Network access identity recognition system and method
A technology of identification and identification, which is applied in the direction of instruments, time registers, single input port/output port registers, etc., can solve the problems of high cost, high system construction cost, inconvenient use for users, etc., and achieve convenient use , save cost, and facilitate project deployment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
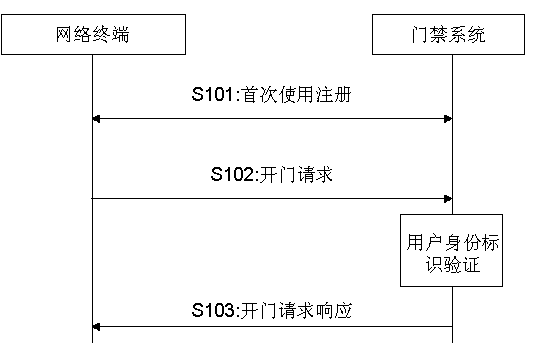
[0030] The principle of the network access control identification system of the present invention is as follows: figure 1 and figure 2 As shown, it includes a network access control identification device and a communication terminal, and the network access control identification device and the communication terminal communicate through a local area network or the Internet.
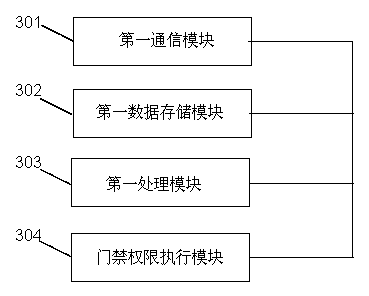
[0031] The network access control identity recognition device is used to process the registration of the communication terminal and issue the user access control identity to the communication terminal; process the door opening request of the communication terminal, and perform the corresponding access control authority operation according to the result of the legality verification of the user access control identity;
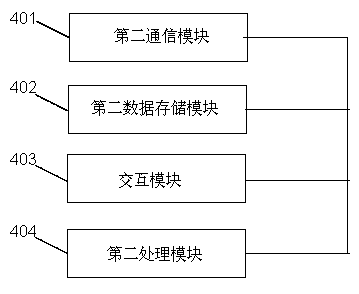
[0032] The communication terminal is used for: completing the user registration operation, and initiating a door opening request according to the stored user access control identity. The s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com