Method for realizing security and credibility of intelligent mobile terminal and system thereof
A technology of smart mobile terminals and secure channels, which is applied in the field of realizing the security and trustworthiness of smart mobile terminals, and can solve difficult problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
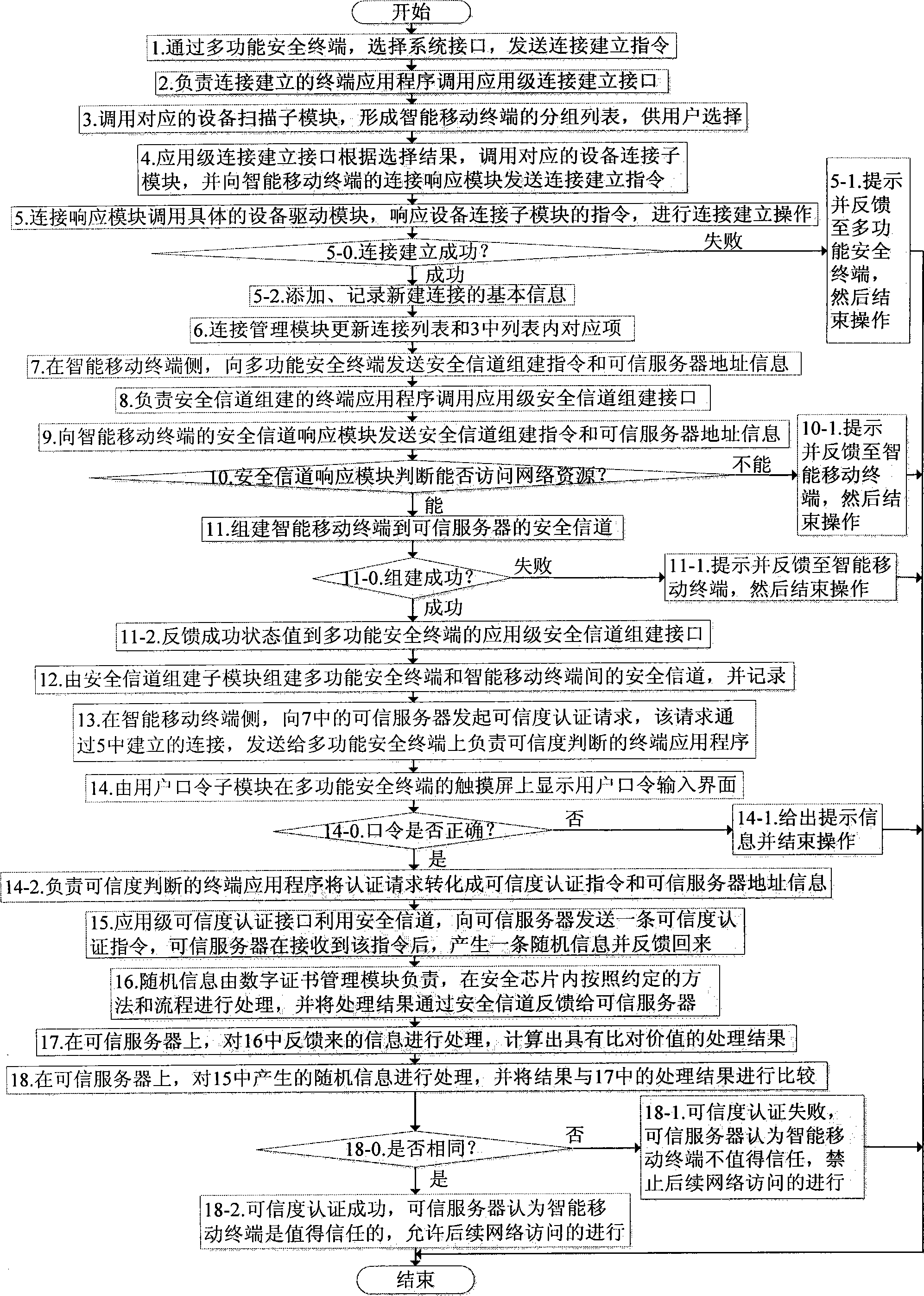
[0052] The present invention will be further described in detail below in conjunction with specific embodiments.
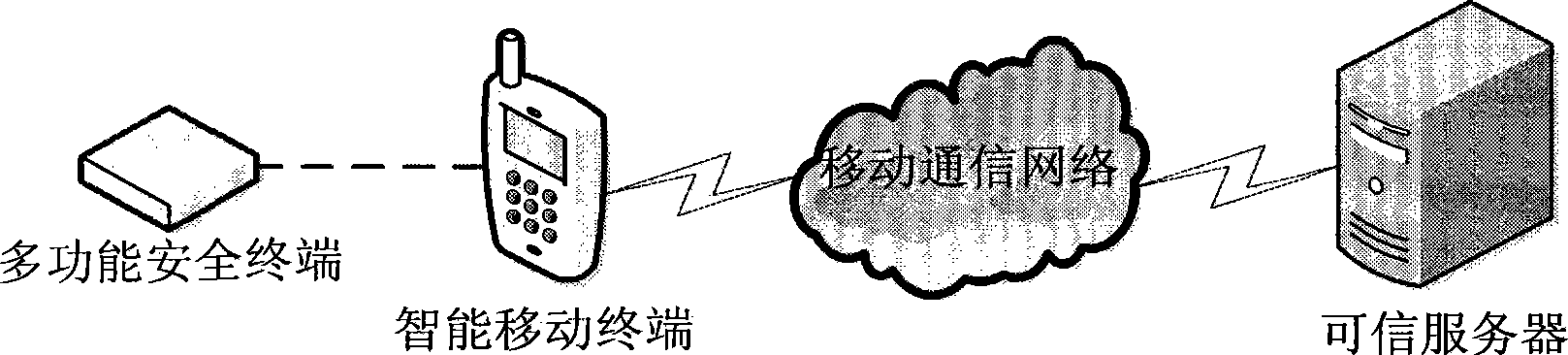
[0053] as attached figure 1 As shown, the system composition includes: a multifunctional security terminal, an intelligent mobile terminal and a trusted server.
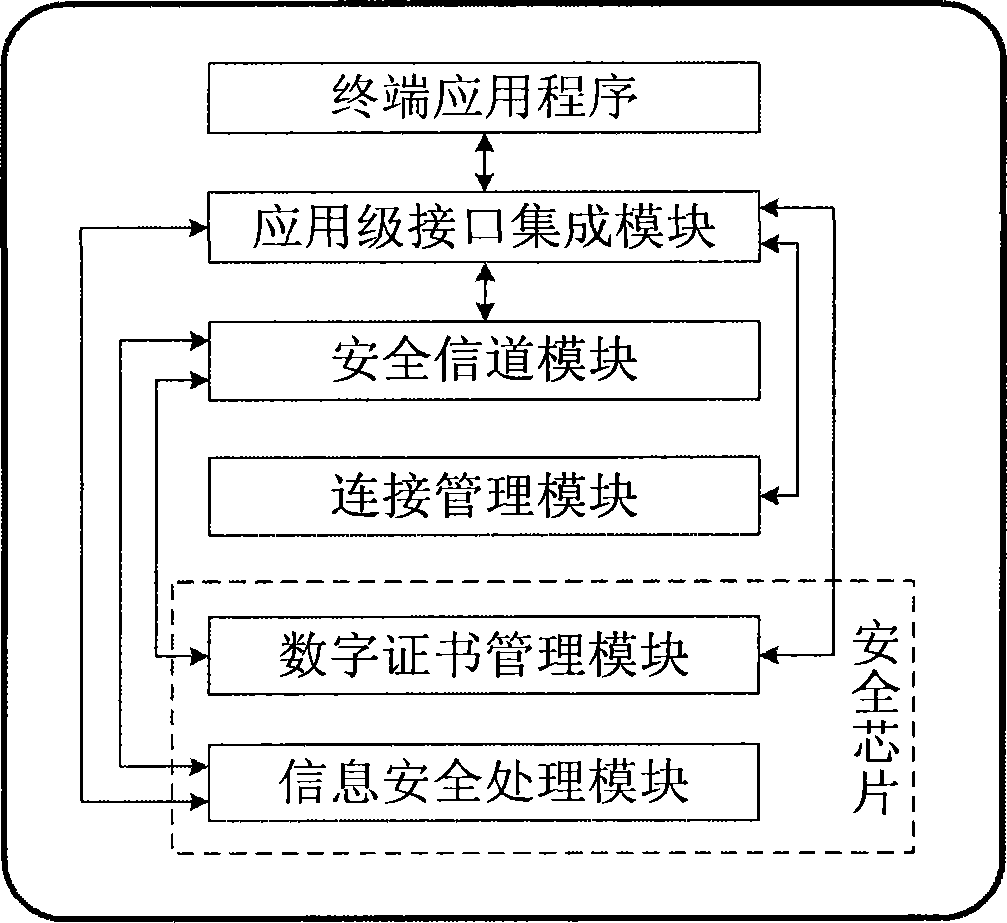
[0054] The multifunctional security terminal is completely independently developed, including: 1 set of system interface, 1 set of input and output devices and internal functional modules. The entire system interface includes but is not limited to: 1 Bluetooth, 1 Wi-Fi, 1 USB interface, 1 NFC and 1 audio interface. The whole set of input and output devices includes but not limited to: 1 display screen, 1 touch screen, 1 buzzer / vibrator, 1 LED indicator light and 3 buttons. The internal functional modules are based on the open source operating system on the mobile platform, combined with a security chip with a unique serial number, and reinforced according to security requirements; the internal function...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com