System and method for virtual identity library entering inquiry
A technology of virtual identity and query method, which is applied in the field of virtual identity storage query system, can solve the problems of inability to follow up cases in time, inconvenience, and effective management and control of personnel who cannot access the Internet, and achieve the effect of improving network combat capability and efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
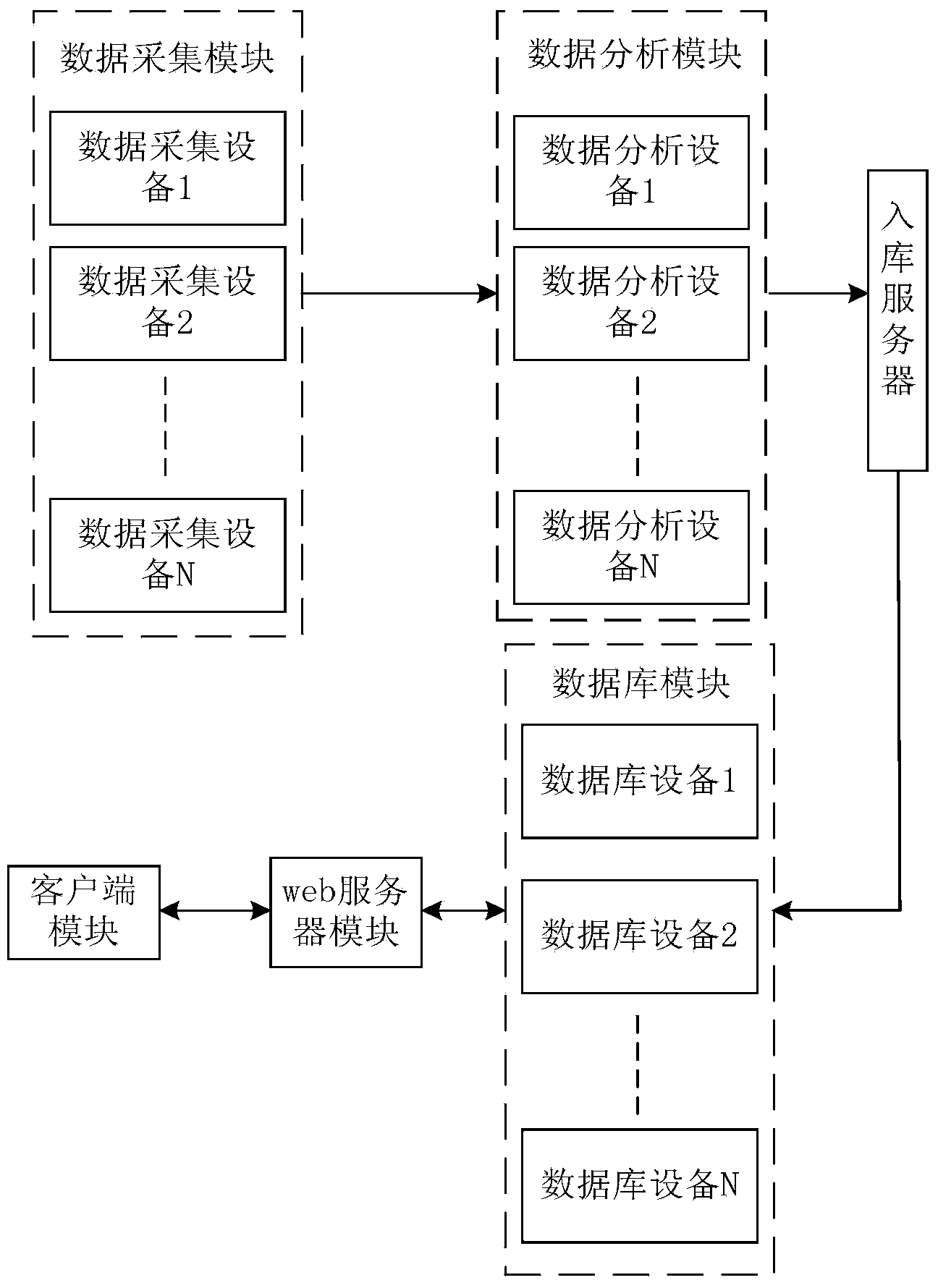
[0022] Please refer to figure 1 As shown, a preferred embodiment of the virtual identity storage query method of the present invention includes the following steps:
[0023] Step 1, utilize the cluster of data collection equipments to collect respectively N virtual identity data of Internet mirror image, N is a natural number; Described virtual identity data comprises online identity information (for example information such as online card number, email account number), place information (such as place Information such as address and surrounding environment), specific group information (such as specific area group, specific age group, etc.), and identity activity track information (such as frequent occurrence time, place, etc.);
[0024] Step 2. Use the data analysis equipment cluster to analyze the collected N virtual identity data, mainly including integrating and analyzing the collected information, and extracting valid virtual identity data (such as QQ account, email accou...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com