A Memory Forensics Method Based on Kernel Object Link Relationship
A technology of kernel objects and link relationships, applied in memory systems, instruments, electrical and digital data processing, etc., can solve problems such as data corruption, achieve good accuracy, overcome uncertainty and slow speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0050] Exemplary embodiments of the present disclosure will be described in more detail below with reference to the accompanying drawings, but are not limited thereto.
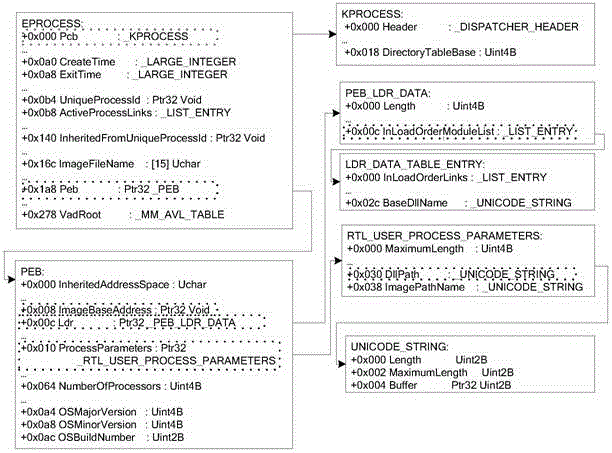
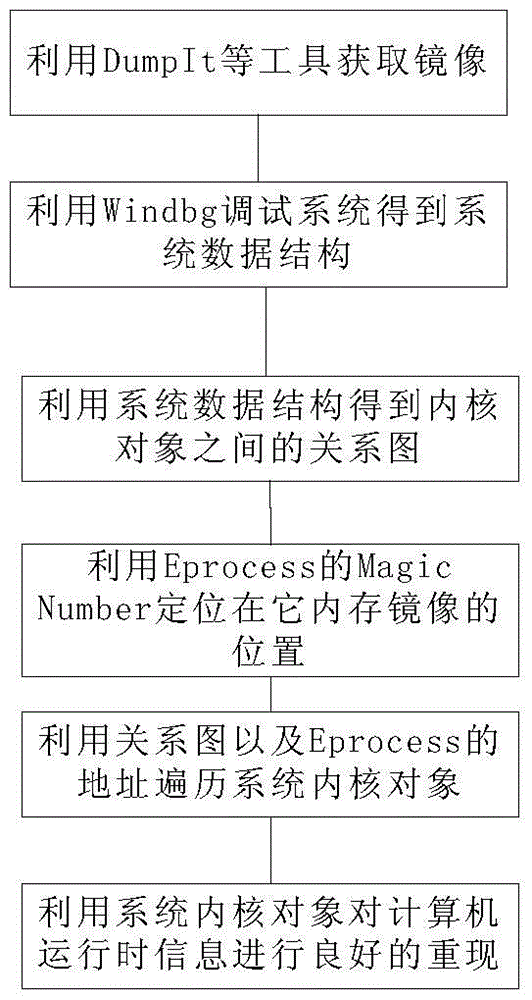
[0051] figure 1 It is a flow chart of a memory forensics method based on kernel object link relationship according to an embodiment of the present invention. Such as figure 1 As shown, a memory forensics method based on the link relationship of kernel objects according to an embodiment of the present invention includes: using DumpIt to obtain a memory image, using Windbg to debug the same version system of the system to be forensic or the forensics system to obtain the data structure of the system, and using the system data structure Get the relationship diagram between kernel objects, use the Magic Number of Eprocess to successfully locate its physical location in the memory mirror, use the relationship diagram between kernel objects to traverse all kernel objects in the system through the physical locatio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com