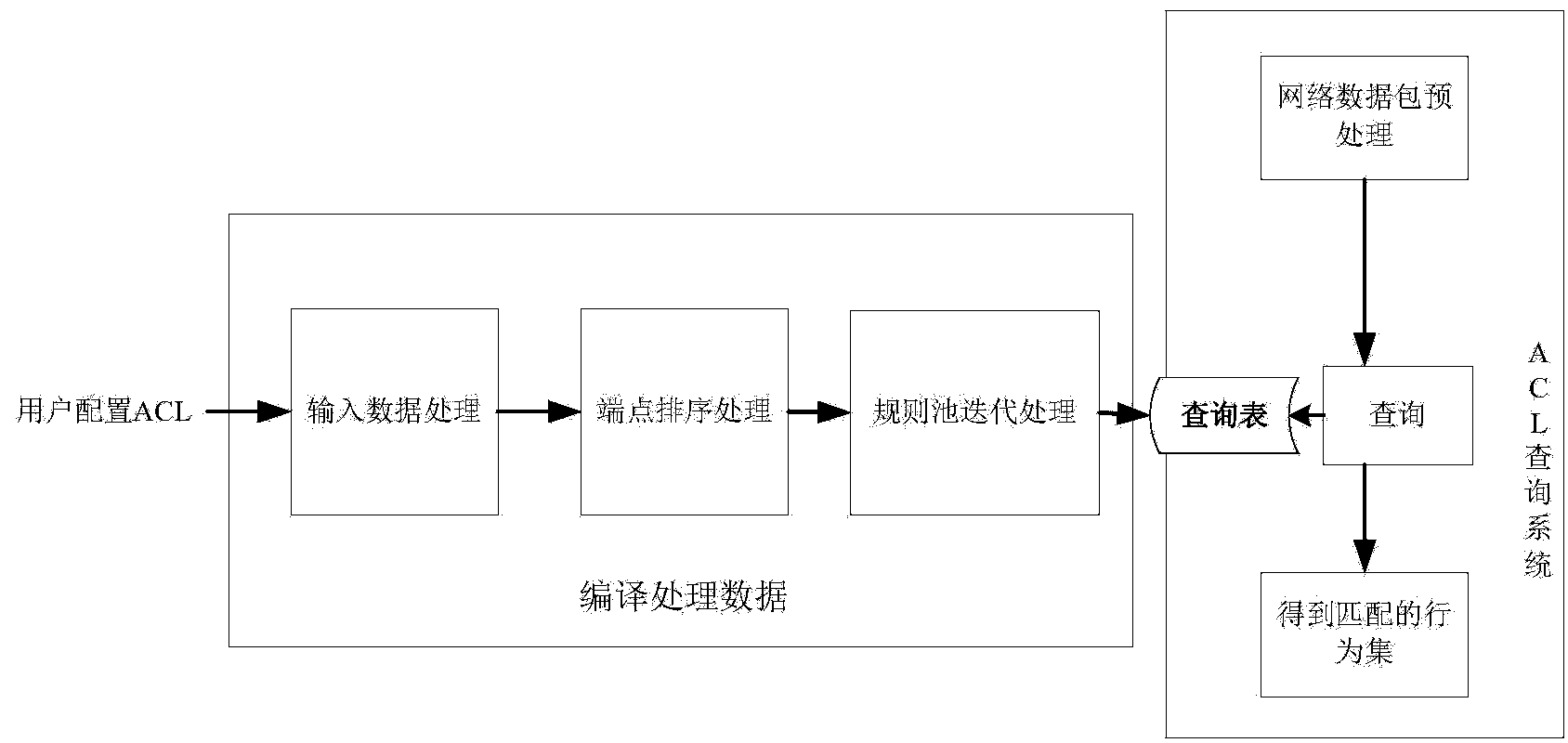
[0018] The encoding method of the present invention mainly imports the ACL entries configured by the user through the user configuration interface, and obtains a query table after compiling data and processing, and provides it to the ACL query system for use.
[0019] Compiled data processing includes three steps: input data processing, endpoint sorting processing, and rule pool iteration processing, among which:
[0020] Input data processing extracts the matching range of each keyword in each ACL entry configured by the user, including the upper limit and lower limit of the range, and divides the longer part of the keyword data into different keywords according to the specific situation , that is,
[0021] Input data processing transforms the access control list entries into an independent endpoint information str...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com