Bidirectional security authentication method for RFIP system
A two-way authentication and security technology, applied in user identity/authority verification, cooperative devices, instruments, etc., can solve the problem that plaintext transmission cannot resist eavesdropping and replay attacks, and cannot derive one-way security encryption characteristics and hash functions Fast calculation speed and other issues, to achieve the effect of reducing query overhead, increasing the scope of application, and low cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] Below in conjunction with accompanying drawing and specific embodiment the present invention is described in further detail:
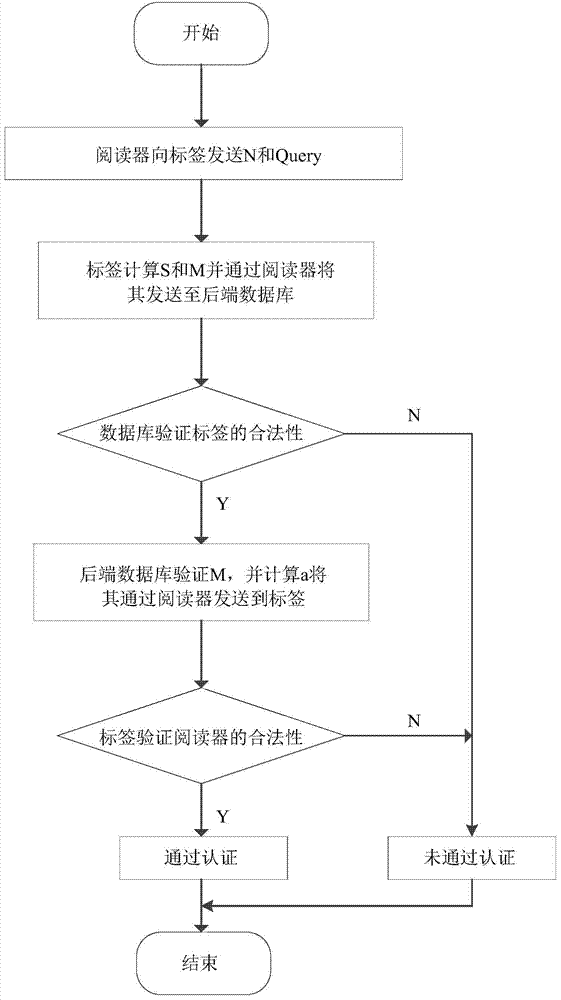
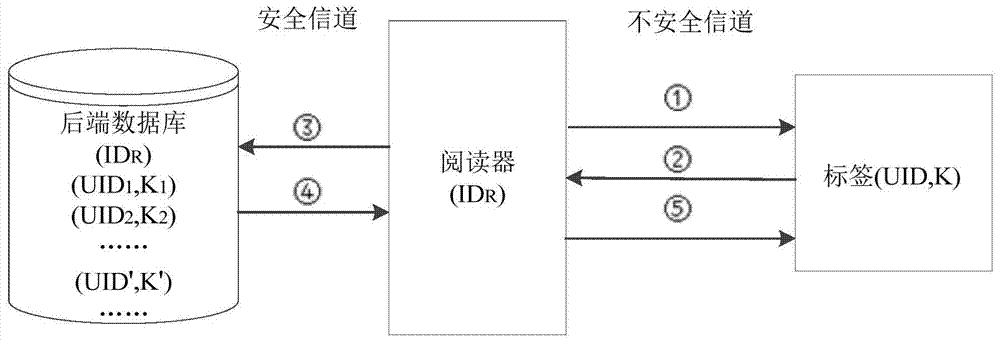
[0026] The basic idea of the present invention is aimed at the safe two-way authentication of the radio frequency identification system. It is generally assumed that the communication channel between the reader and the background database server is safe, and information can be transmitted in plain text between them. insecure communication channels. The one-way secure encryption function is used to encrypt the authentication message before transmission, which can prevent security threats such as data eavesdropping. During the authentication process, the back-end database must first confirm the identity of the reader, which can avoid access by illegal readers, calculation and storage overhead. Compared with other authentication methods, it is relatively suitable, and effectively realizes a secure two-way authentication process between the tag an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com