Message processing method and device
A message processing and message technology, applied in the field of communication, can solve the problems of high operation cost and maintenance cost, low utilization rate, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
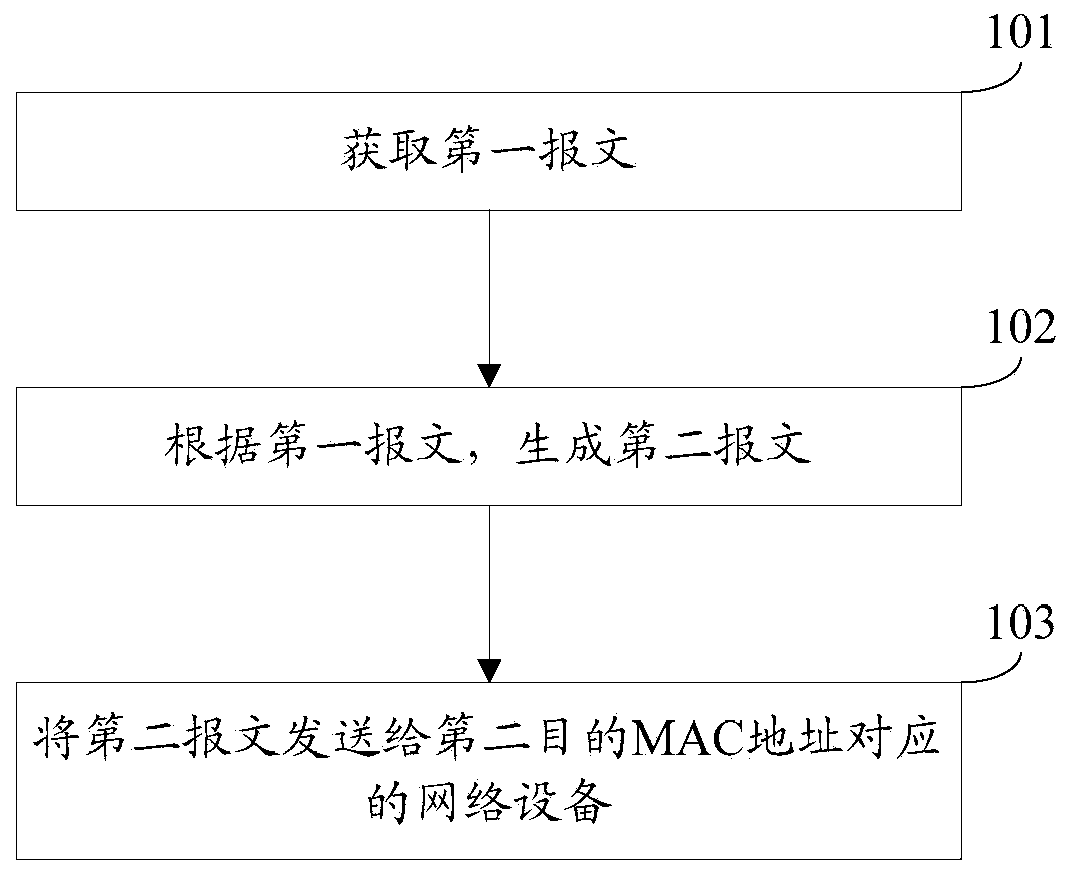
[0094] The embodiment of the present invention provides a message processing method, the execution subject of the method may be a security device or other listening device, see figure 1 , the method includes:
[0095] Step 101: Obtain a first packet.
[0096] In this embodiment, the first packet includes first packet content, a first source MAC address, and a first destination MAC address.
[0097] In practical applications, the first message may be a message transmitted between a domestic gateway and a foreign gateway, may also be a message transmitted between inter-provincial gateways, or may be a message transmitted between metropolitan gateways.
[0098] Step 102: Generate a second message according to the first message.
[0099] In this embodiment, the second packet includes a second packet content, a second source MAC address, and a second destination MAC address, the second packet content includes the first packet content, and the second source MAC address includes ta...
Embodiment 2
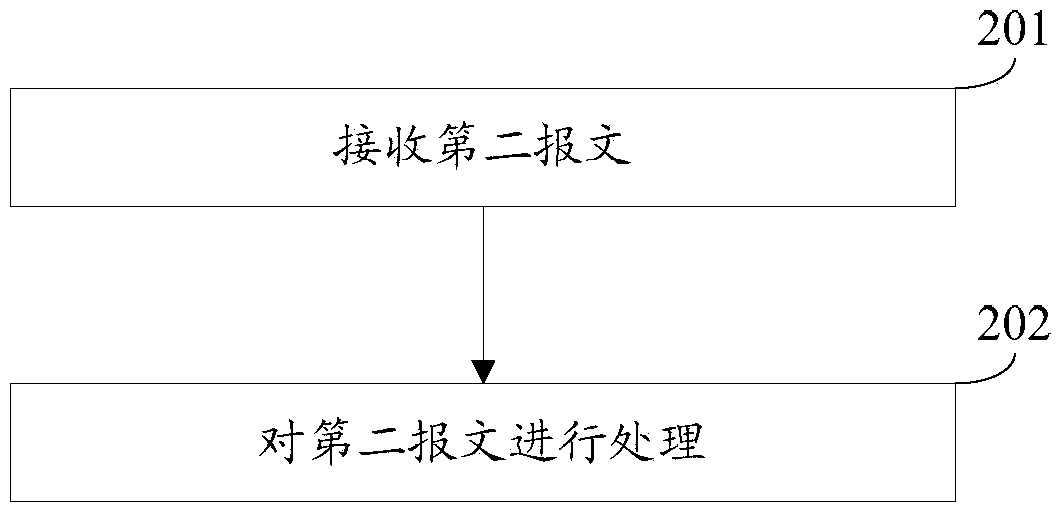
[0106]The embodiment of the present invention provides a message processing method, the execution subject of the method may be a traffic analysis server or a statistics server, see figure 2 , the method includes:
[0107] Step 201: Receive a second packet.
[0108] In this embodiment, the second packet includes a second packet content, a second source MAC address, and a second destination MAC address, the second packet content includes the first packet content, and the second source MAC address includes tag information.
[0109] Among them, the label information may include the link number of the link transmitting the first message, the ACL identifier used to determine the first message, the port number of the port through which the first message passes, and the device number of the device through which the first message passes. one or more of .
[0110] Specifically, the second packet may be sent by the security device in Embodiment 1 or other monitoring devices.
[0111]...
Embodiment 3
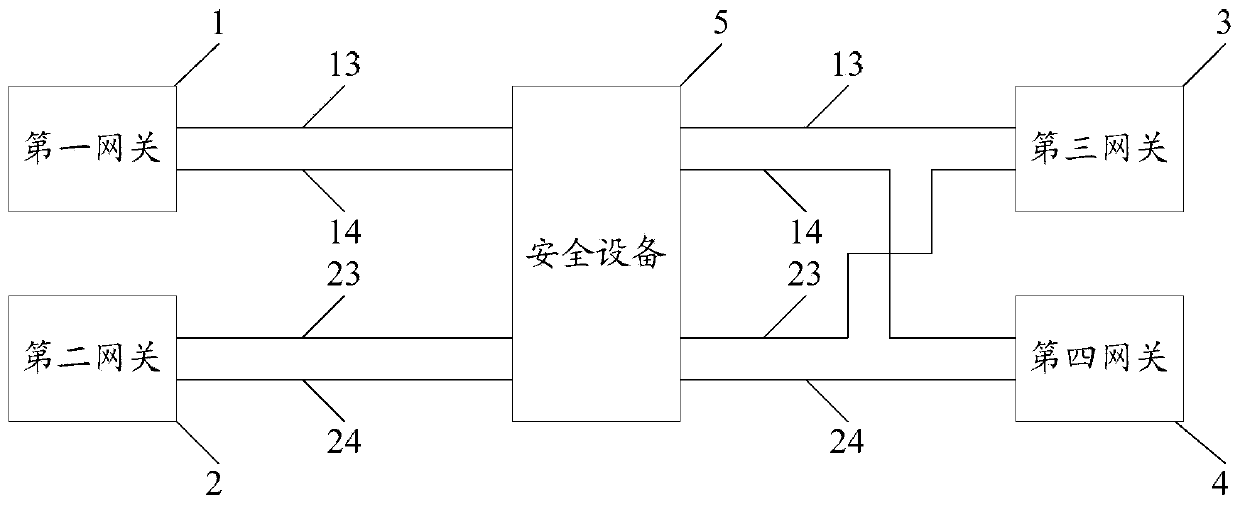
[0122] This embodiment uses the second source MAC address to replace the first source MAC address, and uses the second destination MAC address to replace the first destination MAC address to generate a second message as an example, and specifically describes the message processing method provided by the present invention . The embodiment of the present invention provides a message processing method, see Figure 4 , the method includes:
[0123] Step 301: The security device acquires the first packet.
[0124] In this embodiment, the first packet includes first packet content, a first source MAC address, and a first destination MAC address.
[0125] Optionally, this step 301 may include:
[0126] Match the received message with the ACL, which is used to determine the message that needs to be forwarded;
[0127] The packet matching the ACL is used as the first packet.
[0128] Optionally, ACLs can be configured as required.
[0129] Step 302: The security device generates ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com