Password input method based on touch screen, and touch terminal
A password input and touch screen technology, applied in the field of communication, can solve the problems of high cost, no industrialization advantages, and inapplicability to the promotion and use of large interviews, and achieve the effect of low cost, eliminating the risk of password leakage, and ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
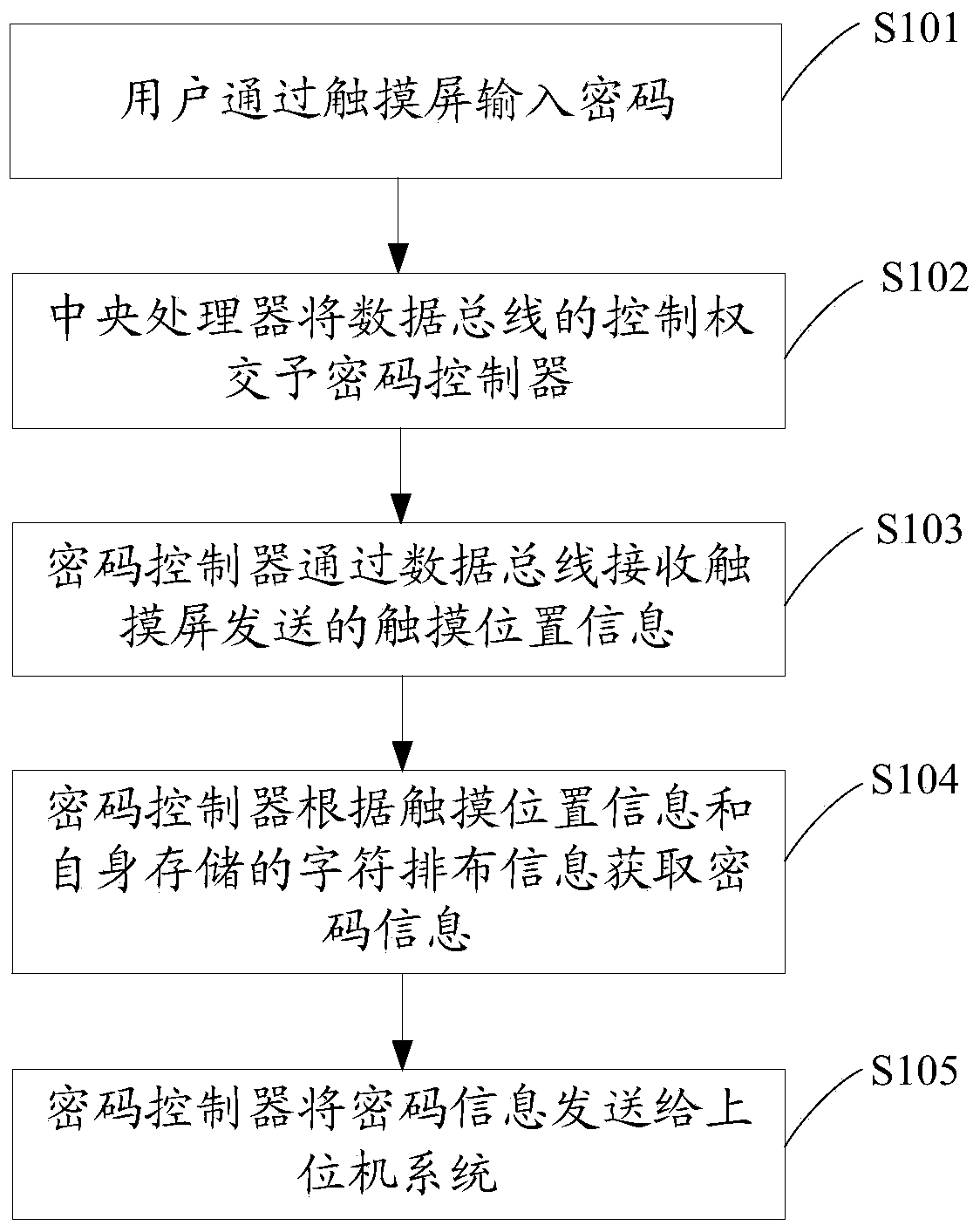
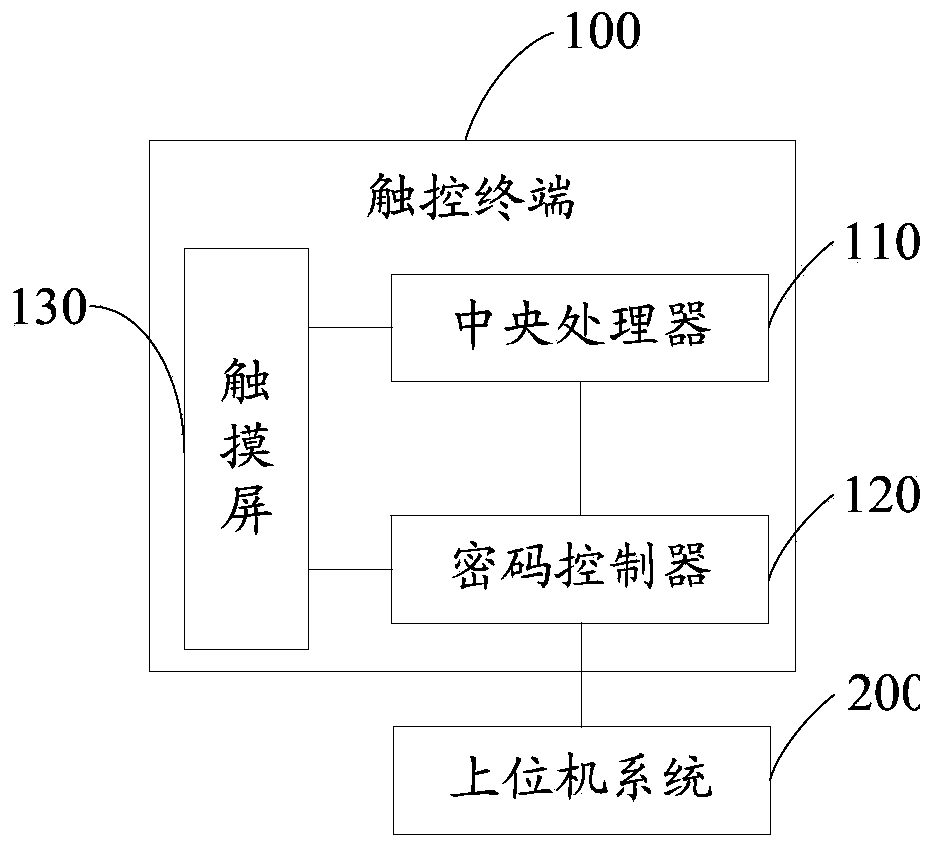
[0036] see figure 1 , propose the first embodiment of the password input method based on the touch screen of the present invention, the password input method includes the following steps:
[0037] Step S101: The user enters the password through the touch screen
[0038] The password input described in step S101 mainly means that in the scenarios of electronic payment and server login, the touch terminal needs to send the password input by the user to the remote host computer system, and the host computer system will perform the password verification on the password. Verification situation. The password of the present invention should be understood in a broad sense, including all private information that can be used as identity verification for input.
[0039] Step S102: the central processing unit hands over the control of the data bus to the cryptographic controller
[0040] When the user performs ordinary operations on the touch screen except for password input, the centr...
no. 2 example
[0049] see figure 2 , propose the second embodiment of the password input method based on the touch screen of the present invention, the password input method includes the following steps:
[0050] Step S201: The central processing unit randomly arranges password input characters on the touch screen for users to input passwords through the touch screen
[0051]The character arrangement in this embodiment is not solidified, but the central processor controls the touch screen to display randomly arranged password input characters, thereby preventing the solidified character arrangement information from being stolen and further improving the security of password input.
[0052] Step S202: The central processing unit hands over the control of the data bus to the cryptographic controller, and sends the character arrangement information to the cryptographic controller
[0053] When the user needs to input a password through the touch screen, the central processing unit releases th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com