System and method for cloud application access control in cloud computing environment
A cloud computing environment and access control technology, applied in the field of cloud computing, can solve problems such as information leakage, and achieve the effect of shielding information leakage and flexible control
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
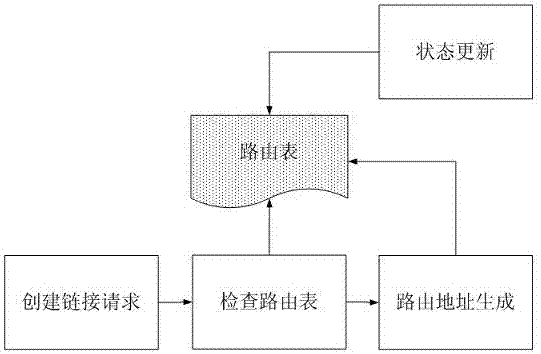
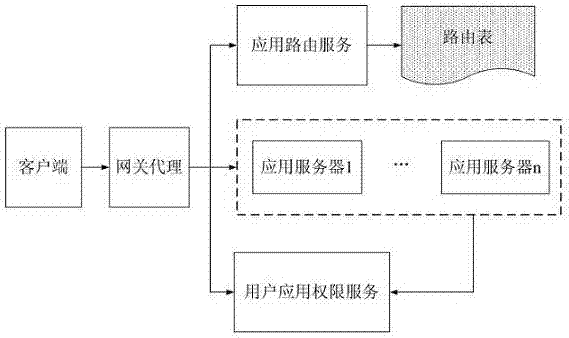
[0031] The application scenarios of the present invention include users and cloud application providers. The user is mainly the initiator of the application link, and the client may be assisted by a third-party desktop program to obtain the user's basic login information, which is also a necessary parameter for creating a cloud application link. The cloud application provider will provide the management and maintenance function of user permission information, which is stored in the user application permission service module. Cloud applications will run on cloud application servers. In actual deployment, cloud application servers are generally servers with multi-session login functions, which can be virtual machines or physical machines.
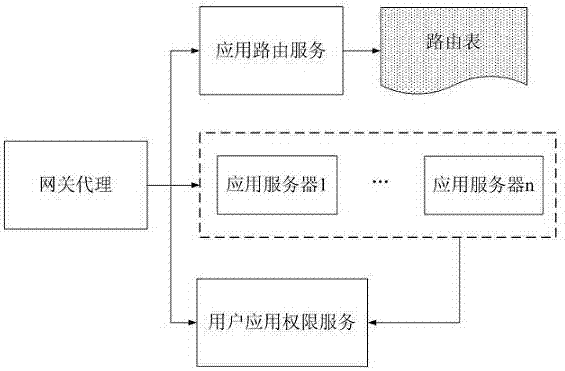
[0032] Cloud application provider based on the present invention in figure 2 The following service roles shown in to implement access control to cloud applications, including: gateway agent, routing service module, user application permissi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com