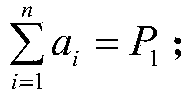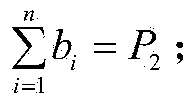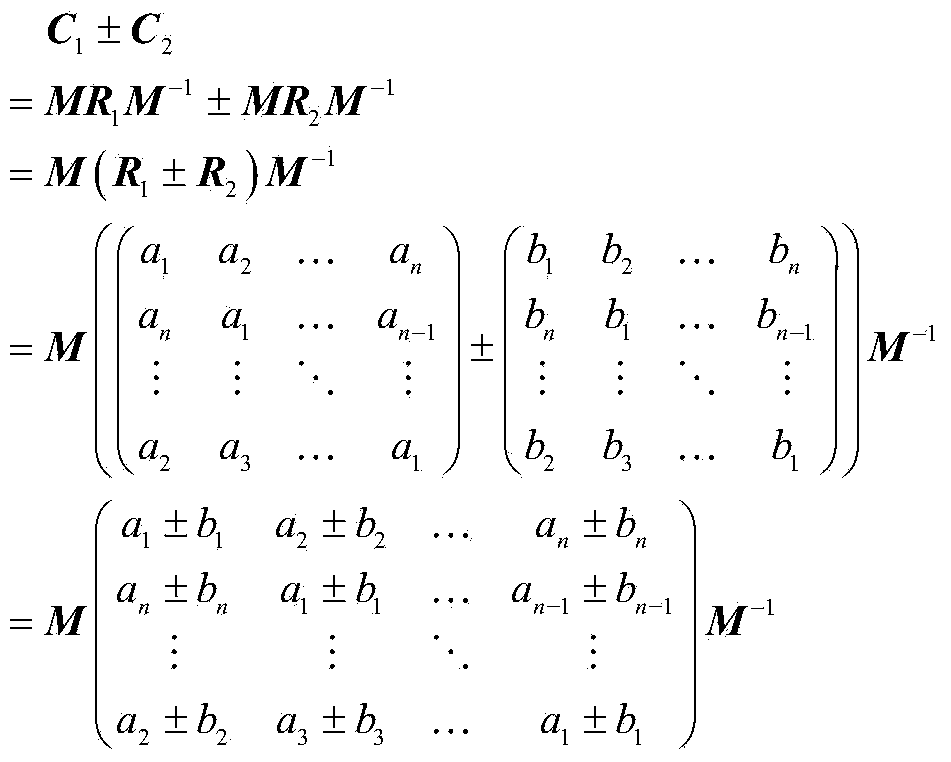Circulant matrix transformation based and ciphertext computation supportive encryption method
A technology of cyclic matrix and encryption method, which is applied in the direction of digital transmission system, electrical components, transmission system, etc., and can solve the problems of high complexity, complex calculation amount and large calculation amount of fully homomorphic scheme
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The present invention is an encryption method based on cyclic matrix transformation that supports ciphertext calculation (English full name: Computable Encryption Scheme based on Cycle Matrix; abbreviation: CESCM), which mainly includes encryption of original data, encryption of calculation parameters, and arithmetic operation of encryption matrix 1. Four steps of decrypting the encrypted operation results. The implementation steps of CESCM are described in detail below:
[0029] Step 1. Encryption of the original data: convert the original data into a vector, then convert the vector into a circular matrix, and encrypt it through the key matrix to obtain an encrypted outsourcing matrix;
[0030] Step one specifically includes the following steps:
[0031] Let the original data P 1 is a rational number.
[0032] (1) will P 1 random decomposition into vector r 1 =(a 1 ,a 2 ,...,a n ) T , where n represents the dimension of the vector, a i (i=1,2,3...n) is random ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com