A method for implementing a secure computer
A computer and computer control technology, applied in the computer field, can solve problems such as leaking commercial secrets, and achieve the effect of preventing leaks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
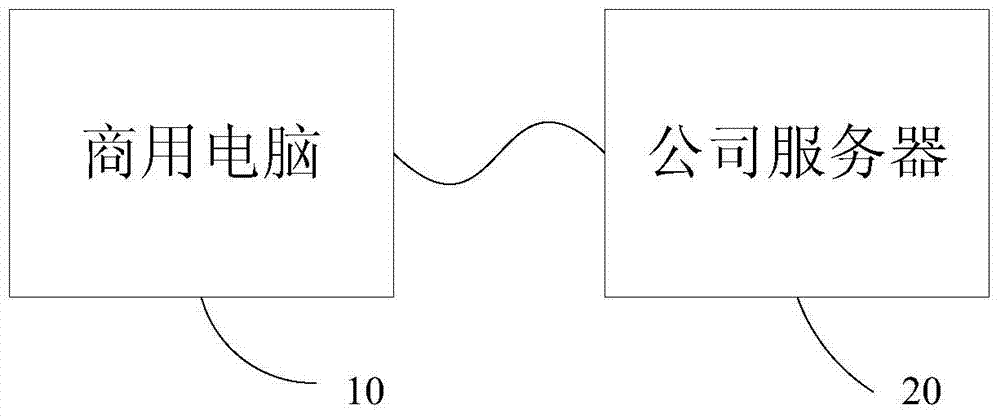
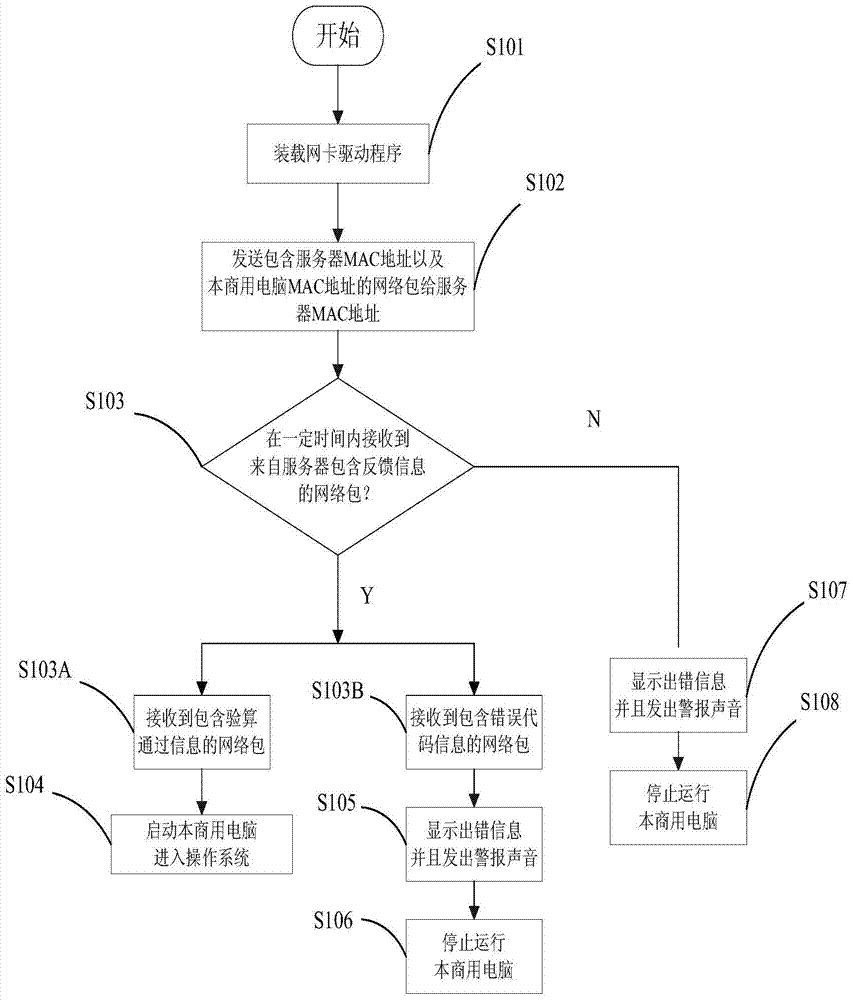
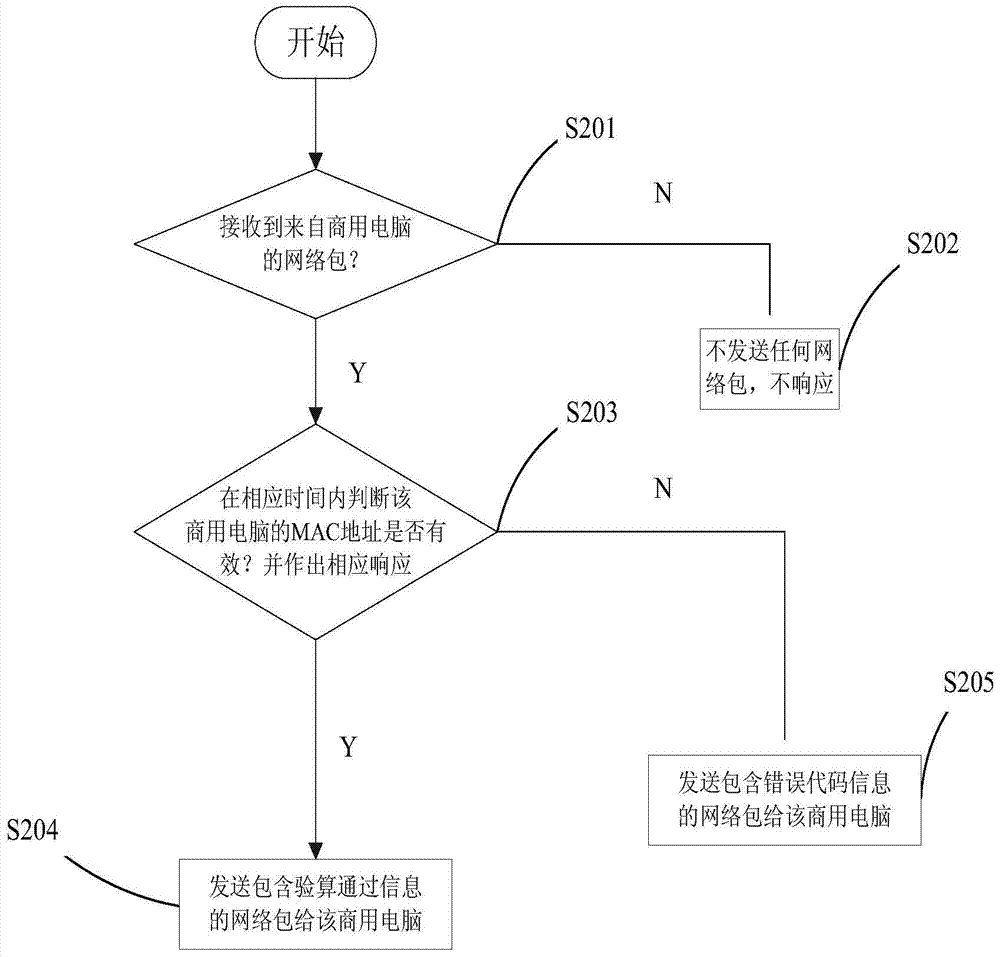
[0039] Such as figure 1 As shown, the embodiment according to the present invention involves a business computer 10 and a company server 20, and the communication between the two is through the TCP / IP protocol. When the commercial computer 10 is used for the first time, use the motherboard configuration program of the commercial computer 10, that is, UEFI BIOS SETUP, to set and input the MAC address of the company server 20. When the commercial computer 10 is turned on, after the UEFI BIOS hardware self-test finishes, the network card driver will be loaded in the UEFI BIOS SETUP, and the network detection function will be turned on, such as figure 2 Shown in S101. The commercial computer 10 will send a network packet containing the MAC address of the company server 20 and the MAC address of the commercial computer 10 to the MAC address of the company server 20, such as figure 2 As shown in S102, and encrypt the certificate of the commercial computer 10, and then wait for t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com