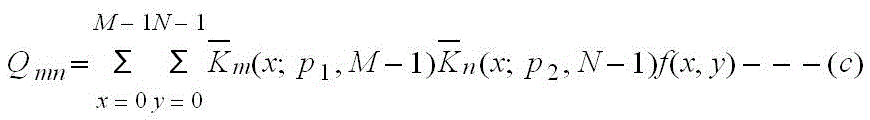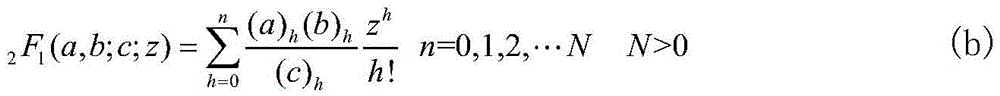Patents
Literature
37 results about "Computer forensics" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Computer forensics (also known as computer forensic science) is a branch of digital forensic science pertaining to evidence found in computers and digital storage media. The goal of computer forensics is to examine digital media in a forensically sound manner with the aim of identifying, preserving, recovering, analyzing and presenting facts and opinions about the digital information.
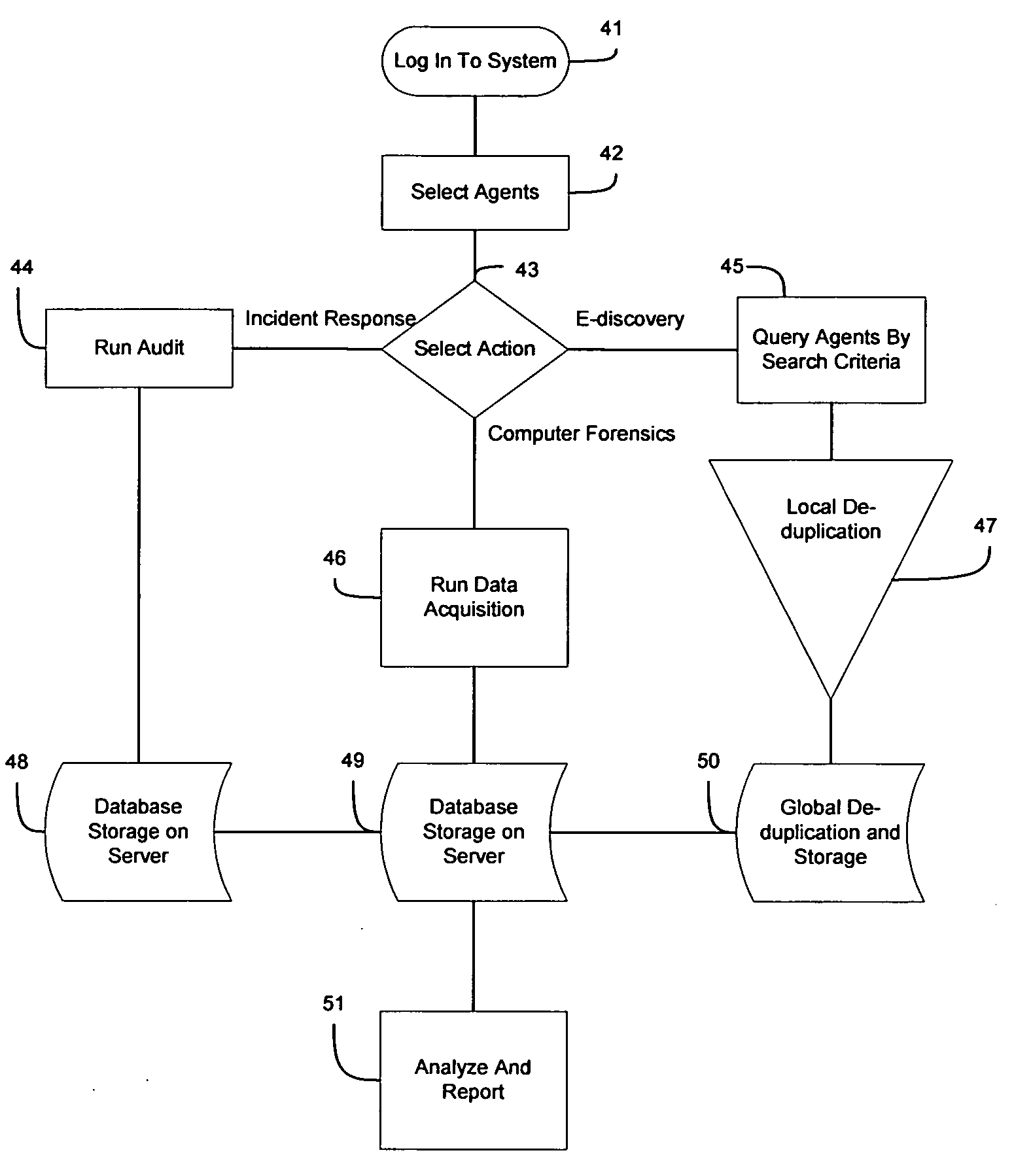
Computer forensics, e-discovery and incident response methods and systems
InactiveUS20090164522A1Secure transmissionCommunication securityMultiple digital computer combinationsTransmissionUser inputElectronic discovery
Systems and methods for collection of volatile forensic data from active systems are described. In an embodiment of the methods, a selected set of forensics data items can be selected. Runtime code capable of launching data collection modules from a removable storage device with little or no user input is generated and stored on the device. The collection of forensic data can then be accomplished covertly using the removable storage device by a person with minimal training. In another embodiment, pre-deployed agents in communication with servers and controlled by console software can collect forensic data covertly according to schedule, immediately at the command of an analyst using a remote administrative console, or in response to a triggering event.
Owner:E FENSE
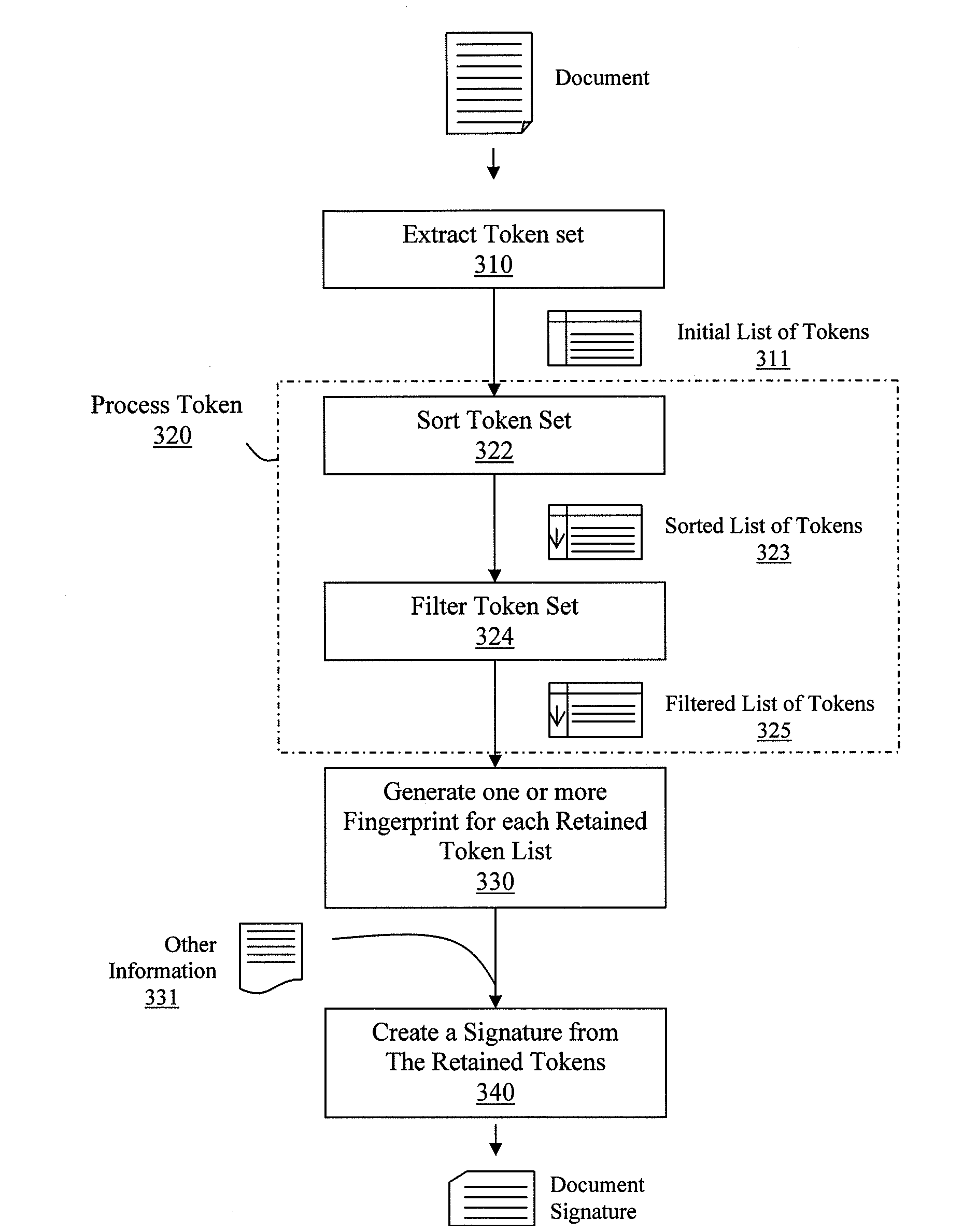
Automated forensic document signatures
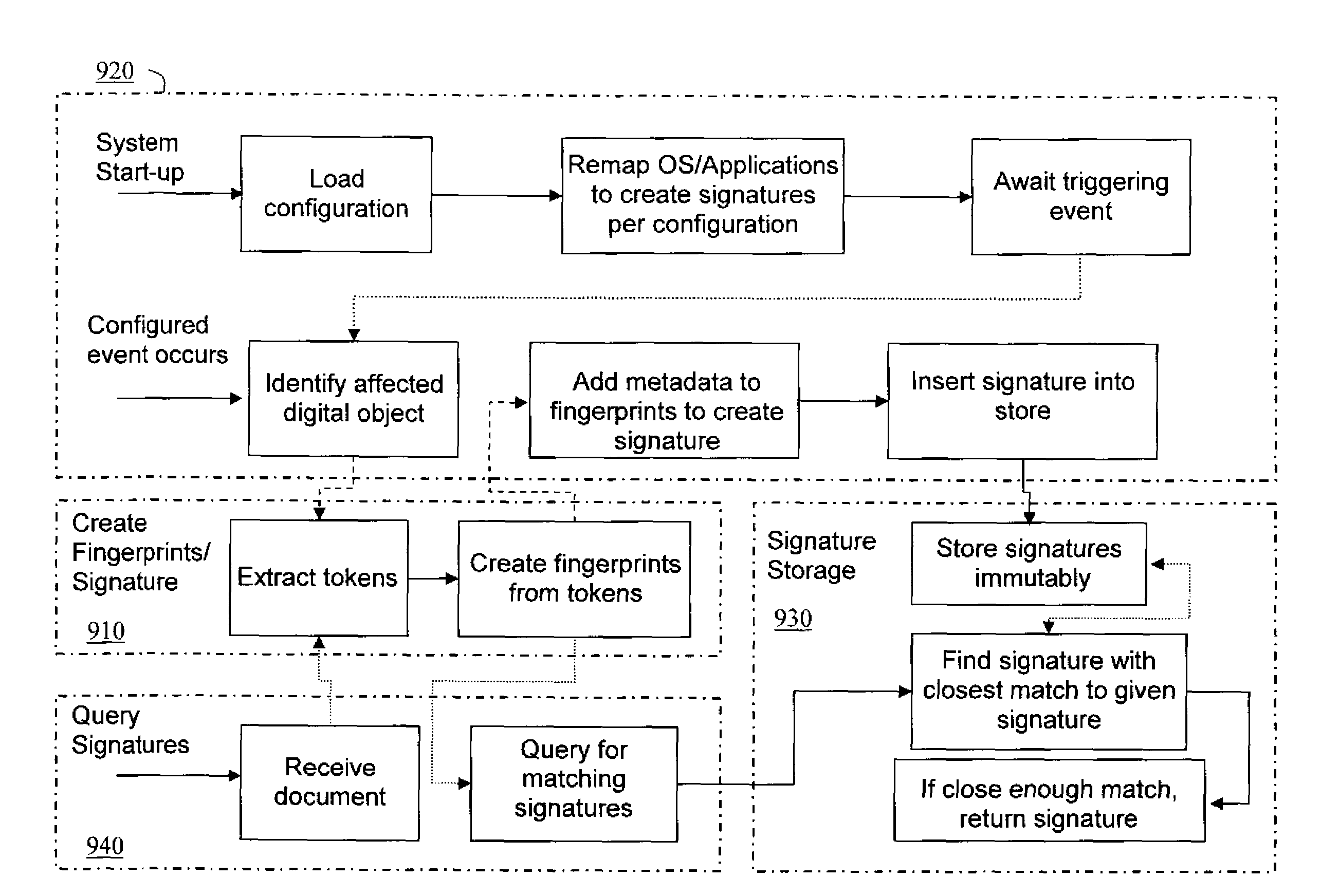
ActiveUS20100287196A1Facilitate methodDigital data processing detailsPlatform integrity maintainanceDocument preparationDigital fingerprint
Owner:GEORGETOWN UNIV
Forensics tool for examination and recovery and computer data
InactiveUS20070226170A1Avoid modificationAvoid creatingData processing applicationsError detection/correctionElectronic discoveryFile size
The present invention concerns an electronic forensic tool for conducting electronic discovery and computer forensic analysis. The present invention allows a non-technical person such as a non-forensic expert to conduct electronic discovery and thereby obviate the need for an expert in many situations. The present invention allows for electronic discovery in a forensically sound manner. The present invention also concerns a business method for electronic discovery involving a software program and a command server for generating expanded functionality. The client software may be distributed at minimal or no cost, preferably as a CD. Using the client software, a user boots a target machine to determine whether a target machine contains data of interest. The client software will, however, only display limited data such as file information, date, last modified, and file size. To access and examine the actual underlying data, the user must obtain additional functionality, e.g. by purchasing a command block from the control server. The additional functionality will allow the client program to extract the data of interest or the entire contents of the target machine to an external device for further analysis.
Owner:SUN DAVID
Automated forensic document signatures
ActiveUS20090164517A1Facilitate methodDigital data processing detailsUser identity/authority verificationDigital signatureMisuse detection
Methods and systems are provided for a proactive approach for computer forensic investigations. The invention allows organizations anticipating the need for forensic analysis to prepare in advance. Digital signatures are generated proactively for a specified target. The digital signature represents a digest of the content of the target, and can be readily stored. Searching and comparing digital signatures allows quick and accurate identification of targets having identical or similar content. Computational and storage costs are expended in advance, which allow more efficient computer forensic investigations. The present invention can be applied to numerous applications, such as computer forensic evidence gathering, misuse detection, network intrusion detection, and unauthorized network traffic detection and prevention.
Owner:GEORGETOWN UNIV
Dynamic user behavior-based cloud forensics method and dynamic user behavior-based cloud forensics system
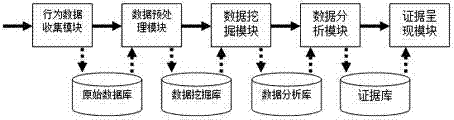
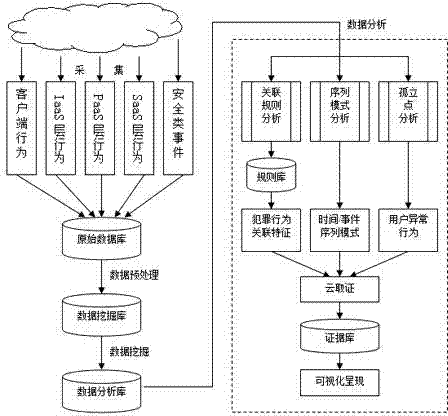
The invention discloses a dynamic user behavior-based cloud forensics method and a dynamic user behavior-based cloud forensics system; the formalized definition of dynamic user behavior is put forward as basis; and the method comprises the steps of: collecting dynamic user behavior and behavior data, and storing the behavior data as primary evidence data; carrying out data integration, data cleaning and data mining to form forensic analysis data, and storing the forensic analysis data into a data analysis library (key value database); using Map Reduce to carry out correlation analysis, sequence pattern analysis and isolated point analysis on the forensic analysis data, and digging out the potential user behavior patterns and the possible aggressive behavior to form forensic evidence; and displaying the forensic evidence in a visual way. The high performance computing power of cloud computing and large-scale distributed-memory environment are applied into computer forensic analysis, so that various problems in cloud computing forensics can be solved.
Owner:INSPUR GROUP CO LTD
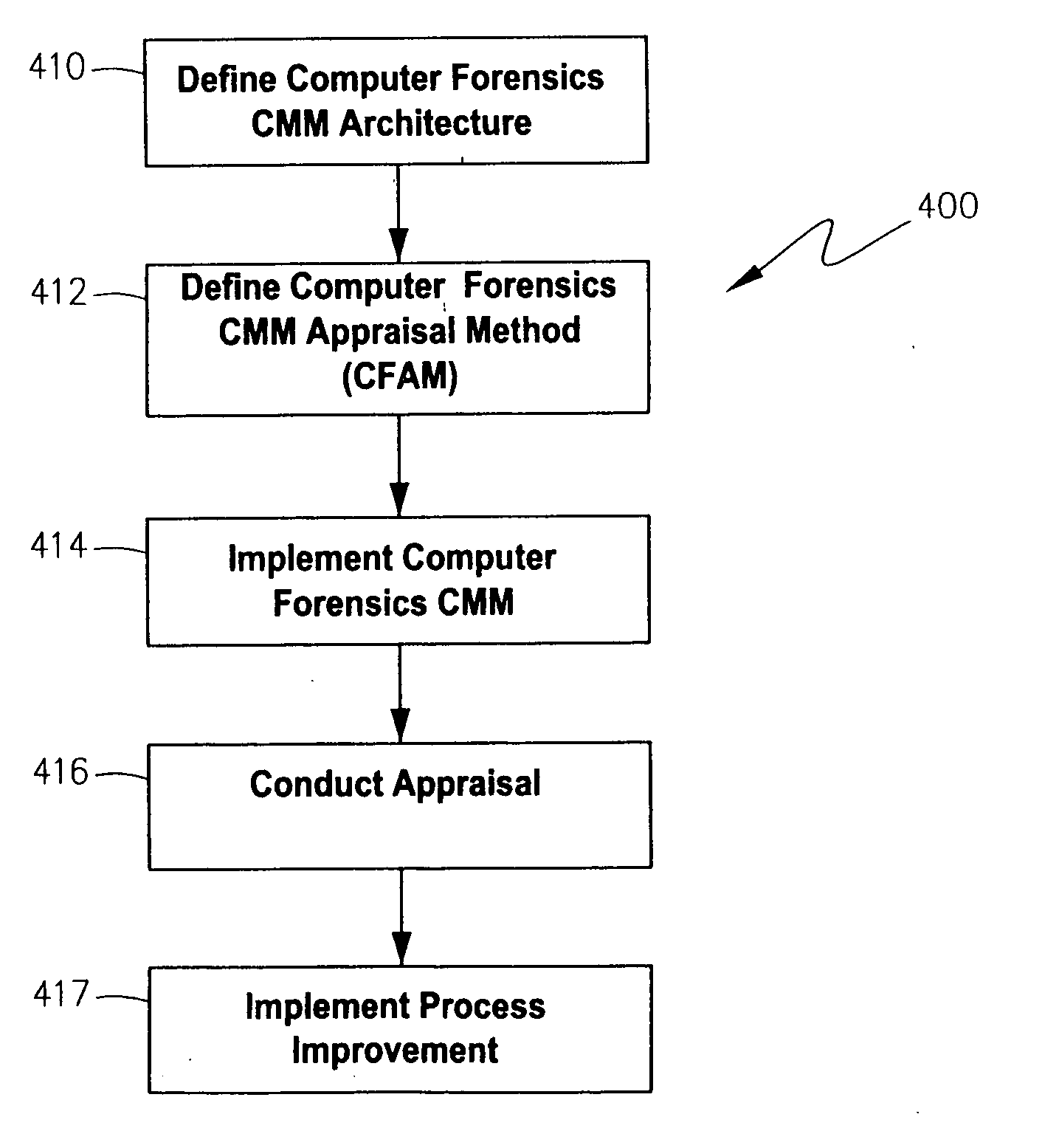
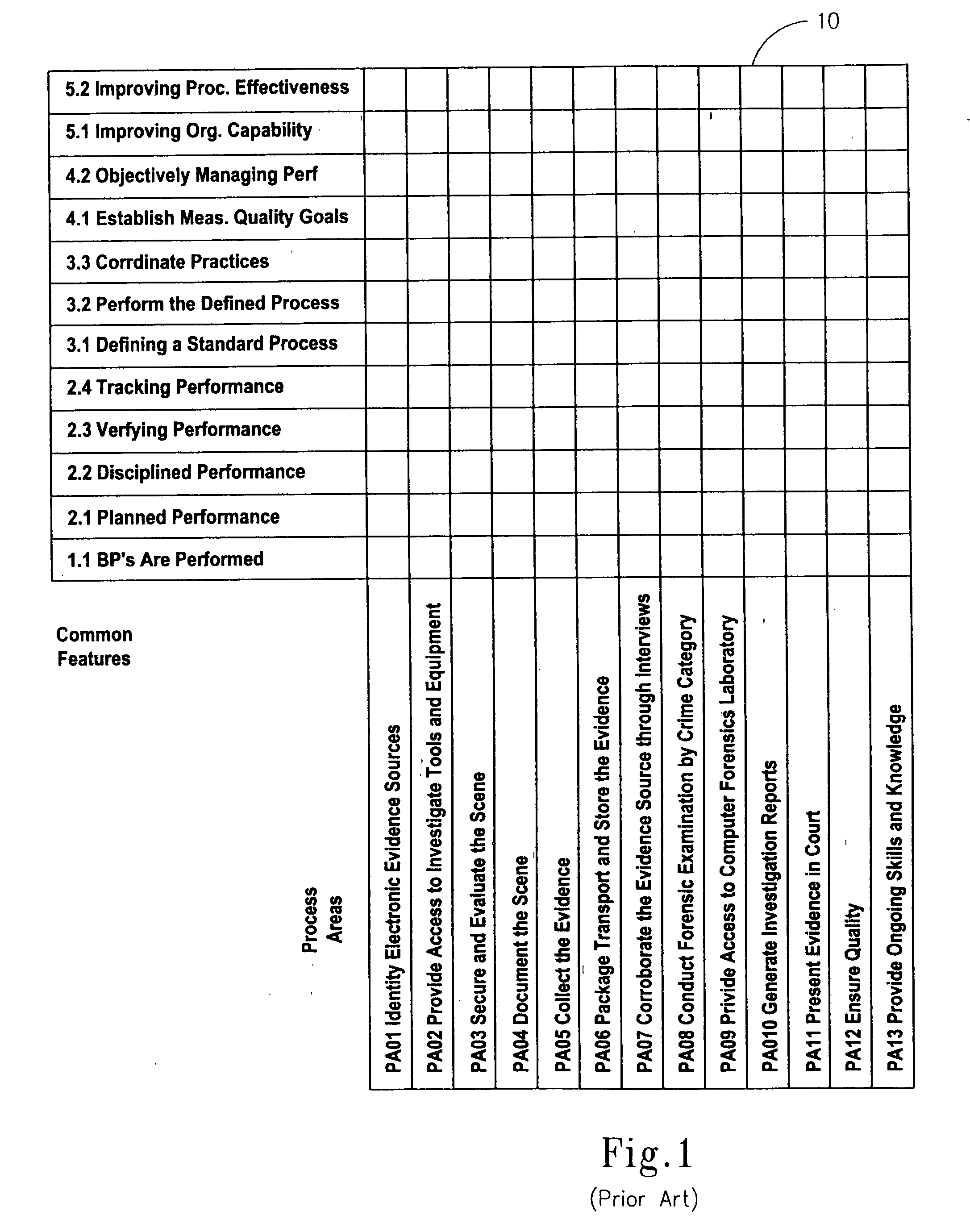
Methodology for assessing the maturity and capability of an organization's computer forensics processes
A method for assessing capability and maturity of an organization's computer forensics processes defines an architecture for a computer forensics capability and maturity model (CMM), a computer forensics CMM appraisal method, implements the computer forensics CMM for improving computer forensics processes within the organization, and conducts an appraisal of the organization according to the CMM appraisal method.
Owner:SYTEX
Forensics tool for examination and recovery of computer data
InactiveUS20070168455A1Increase costComputer security arrangementsMultiple digital computer combinationsElectronic discoveryFile size
Owner:SUN DAVID
Computer forensic tool
InactiveUS8793795B1Speed up analysis dataEasy to analyzeMemory loss protectionError detection/correctionData transmissionComputer science
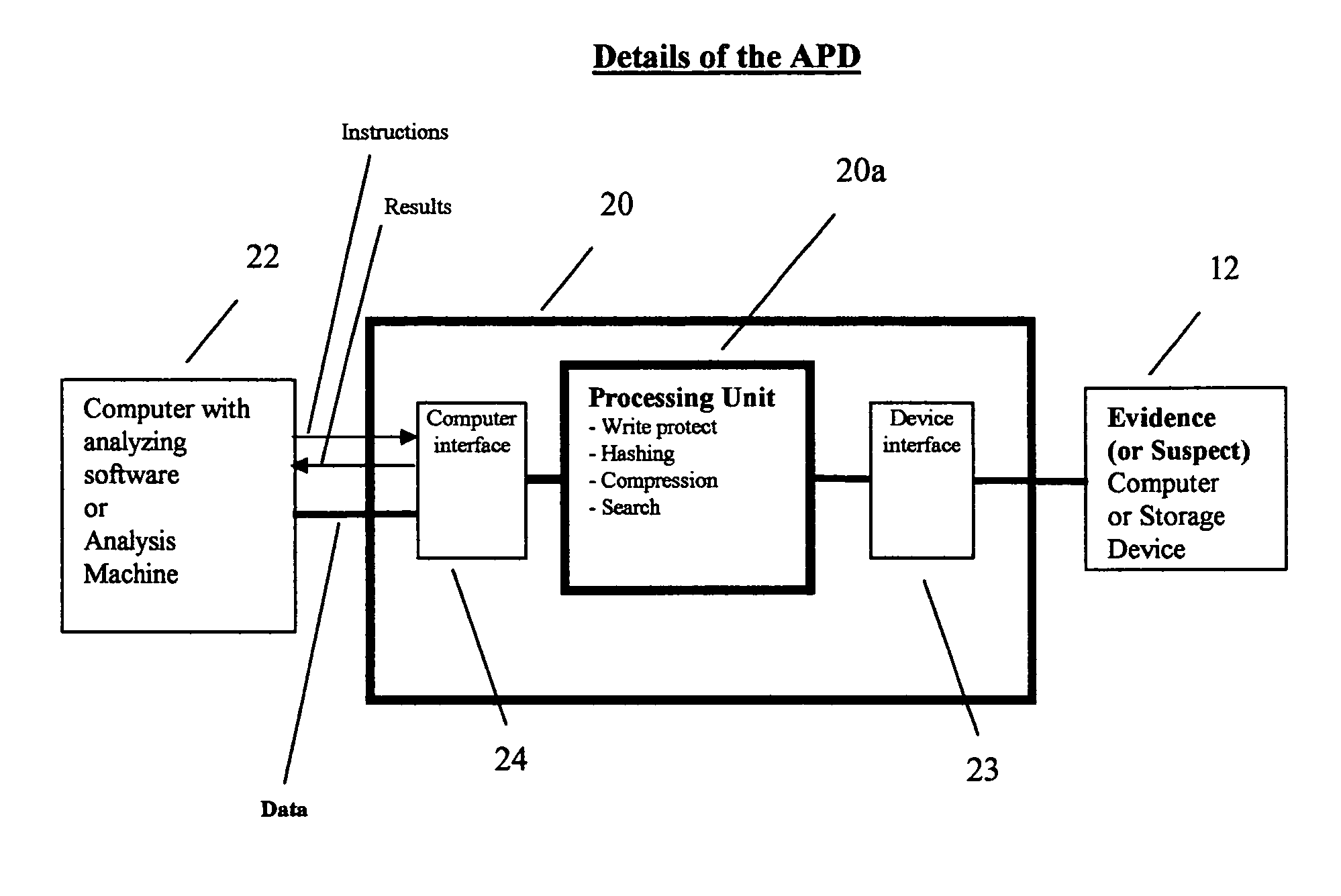
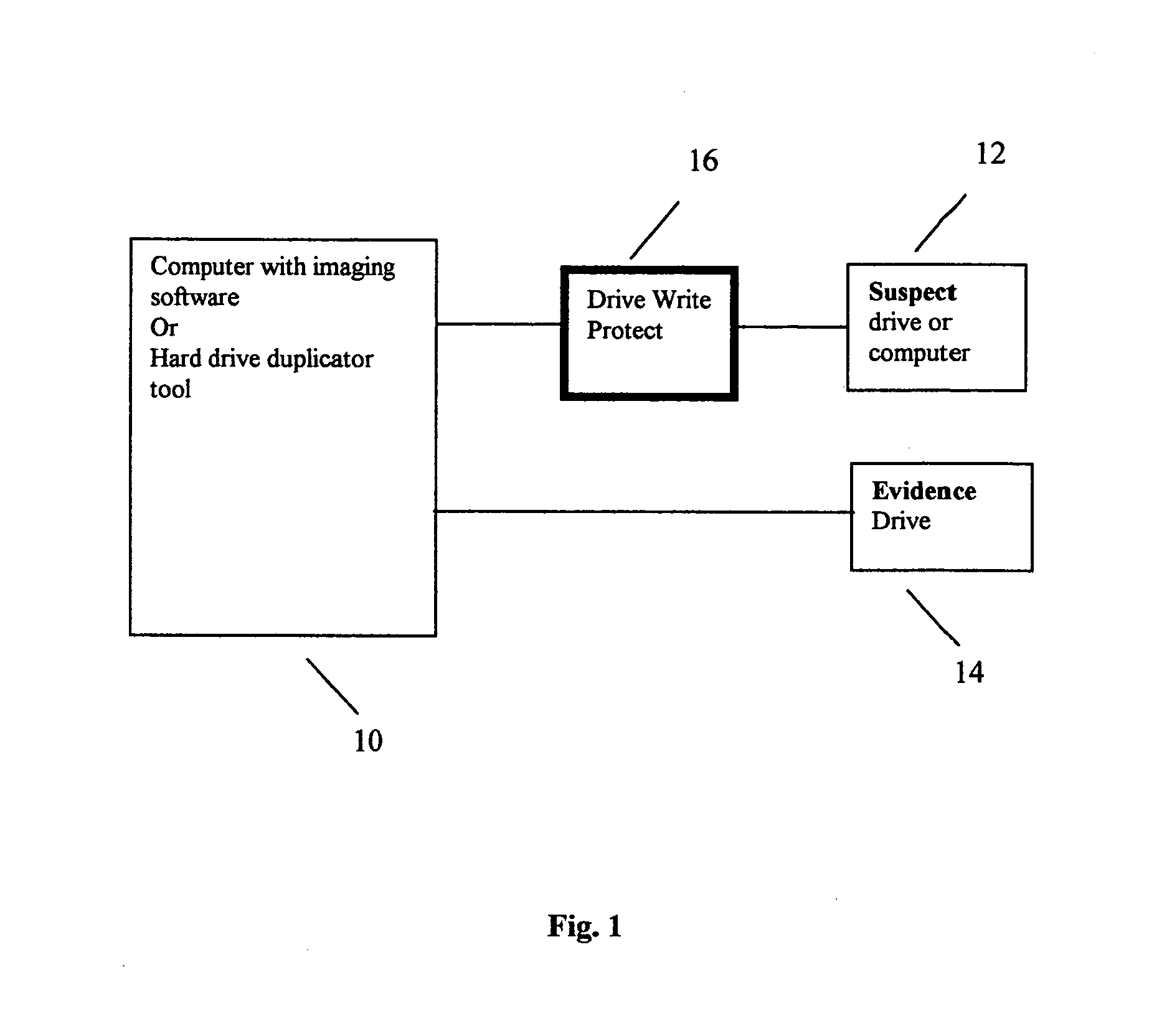
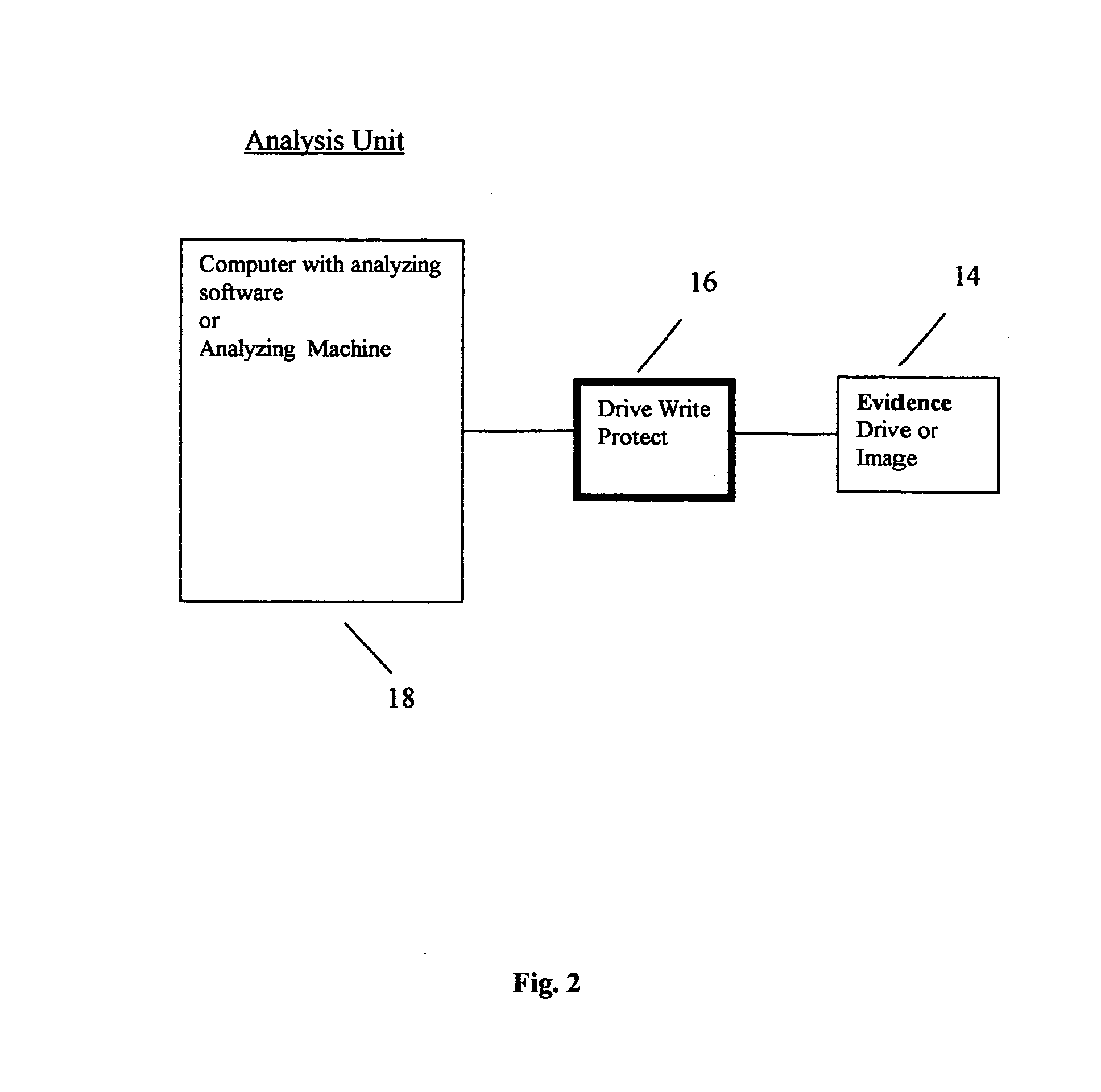
A computer forensic accelerator engine designed to speed up the forensic analysis process is disclosed. It is a device for use with an analysis device to analyze data on a suspect computer device, and includes a first interface for connecting to the suspect computer device, a second interface for connecting to the analysis device, and a processing unit programmed to read data from the suspect device via the first interface, perform analysis on the data, transmit the data to the analysis device via the second interface, and transmit results of the analysis to the analysis device via the second interface. A drive write protect module may be integrated in the computer forensic accelerator engine. The computer forensic accelerator engine allows data read from the suspect drive to be analyzed while acquiring the data. Also disclosed is a computer forensic analysis system and method using the computer forensic accelerator engine.
Owner:INTELLIGENT COMP SOLUTIONS
Forensics tool for examination and recovery of computer data
InactiveUS7640323B2Avoid modificationAvoid creatingComputer security arrangementsMultiple digital computer combinationsElectronic discoveryWorld Wide Web
The present invention is directed to an electronic forensic tool for electronic discovery and computer forensics. The invention allows a user to conduct limited preliminary examination of computers using a client program on a physical memory device, whereby limited information about the examination result is displayed. To further access and examine the actual underlying data, the user must obtain additional functionality by obtaining a command block from a control server. The additional functionality will allow the client program to extract, copy, export, or further access the data of interest.
Owner:SUN DAVID
Forensics tool for examination and recovery and computer data
InactiveUS7644138B2Avoid modificationAvoid creatingData processing applicationsMultiple digital computer combinationsElectronic discoveryComputer science
The present invention is directed to an electronic forensic method for electronic discovery and computer forensics. The invention allows a user to conduct limited preliminary examination of computers using a client program on a physical memory device, whereby limited information about the examination result is displayed. To further access and examine the actual underlying data, the user must obtain additional functionality by obtaining a command block from a control server. The additional functionality will allow the client program to extract, copy, export, or further access the data of interest.
Owner:SUN DAVID
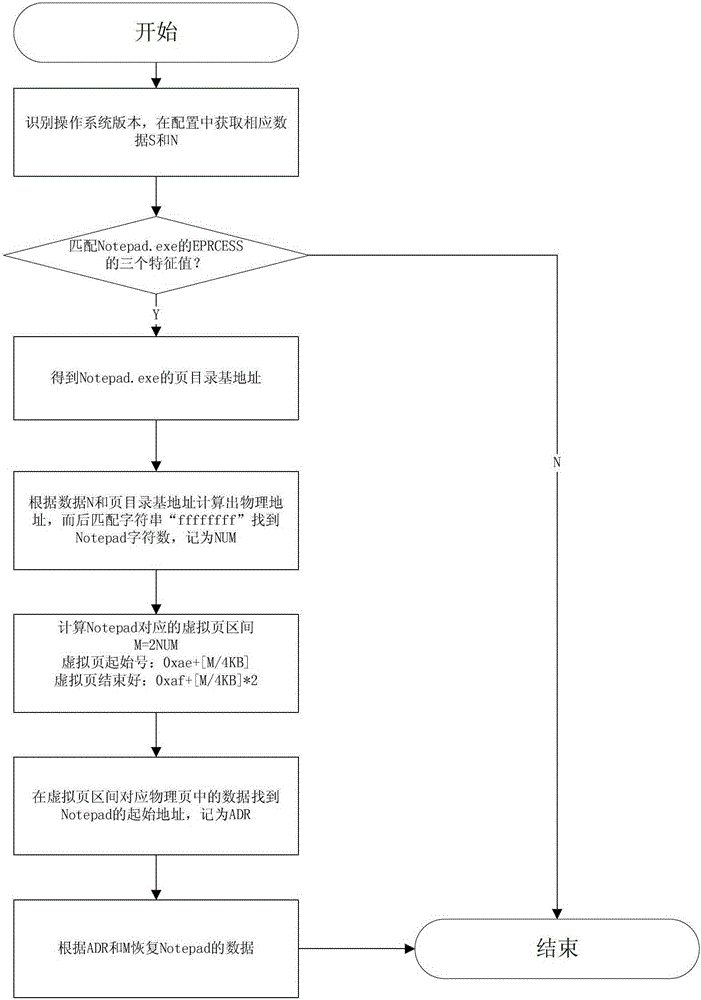
Method for extracting text data file from physical memory image
ActiveCN102945288AAccurately getSpecial data processing applicationsData ingestionOperational system
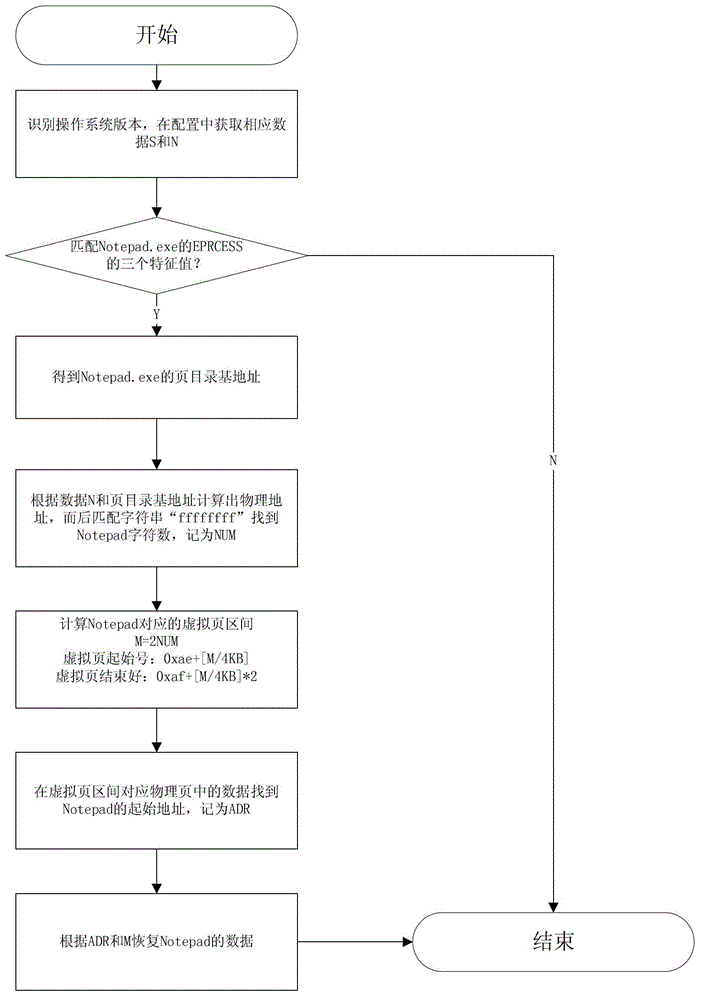
The invention discloses a method for extracting a text data file from a physical memory image. The method comprises the following steps of: searching an eprocess structure of a notepad.exe progress by utilizing characteristic values of the eprocess structure and offset between the characteristic values, and acquiring a page directory base address of the progress; and acquiring text data description information and labeling information in memory, and accurately acquiring the text data in the notepad.exe progress through the principle of converting the address of an operating system. The method can be used for data recovery, data extraction, computer forensic and the like.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Automated forensic document signatures
ActiveUS8280905B2Facilitate methodDigital data processing detailsUser identity/authority verificationDigital signatureMisuse detection
Methods and systems are provided for a proactive approach for computer forensic investigations. The invention allows organizations anticipating the need for forensic analysis to prepare in advance. Digital signatures are generated proactively for a specified target. The digital signature represents a digest of the content of the target, and can be readily stored. Searching and comparing digital signatures allows quick and accurate identification of targets having identical or similar content. Computational and storage costs are expended in advance, which allow more efficient computer forensic investigations. The present invention can be applied to numerous applications, such as computer forensic evidence gathering, misuse detection, network intrusion detection, and unauthorized network traffic detection and prevention.
Owner:GEORGETOWN UNIV
SQLite data recovery method applicable to merging of non-integral primary keys with free blocks
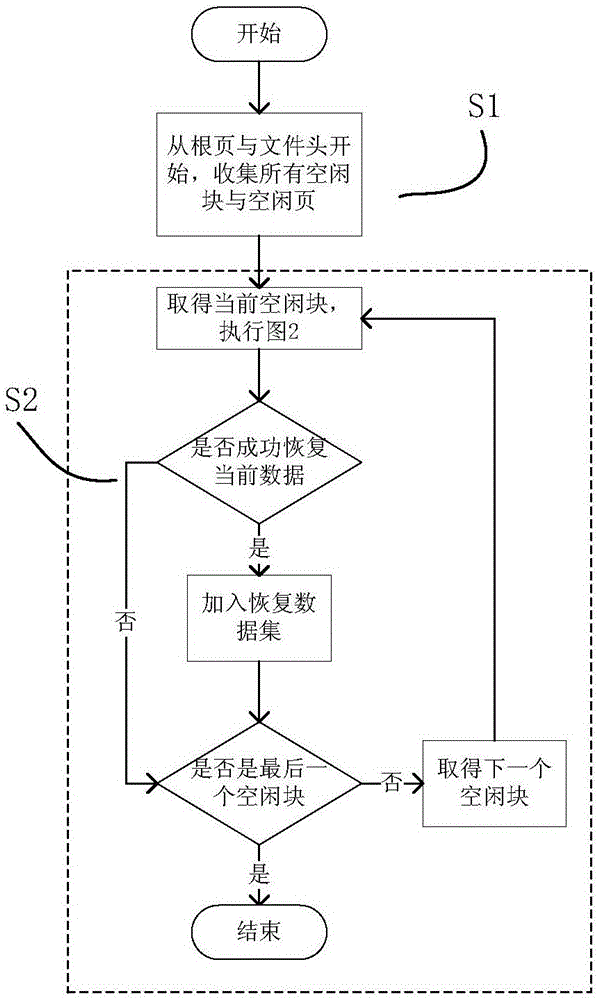
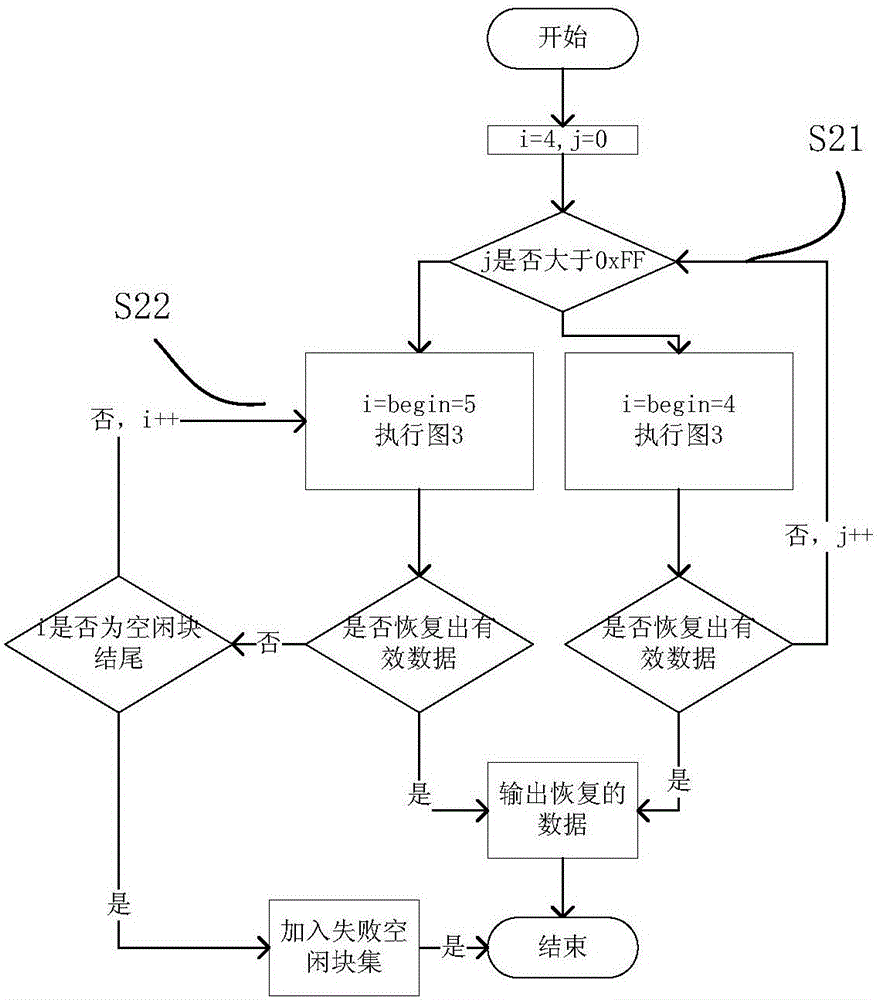
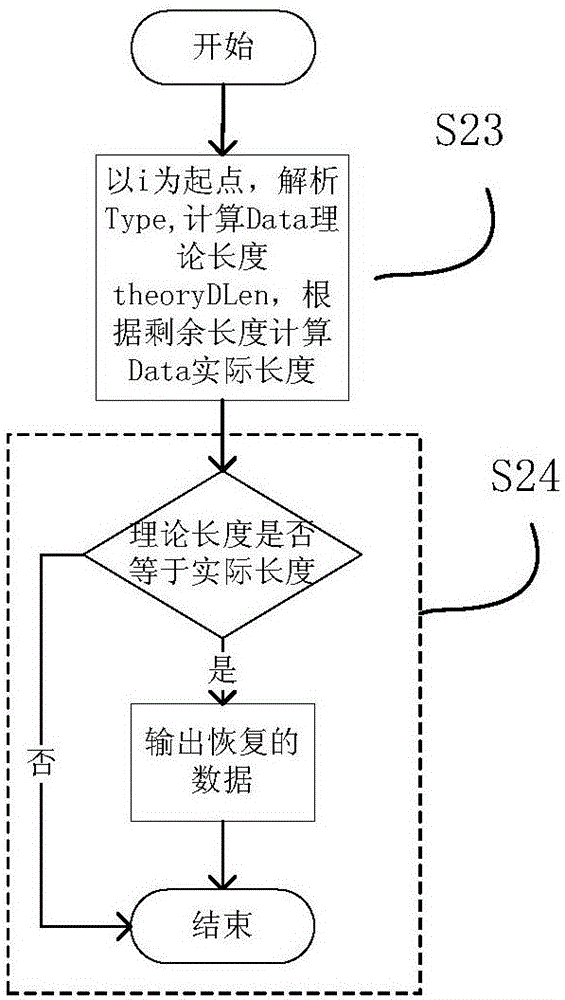
ActiveCN106844607AMake up for the lack of analytical abilityImprove recovery rateRelational databasesRedundant operation error correctionData fieldDatabase file
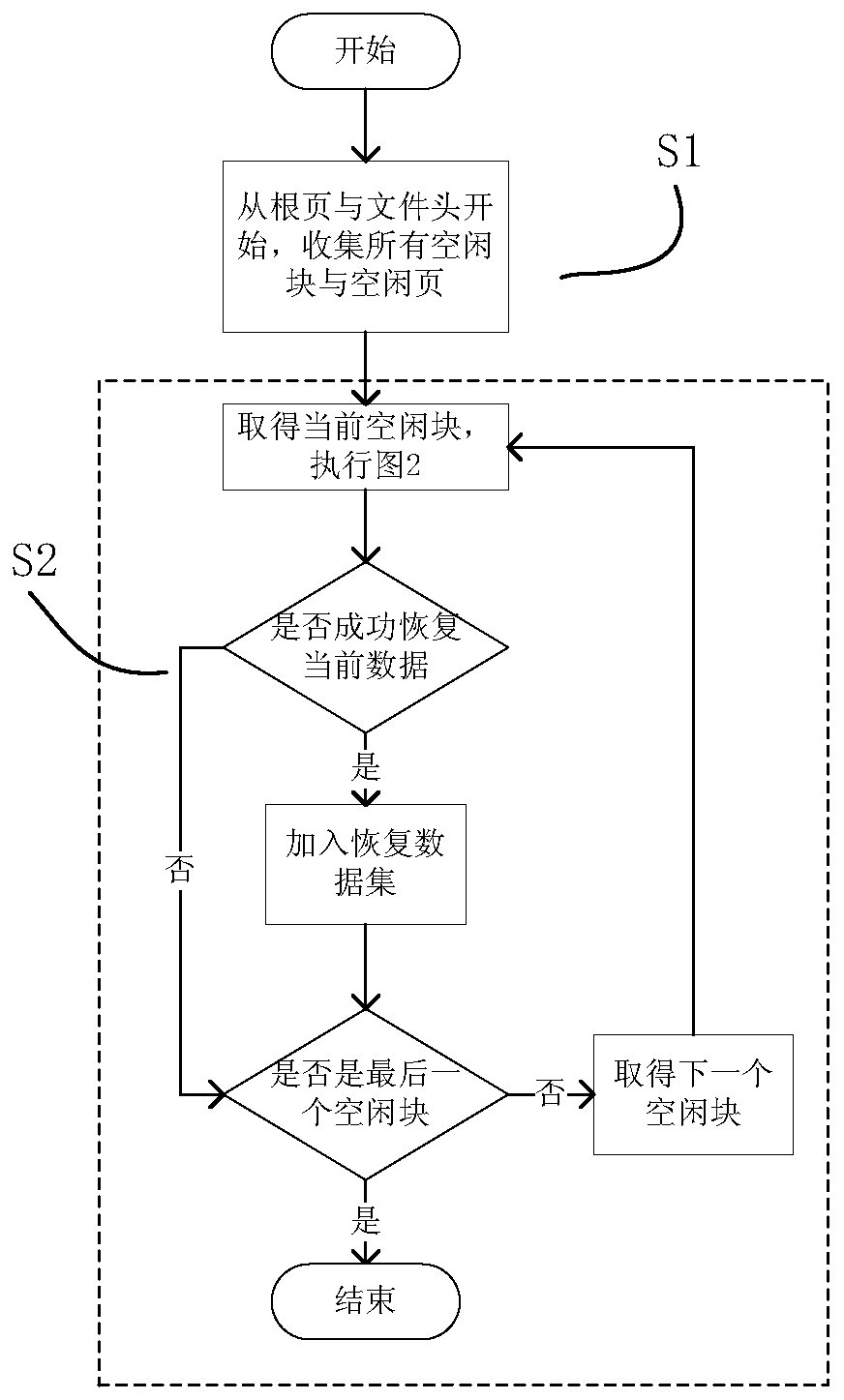
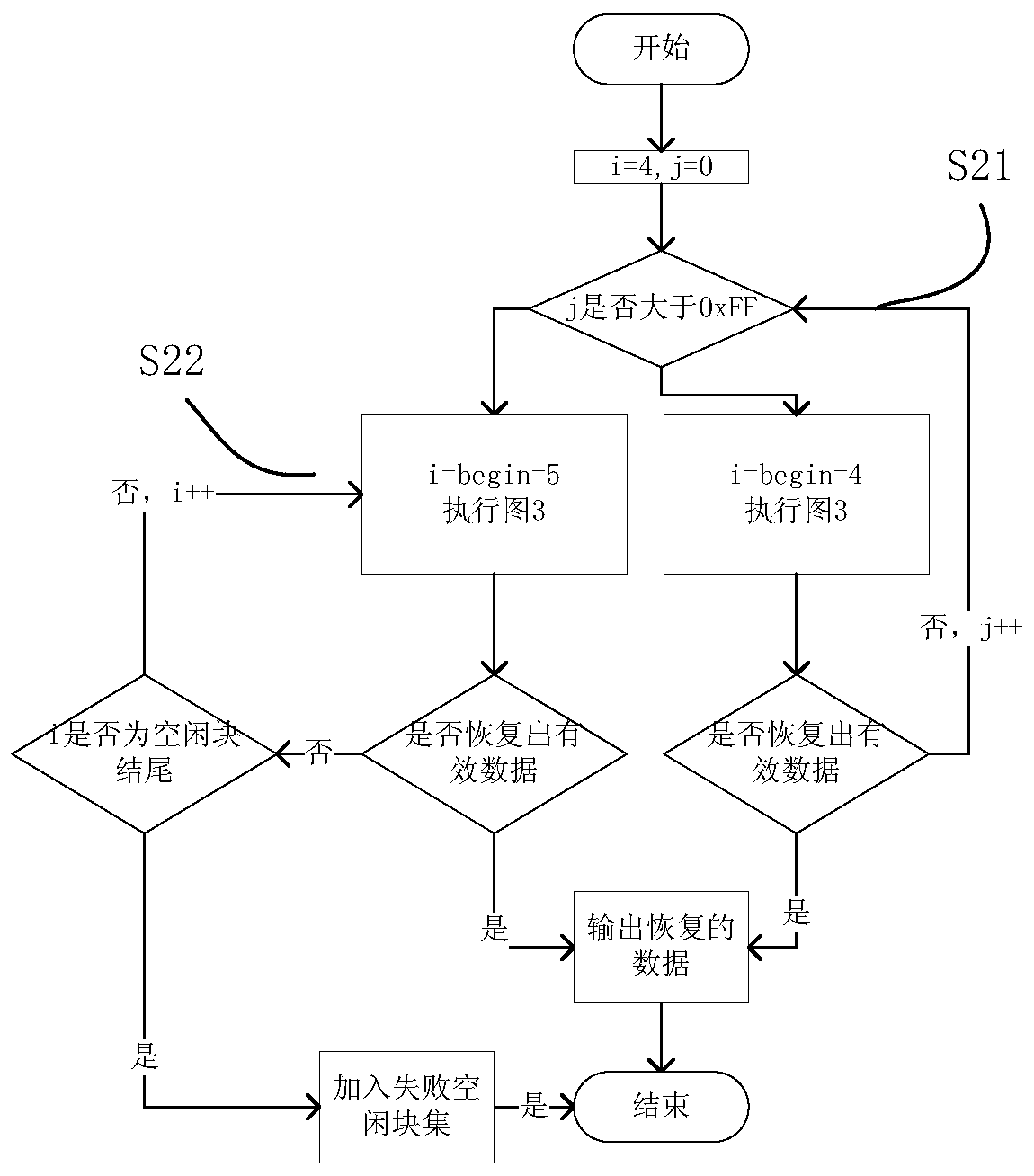
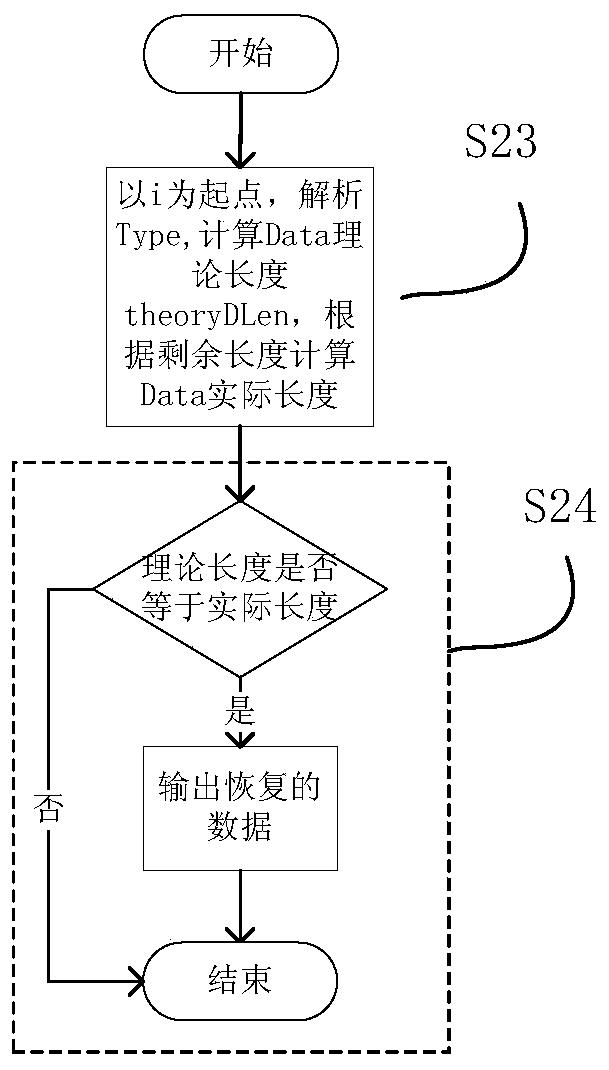
The invention provides an SQLite data recovery method applicable to merging of non-integral primary keys and free blocks and relates to the field of computer forensics. The method includes the steps of 1), starting from a root page and a file header to search all the free blocks and free pages; 2), analyzing difference of cell layout of integral primary keys and the non-integral primary keys as well as difference of meanings of bytes, temporarily assuming each free block contains one cell, calculating information of types covered, analyzing the type information and a data field and performing data recovery; 3), for the free blocks cannot pass the step 2), believing that each of the free blocks contains multiple cell, pre-estimating length of the cells stored in the free blocks is from 4 to free block length on the basis of splitting and verifying, and judging pre-estimated values with a single free block extraction module; 4), in response to decreasing of the free blocks due to B+tree reorganization, extracting the data from the free pages collected in the step 1). With the method, the data deleted can be easily recovered from SQLite3 database files, and the data is provided for follow-up electronic forensics work.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
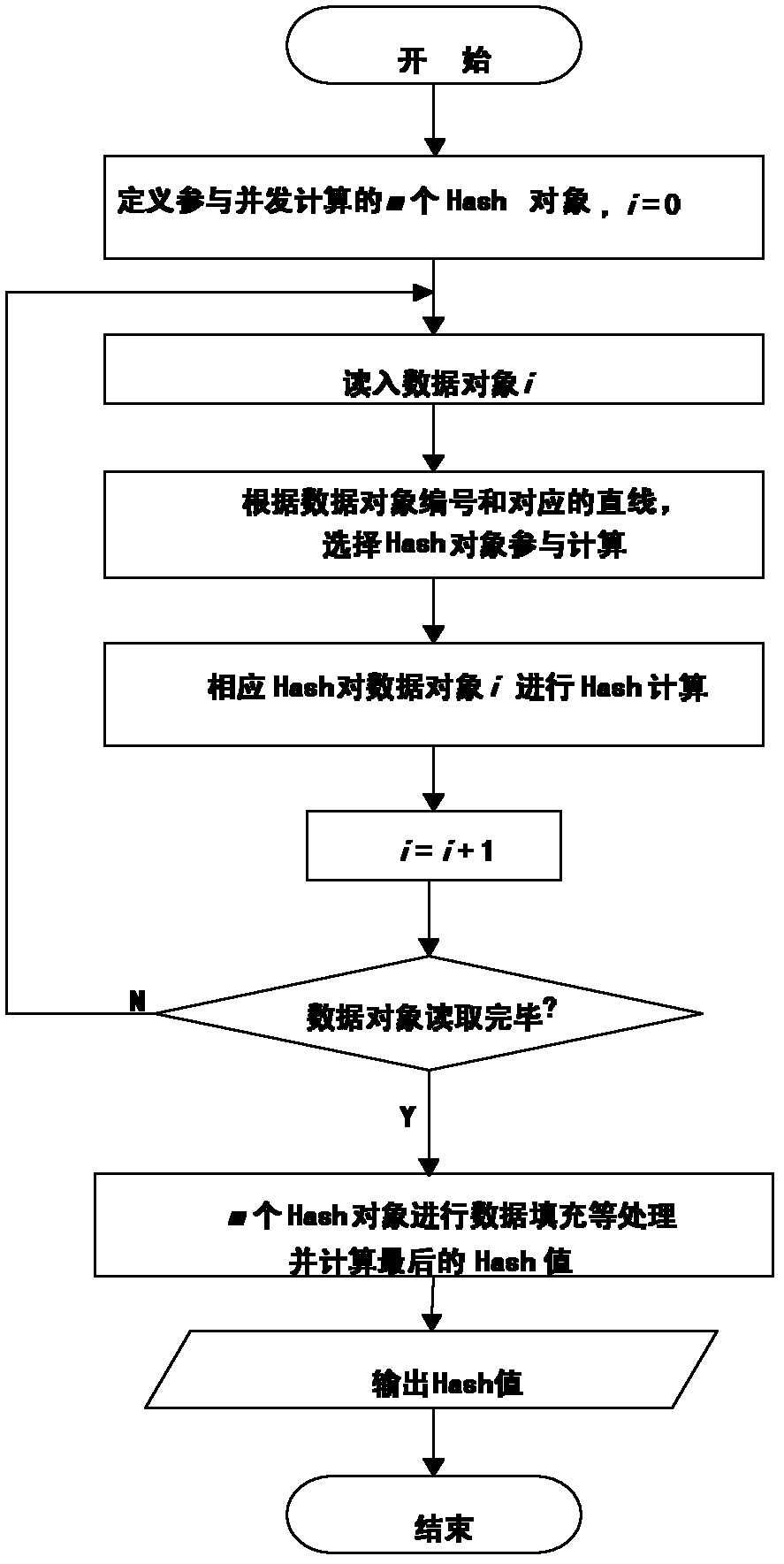
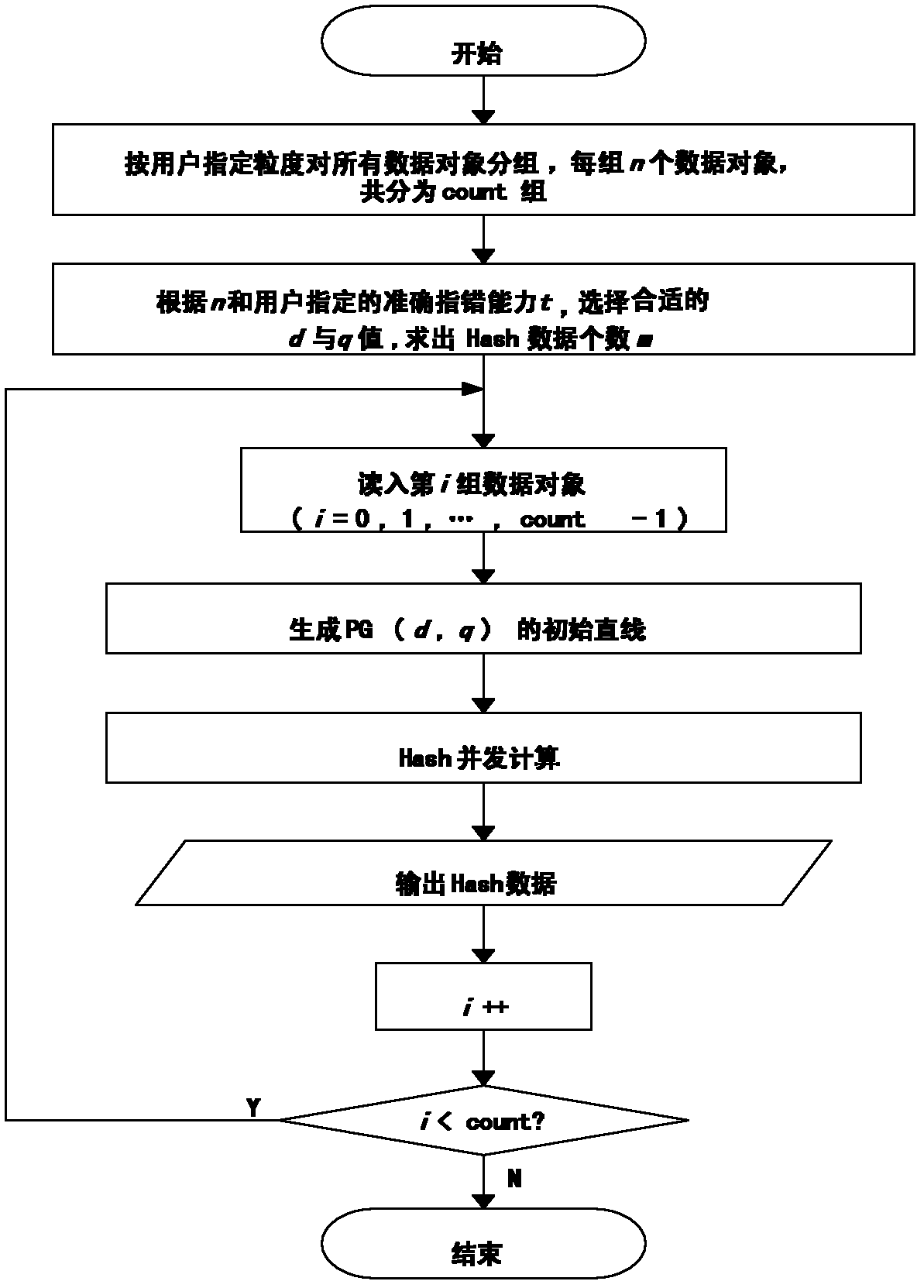
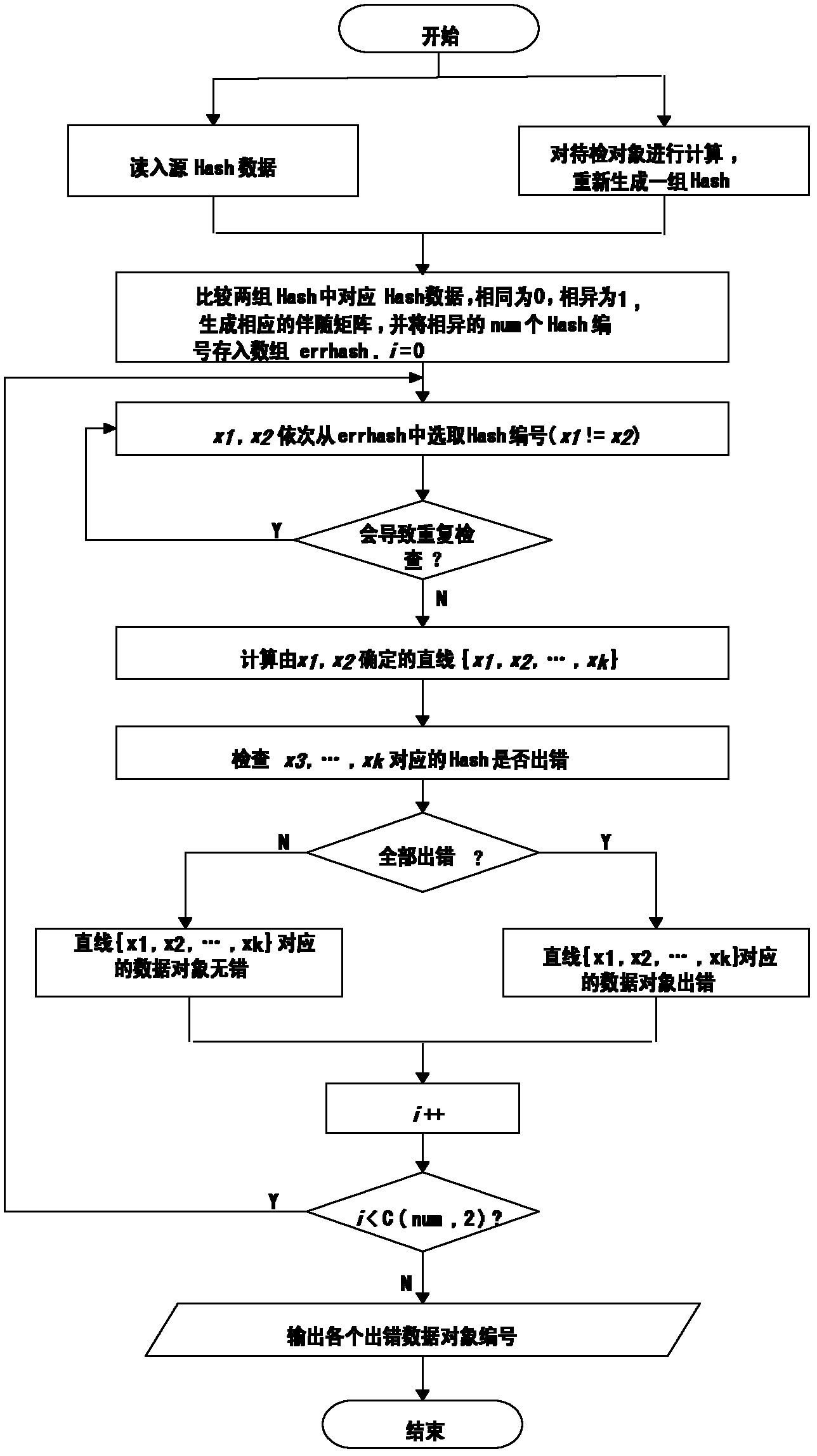
Method for detecting integration of high-efficiency finegrained data
ActiveCN102222202AReduce catastrophic effects of failureDoes not affect practical applicationDigital data protectionData integrityData error
The invention discloses a method for detecting the integration of high-efficiency finegrained data, relating to a method for detecting data integrity in the fields of data security and computer forensics. In the method, through encoding design based on the association and combination relation of lines and points in finite projective geometry, each supervision Hash corresponds to a point in a finite projective space, data objects to be supervised correspond to lines in the finite projective space, the point-line relation is utilized to determine the Hash supervision relation, multiple errors in a group of data objects can be accurately indicated, the compression rate is higher, the processing requirement of mass data can be met, and the storage space of Hash data and the network bandwidth required for Hash data transmission are saved. The method can be used for integration indication of forensic mapping in the computer forensics, and is applicable to integration detection of mass data,electronic data and computer evidences of data processing service department and judicial department, and also applicable to the occasions needing finegrained integration detection and fewer data error indication.
Owner:重庆信科通信建设监理咨询有限公司
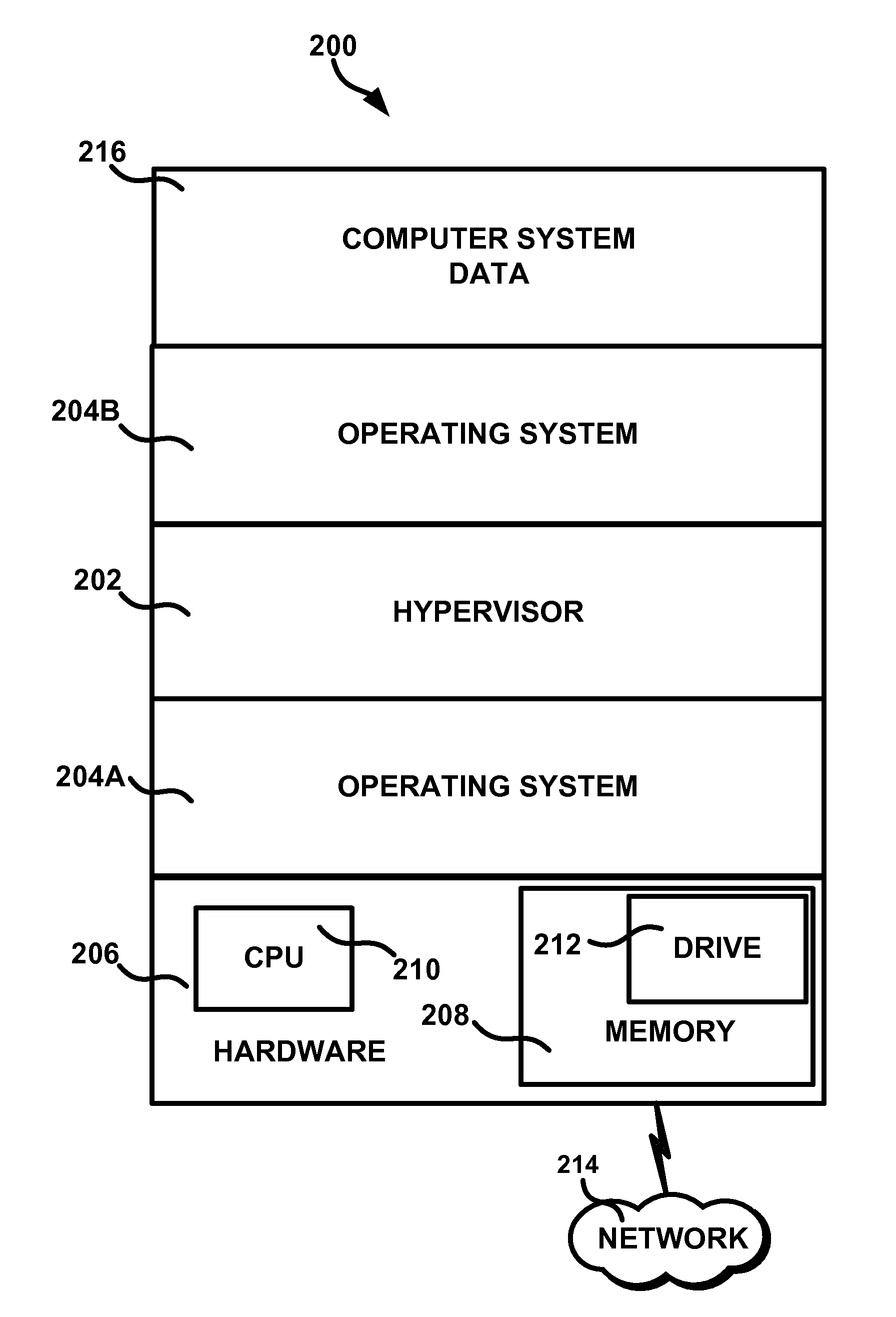
System and method for live computer forensics
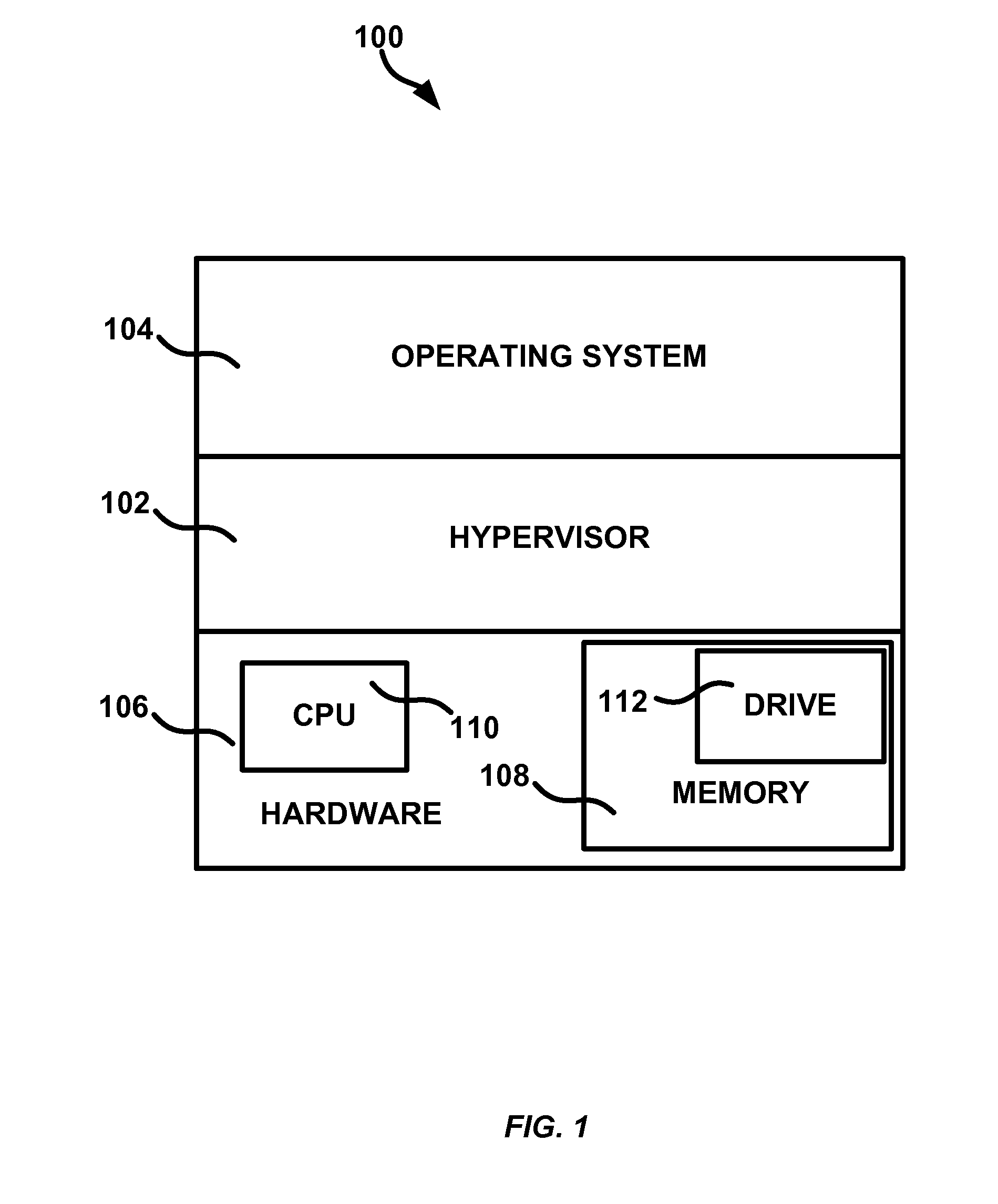
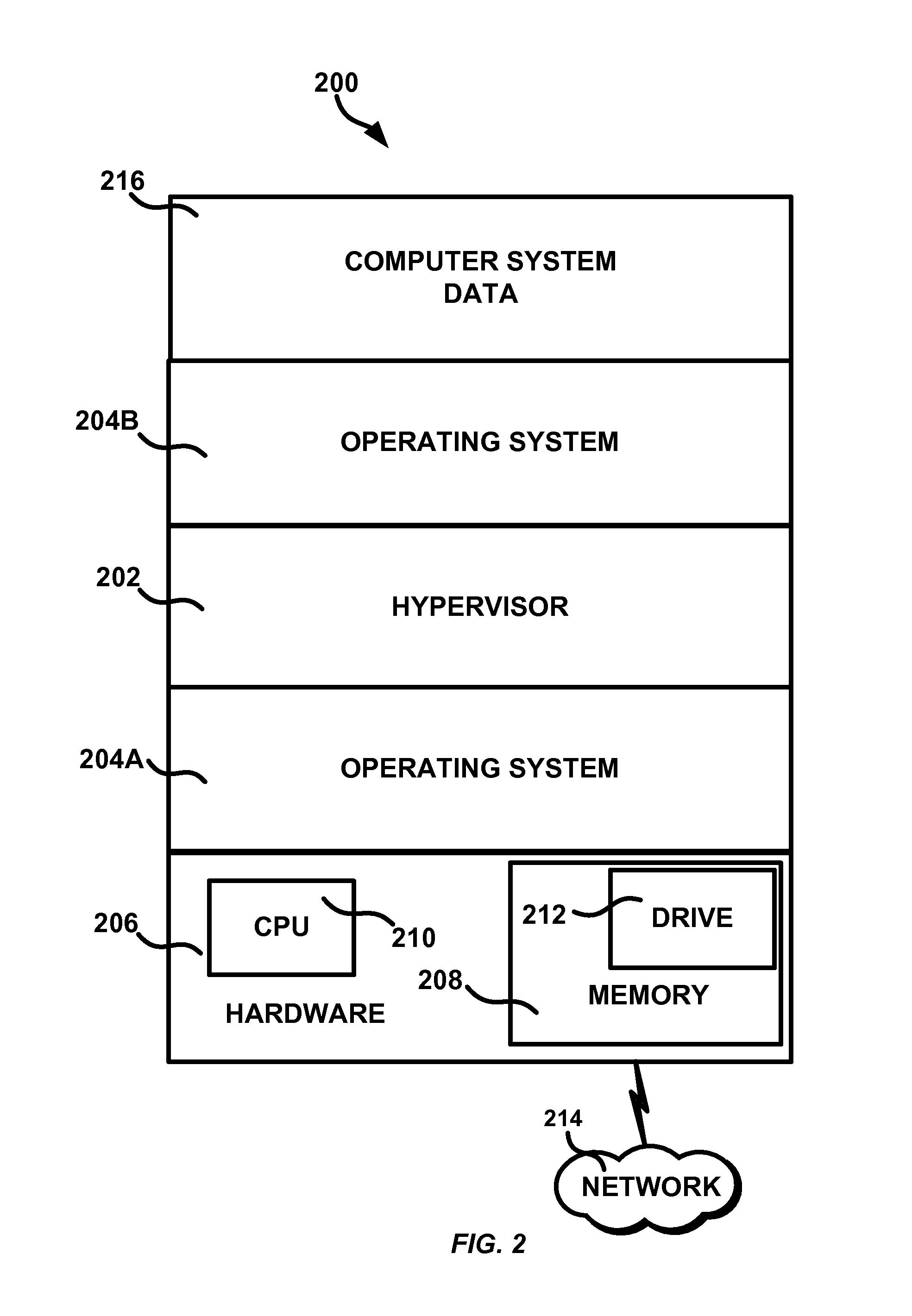
InactiveUS20140068601A1Platform integrity maintainanceSoftware simulation/interpretation/emulationComputerized systemVolatile memory
Embodiments of a system and method for live computer forensics are generally described herein. The system can include a first hypervisor configured to halt a computer system, the computer system including a central processing unit, a drive, a volatile memory, and a non-volatile memory. The first hypervisor can be configured to collect data representative of the state of the computer system at the time the computer system was halted. The data representative of the state of the computer system can include the contents of the volatile and non-volatile memory at the time the computer system was halted, wherein at least a portion of the collected data is representative of the state of the central processing unit and the contents of the drive, at the time the computer system was halted.
Owner:RAYTHEON CO
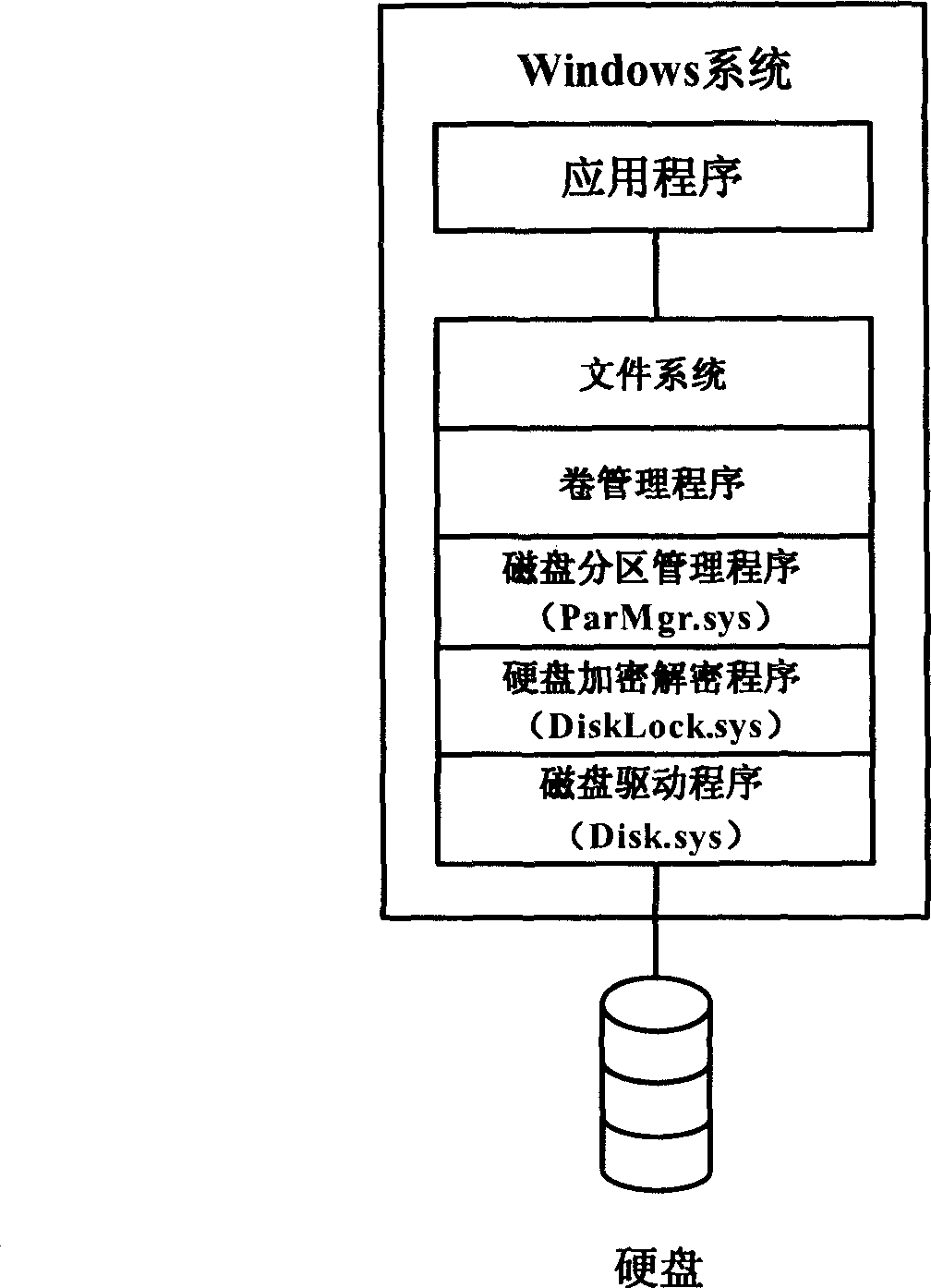
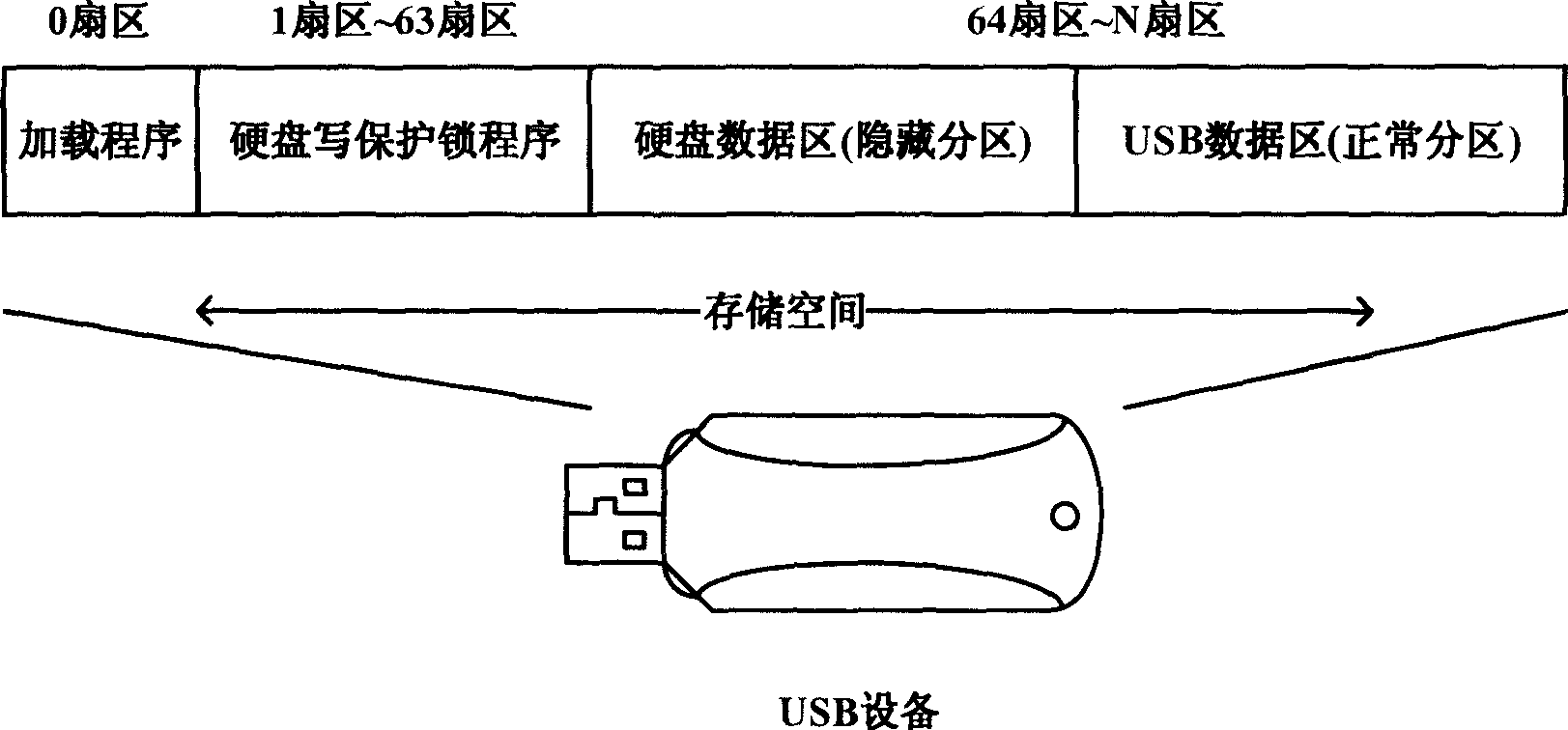
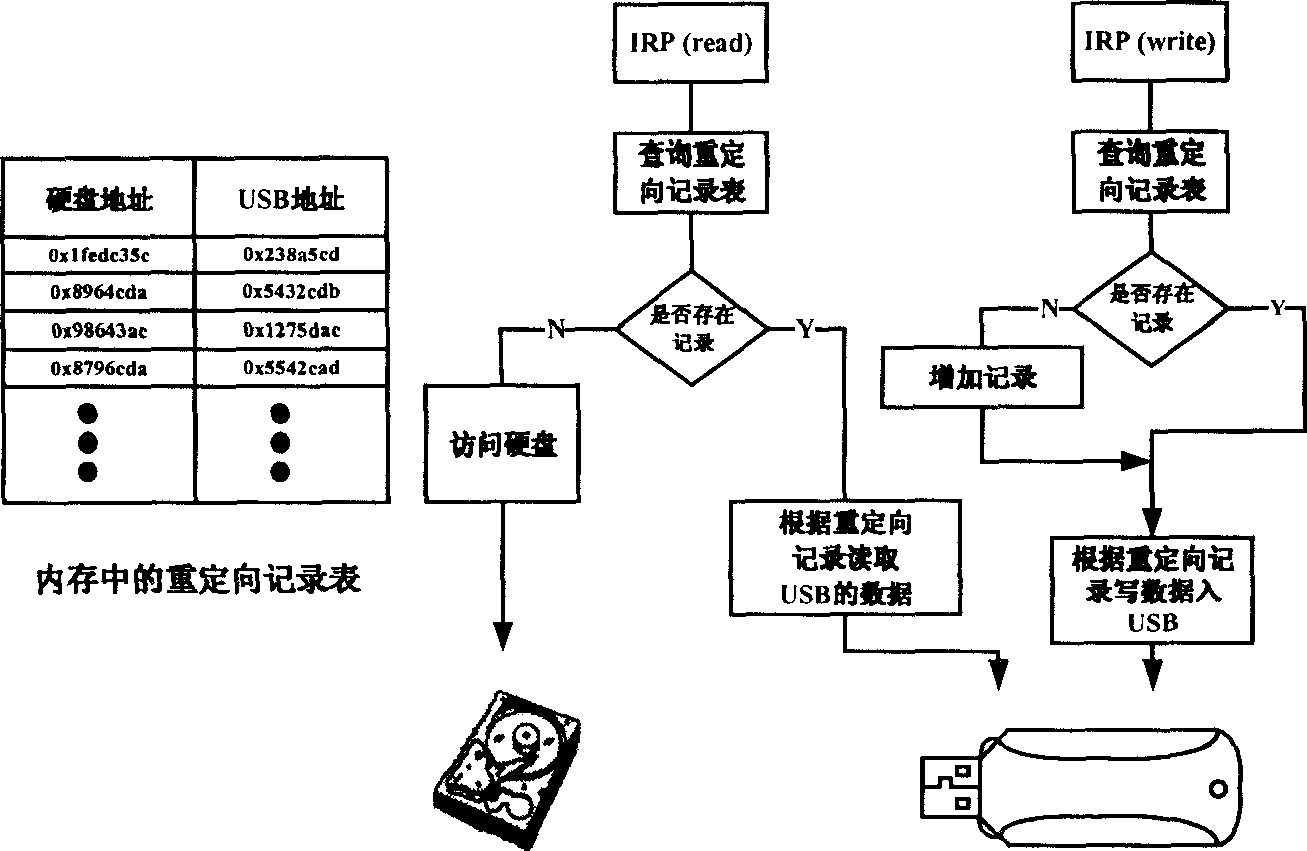
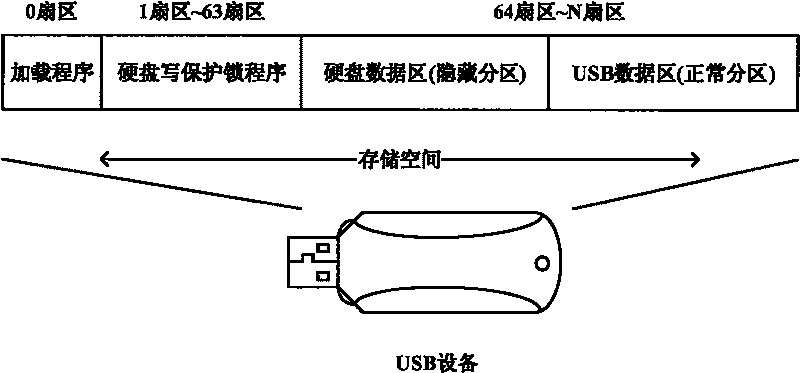
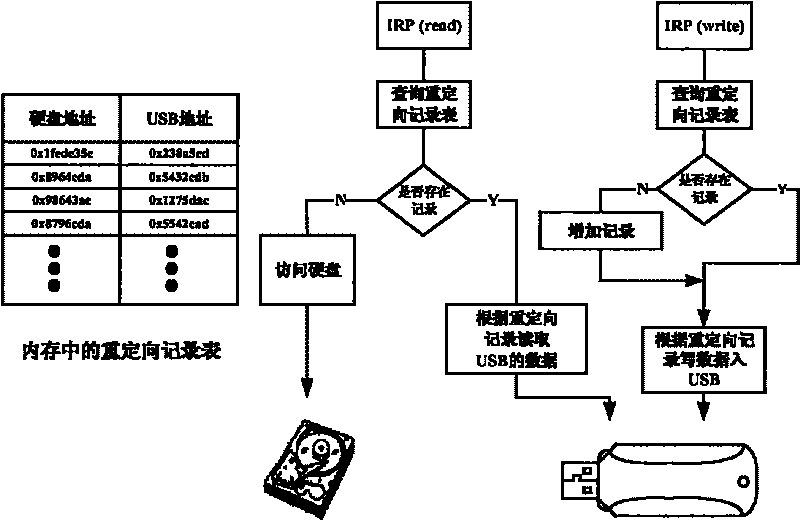
Hard disk write-protection lock based on USB equipment under Windows environment
InactiveCN101373457AInnovative designReduce use costUnauthorized memory use protectionInternal/peripheral component protectionWrite protectionOperational system
The invention relates to the field of computer forensics, in particular to a write protection lock for a hard disk in the Windows environment. The write protection lock comprises a USB unit, a loading program deposited in the sector 0 of the USB unit, a hard disk write-protection lock program deposited in the hidden sector of the USB unit. The loading program monitoring Windows operation system intermits the read-write of an objective hard disk through INT13H; when a computer is started up, the hard disk write protection lock program is embedded into the Windows operation system. The hard disk write-protection lock program monitoring Windows operation system reads and writes the objective hard disk through a drive program, and redirects write operation to the UBS unit, thereby preventing the data on the hard disk from being modified. The write protection lock is designed originally; no additional hardware units are needed between a computer motherboard and the hard disk. The service cost is low, and just one USB unit supporting the start-up from USB is needed; the use value is high; the write protection lock can be used as a running platform for computer crime forensics software.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
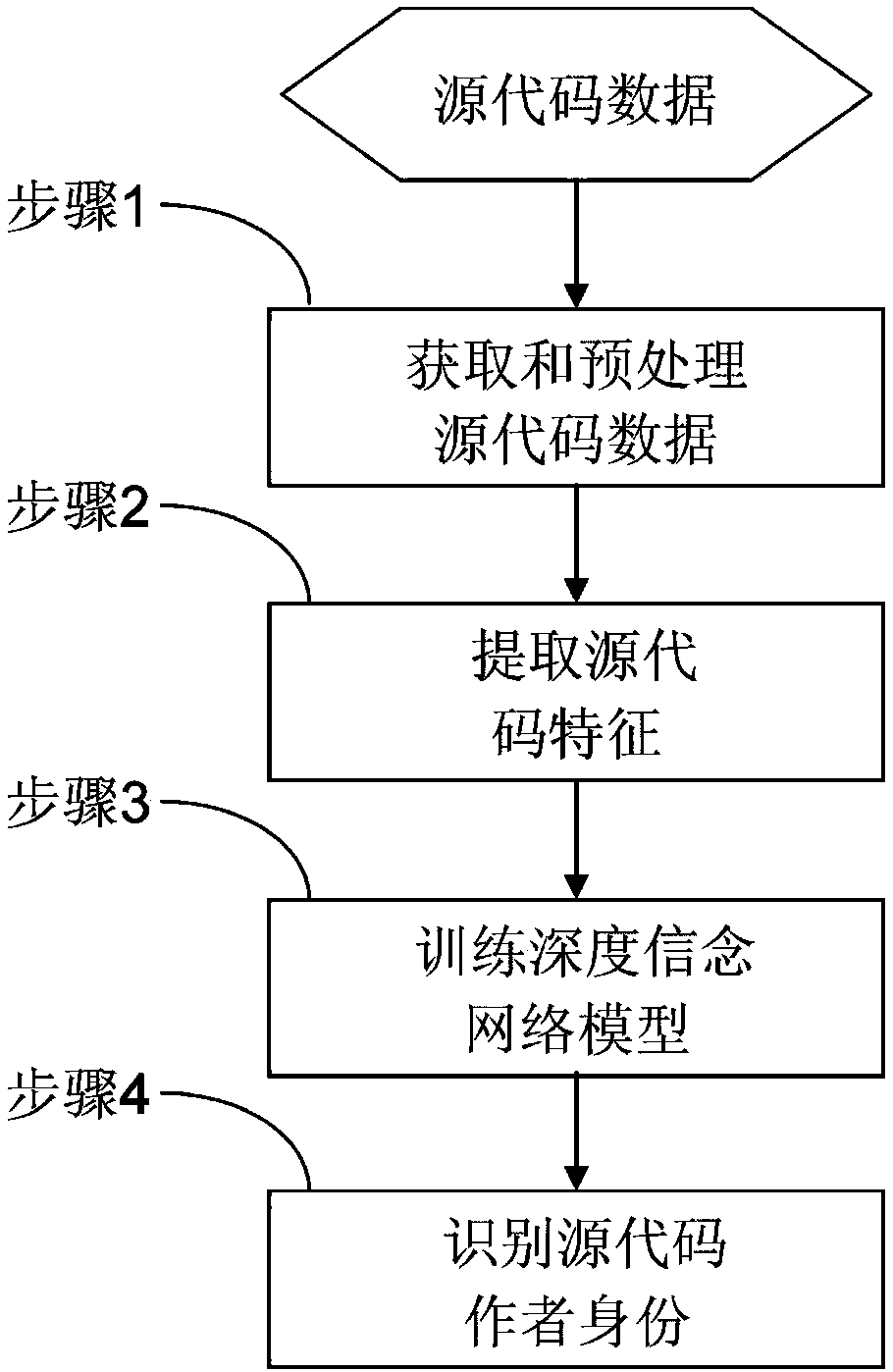
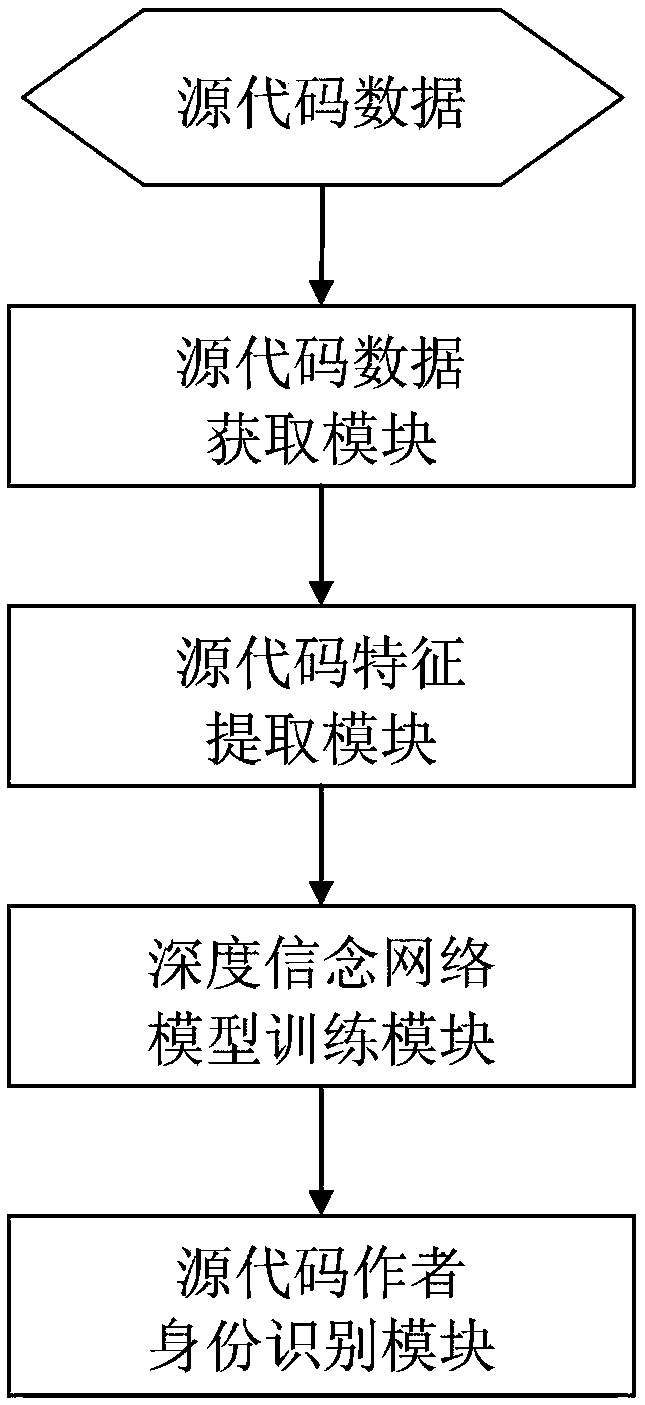
Source code author identification method based on deep belief network
ActiveCN108108184AImprove performanceReal-timeReverse engineeringMachine learningDeep belief networkSource code file
The invention discloses a source code author identification method based on a deep belief network, and belongs to the field of Web mining and information extraction. The method includes the followingsteps of constructing a source code data set, and preprocessing source code data; extracting source code features based on a continuous n-gram code segment model; training a deep belief network modelbased on a training source code file sample; using the trained deep belief network model to identify an author of an source code file, and outputting an author identification result of the source codefile. The method converts a source code author identification problem into a classification problem, and identifies the identity of the author of the source code through the deep belief network, so that the performance and efficiency of identification of author identity are improved, and the method has broad application prospects in the fields of information retrieval, information security, computer forensics and the like.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
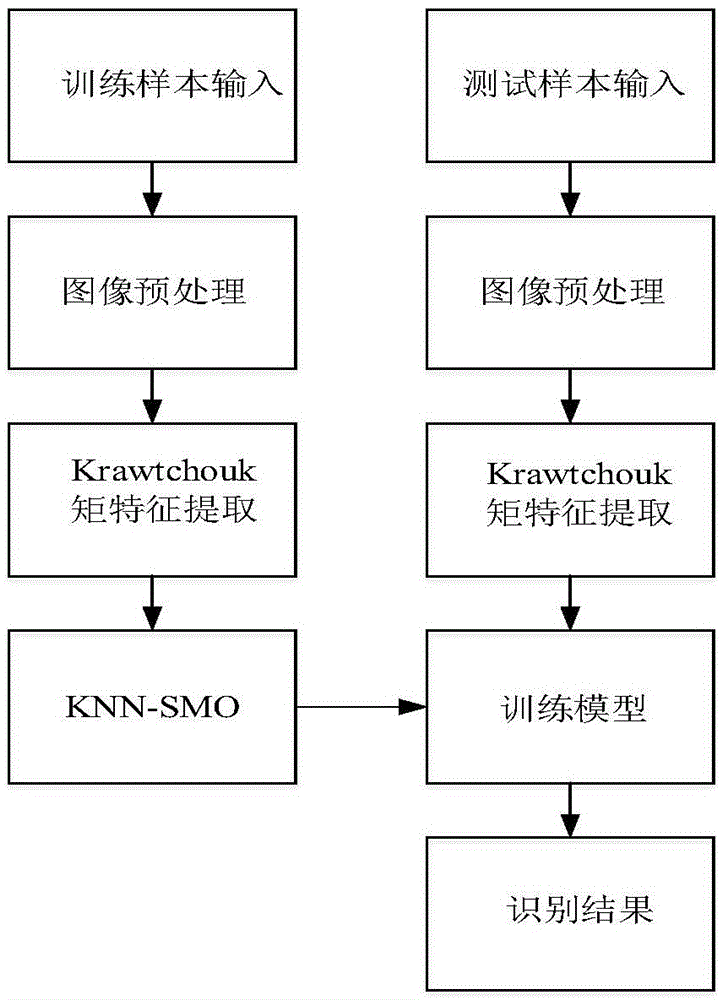
Secret level marking identification method based on Krawtchouk moment and KNN-SMO classifier
ActiveCN105512682AOvercome the shortcomings of being unable to carry out effective identificationImprove technical levelCharacter and pattern recognitionFeature vectorSmall sample
The invention relates to a secret level marking identification method based on a Krawtchouk moment and a KNN-SMO classifier. The method relates to a theory based on the Krawtchouk moment and the KNN-SMO classifier applied to the secret level marking identification of the computer forensics, and the method comprises the steps: a secret level marking image is performed the image preprocessing, the feature vector is formed by calculated Krawtchouk moments of the image, and the secret level marking image is performed the classification and identification by the KNN-SMO classifier. On one side, the low-stage Krawtchouk moment can be used to express the characteristic of the image well and has good stability under the common attack, on the other side, the KNN-SMO classifier is used, so that the classifier has KNN quick sorting capacity and SMO advantage of solving small sample problem, so that precision and speed of the secret level marking identification is improved.
Owner:深圳元物质科技集团有限公司
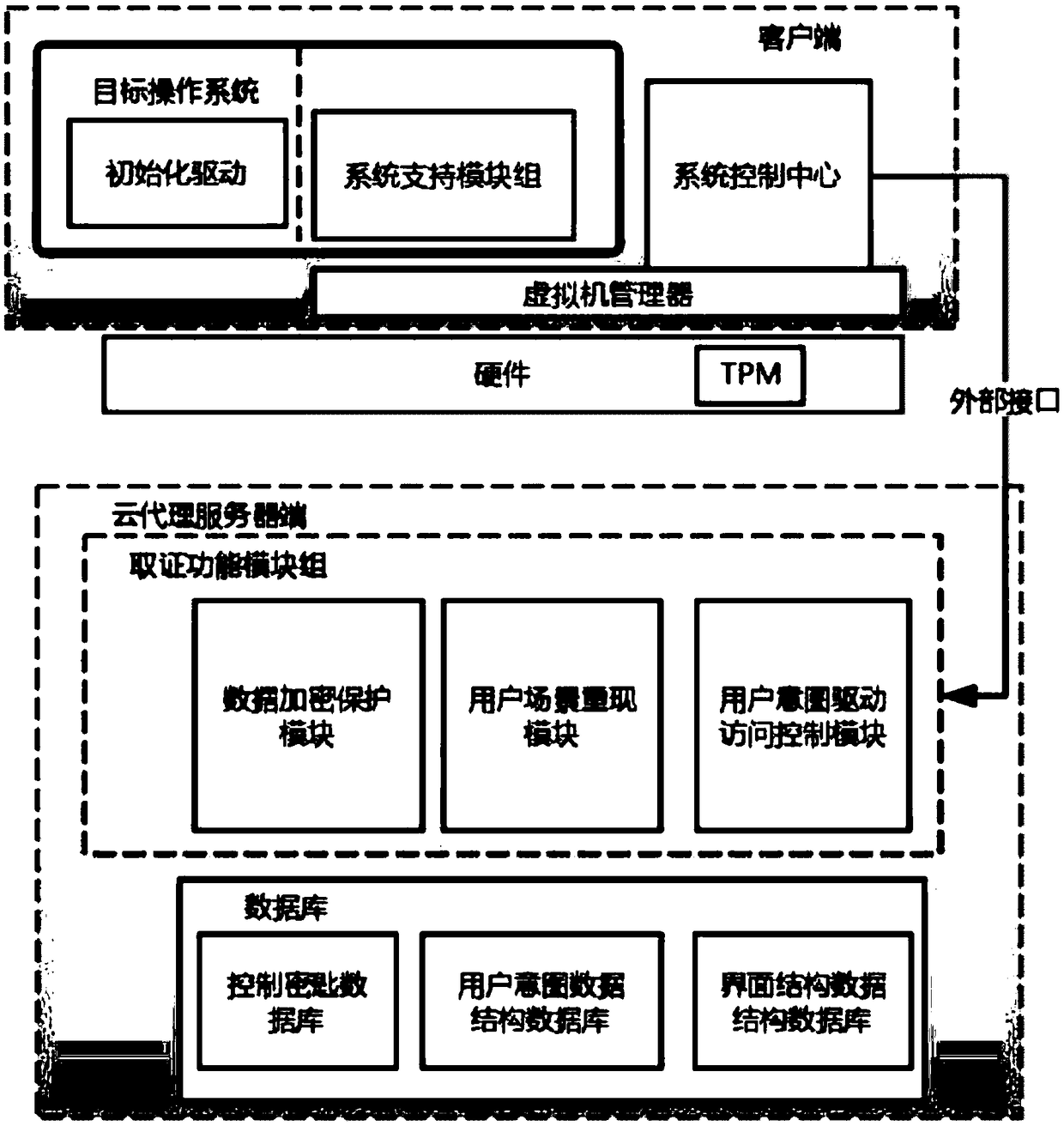
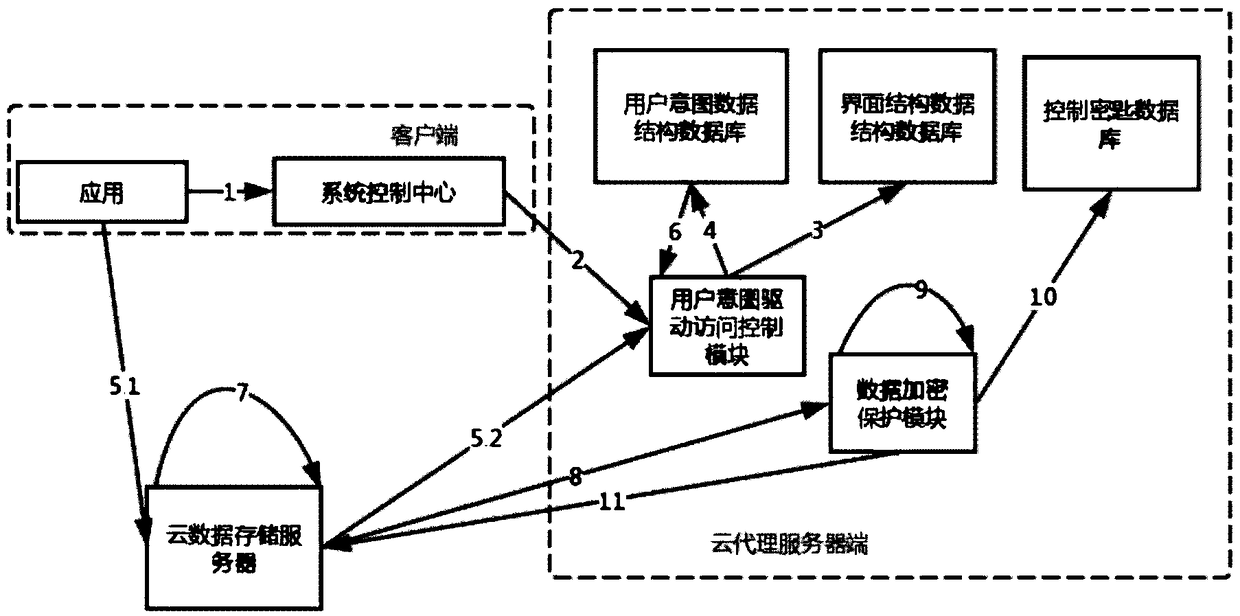
Forensics system and method based on user intention detection applied to cloud computing environment
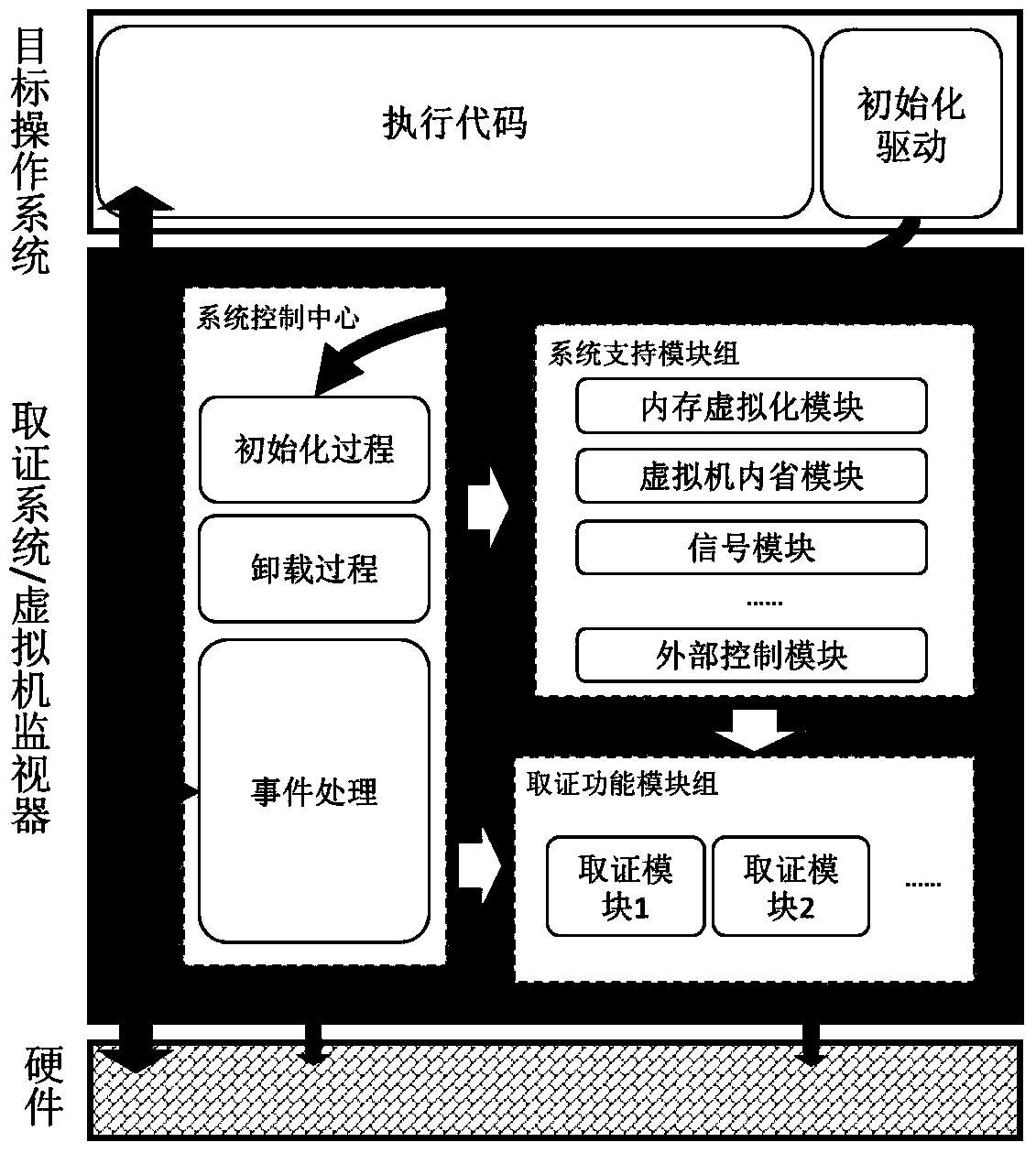
ActiveCN109254902AAvoid lossPrevent tamperingHardware monitoringDigital data protectionVirtualizationClient-side
The invention discloses a computer forensics system and a method thereof based on user intention detection applied to a cloud computing environment. The system comprises a client end and a cloud proxyserver end. The client end is provided with an initialization driving module, a system control center and a system support module group. The cloud proxy server is deployed with forensics function module group. The invention realizes a lightweight virtual machine monitor at the client end, The forensic tools can directly utilize the convenience and flexibility brought by the hardware virtualization technology, provide tools for rapid analysis and real-time evidence acquisition, and build a cloud proxy server between the client and the server, so that the server can directly use the functions of the forensic system without reconstructing the cloud system architecture. The method overcomes the shortcomings of current forensics after the event, overcomes the flexibility shortcomings of the virtualization technology itself, has a wider application scope than the traditional security system, and ensures the credibility and accuracy of evidence collection.
Owner:NANJING UNIV
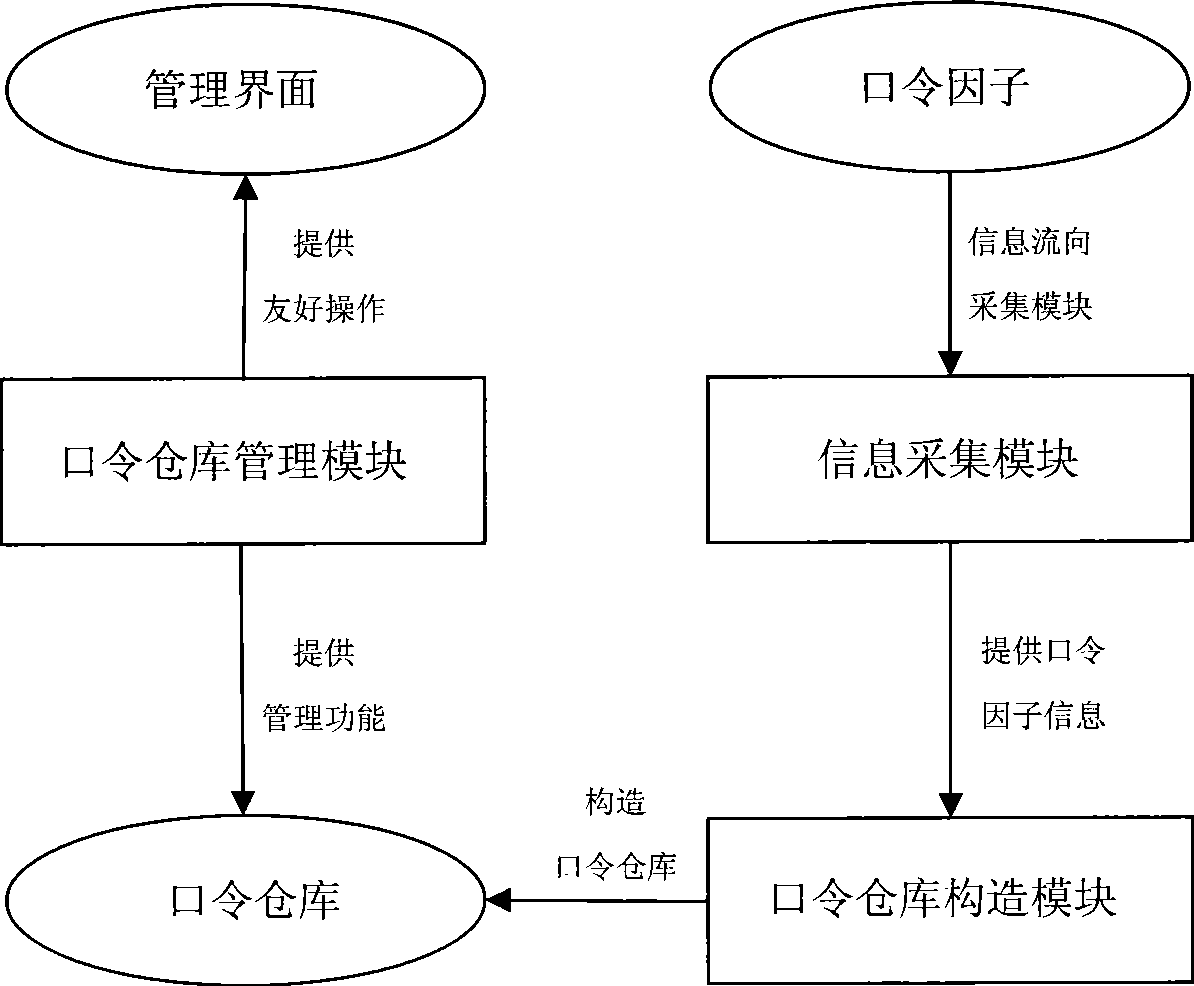
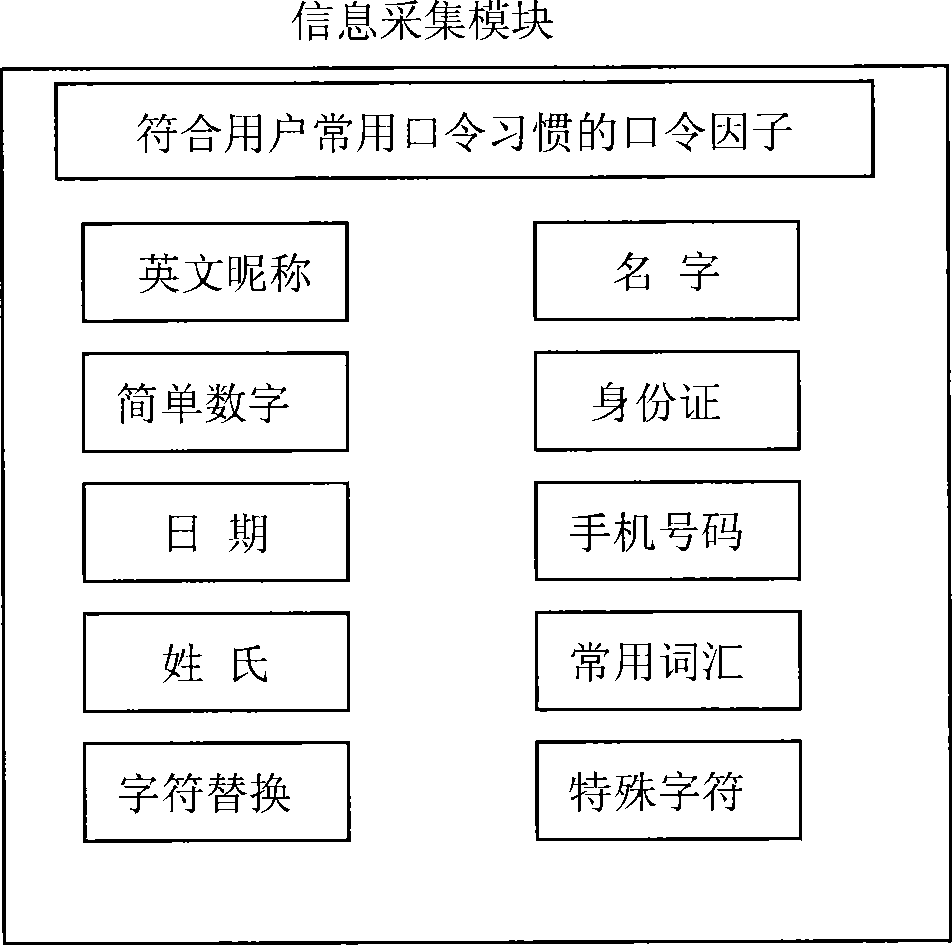
Password warehouse management system based on password characteristic
InactiveCN101533433AQuick searchImprove cracking efficiencyDigital data authenticationPasswordManagement system
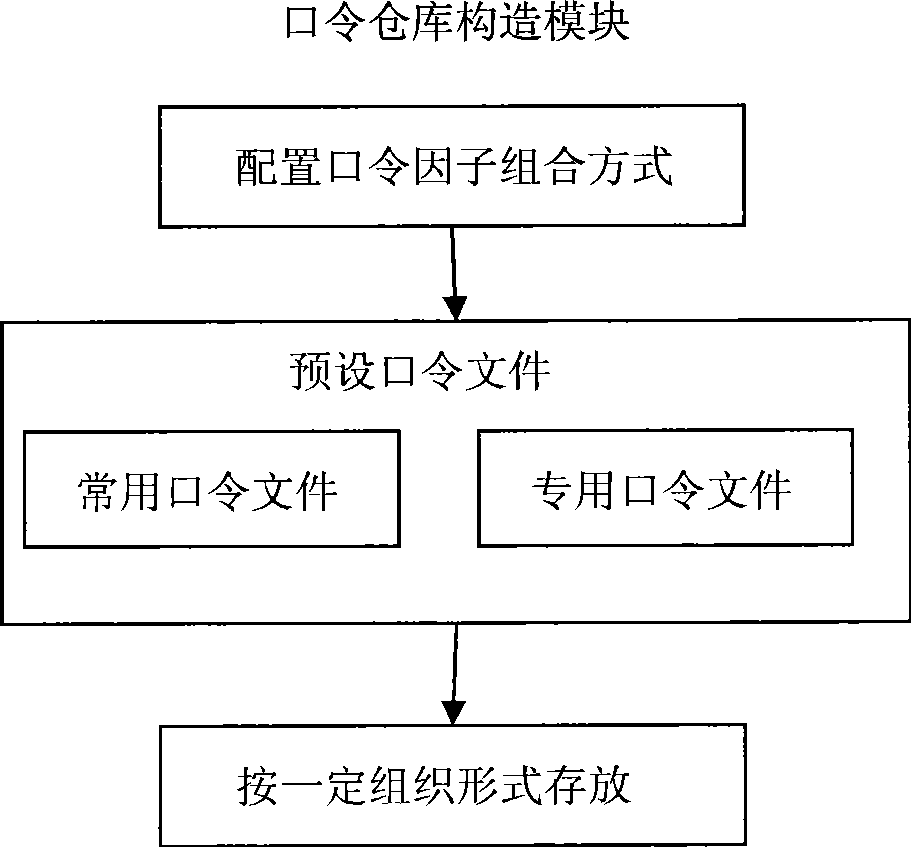
The invention relates to a password warehouse management system based on a password characteristic, belonging to the technical field of computer application. The system comprises an information acquisition module, a password warehouse structure module and a password warehouse management module; wherein, the information acquisition module acquires a password factor which is required by the password warehouse, the password warehouse structure module constructs a preset password document by the password factor which is provided by the information acquisition module and hierarchically and structurally memorizes a constructed preset password document, and the password warehouse management module provides management function to the constructed password warehouse. The preset password document is organizationally memorized according to password type, password organization and password length to form the password warehouse. The invention avoids exhaustive and unnecessary preset password documents, thereby obviously improving the decrypting efficiency of the encryptted key document in the process of computer forensics.
Owner:SHANGHAI JIAO TONG UNIV
Digital evidence integrality storage control system based on computer forensics
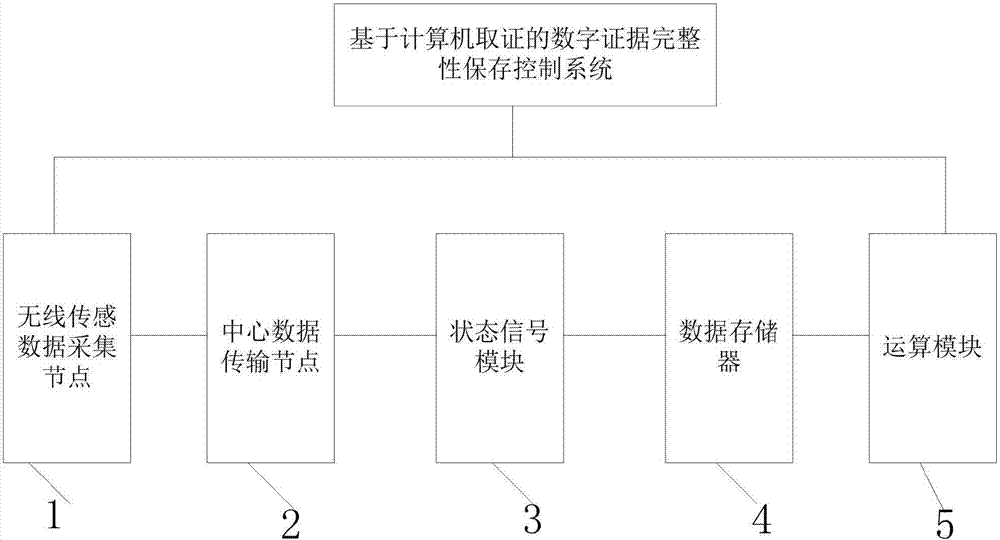
InactiveCN106921393AImprove reliabilityChange the calculation orderPulse conversionControl systemData acquisition
The invention belongs to the technical field of data processing, and discloses a digital evidence integrality storage control system based on computer forensics. The system comprises: wireless sensor data collection nodes, a central data transmission node, a state signal module, a read-write control module and an operation module. Data read from a data memory are processed according to a signal transmitted by the read-write control module. The data collection nodes in the digital evidence integrality storage control system disclosed by the invention performs self organization to form a regional storage network, the data on each data collection node are stored in the nodes of the system in an encoding manner, and when the storage space of the ad hoc storage network is insufficient, the system covers the historical data with the newly collected data according to a certain interval through a set data coverage rule; and the digital evidence integrality storage control system disclosed by the invention greatly improves the reliability of the data storage of the system. The digital evidence integrality storage control system disclosed by the invention has popularization and application values.
Owner:HUNAN CITY UNIV
Log-based computer evidence obtaining system
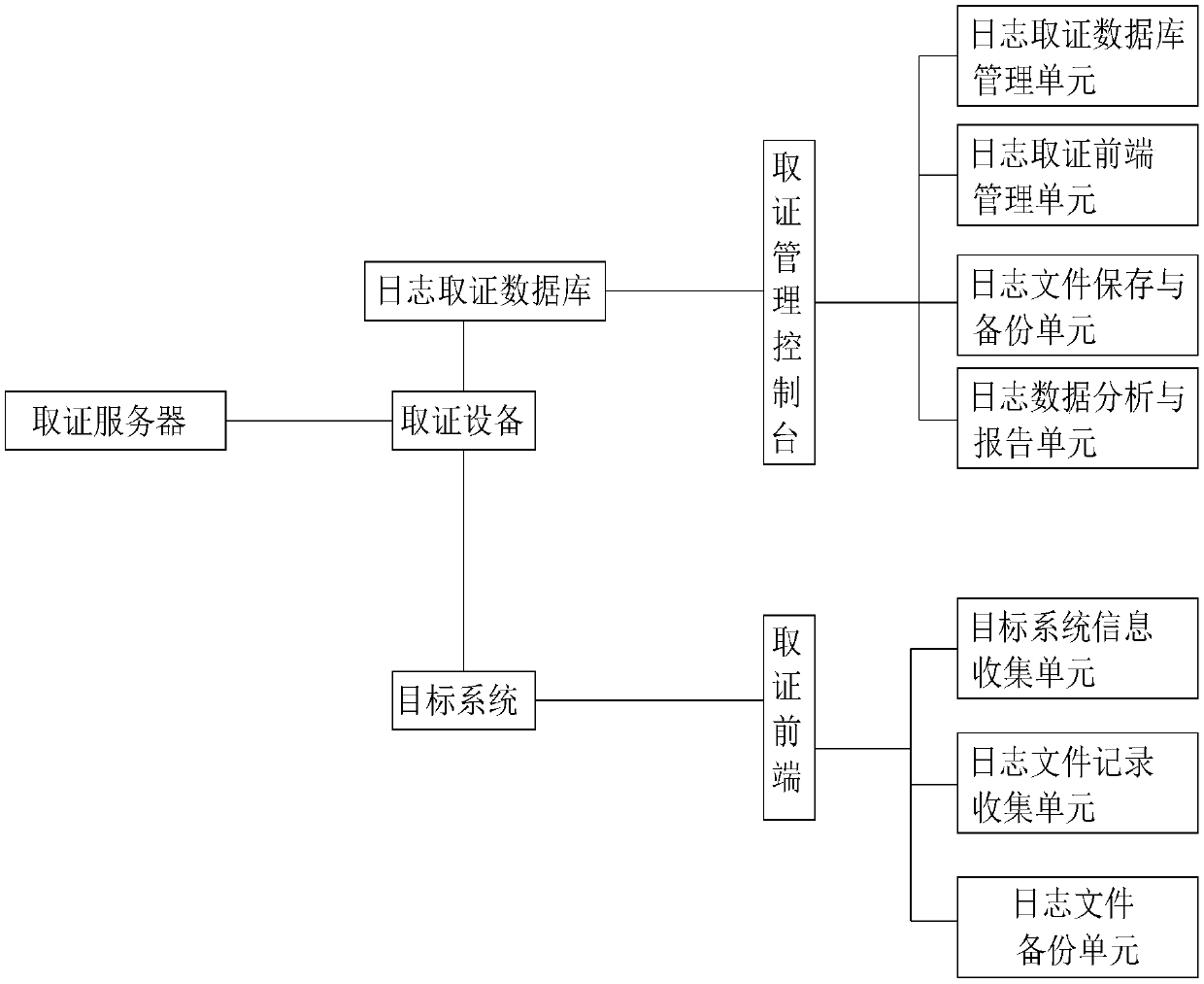
The invention relates to a log-based computer forensics system. The system comprises a forensics server, forensics equipment, a database, a forensics management console, a target system and a forensics front end, The evidence obtaining device is connected with the evidence obtaining server, the database, the evidence obtaining management console and the target system. The database is also connected with the evidence obtaining management console; Wherein the target system is connected with the forensics front end; The forensics management console comprises a database management unit, a log forensics front-end management unit, a log recording unit, a log file storage and backup unit and a log data analysis and reporting unit; According to the system, the log file library is established, formats and default storage positions of most of system logs can be identified, and help is provided for understanding and analyzing log data; Meanwhile, log data collected by various systems can be imported into a database, keyword query and correlation analysis of various logs are carried out, and reports are generated and printed.
Owner:成都纵海科技有限公司
A sqlite data recovery method suitable for merging non-integer primary keys and free blocks
ActiveCN106844607BMake up for the lack of analytical abilityImprove recovery rateRelational databasesSpecial data processing applicationsAlgorithmDatabase file
The invention provides an SQLite data recovery method applicable to merging of non-integral primary keys and free blocks and relates to the field of computer forensics. The method includes the steps of 1), starting from a root page and a file header to search all the free blocks and free pages; 2), analyzing difference of cell layout of integral primary keys and the non-integral primary keys as well as difference of meanings of bytes, temporarily assuming each free block contains one cell, calculating information of types covered, analyzing the type information and a data field and performing data recovery; 3), for the free blocks cannot pass the step 2), believing that each of the free blocks contains multiple cell, pre-estimating length of the cells stored in the free blocks is from 4 to free block length on the basis of splitting and verifying, and judging pre-estimated values with a single free block extraction module; 4), in response to decreasing of the free blocks due to B+tree reorganization, extracting the data from the free pages collected in the step 1). With the method, the data deleted can be easily recovered from SQLite3 database files, and the data is provided for follow-up electronic forensics work.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
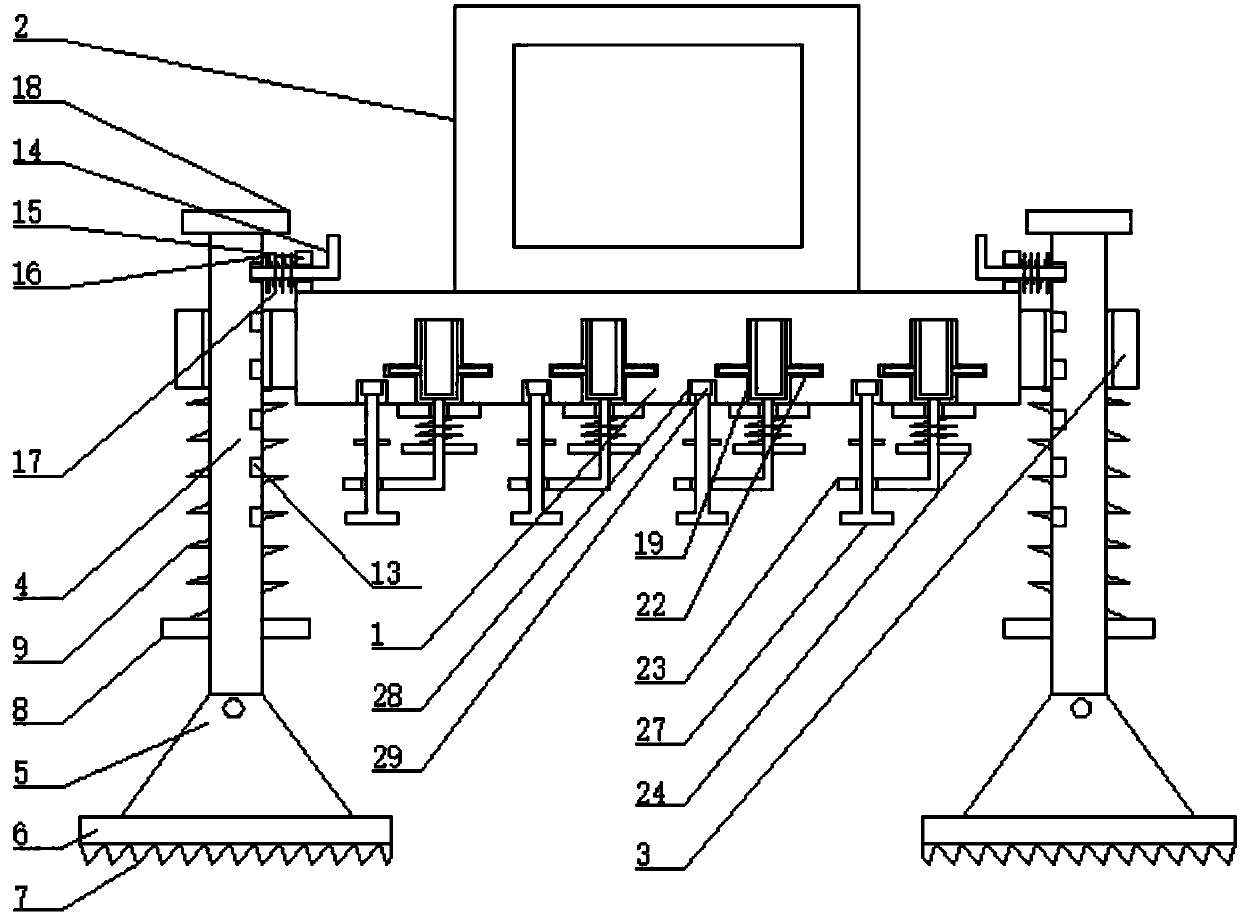
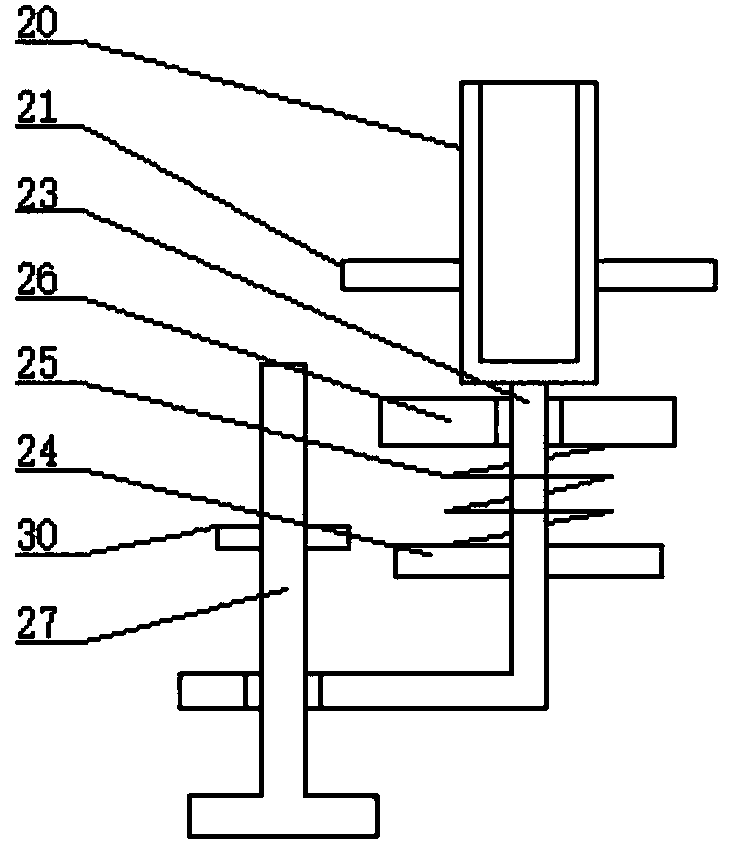
Computer forensics investigation apparatus
The invention discloses a computer forensic investigation equipment, which comprises a flat plate, the left and right ends of the flat plate are fixedly connected to the inner corresponding sides of the slip ring, the middle part of the slip ring is slidably installed with a sliding column, and the lower end of the sliding column passes through a rotating shaft Rotate and connect the upper side of the triangular plate, the lower end of the triangular plate is fixedly connected to the upper middle part of the grounding plate, the lower end of the grounding plate is provided with an anti-skid surface, and the upper end of the sliding column is fixedly connected to the lower end middle part of the limiting plate. The right-angle insert rod is inserted into the lock groove to stabilize the position of the slip ring, and then the device is placed on the uneven ground for use, and the small evidence is placed in the cylinder, which is inserted into the cylinder groove, and the clamping plate corresponds to the clamping Slot, rotate the right-angle turning lever, and the card board is stuck in the card slot, which is convenient for placing small documents on the device. After the lock lever is out of the socket, the card board comes out of the card slot, and the small evidence is taken out of the cylinder Use, and then it is convenient to use when looking for small documents next time.
Owner:成都安信思远信息技术有限公司
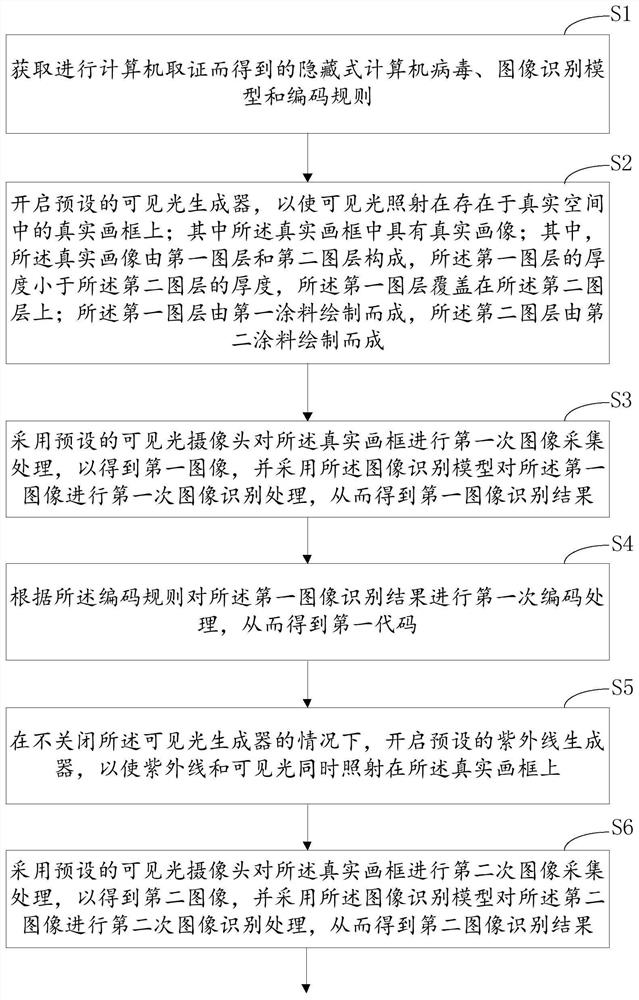
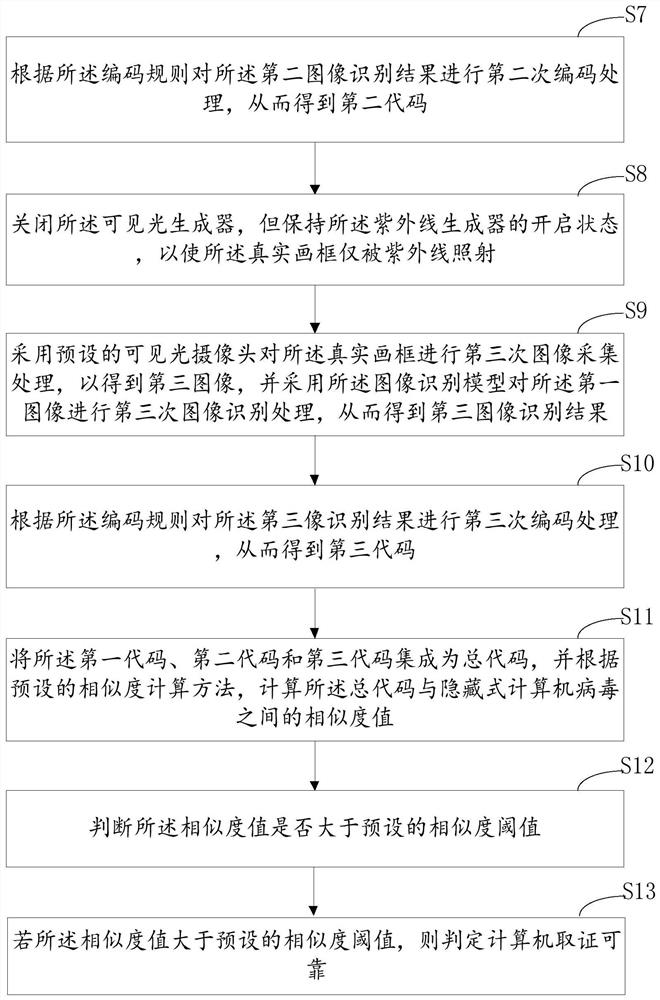
A reliability verification method, device and system based on computer forensics
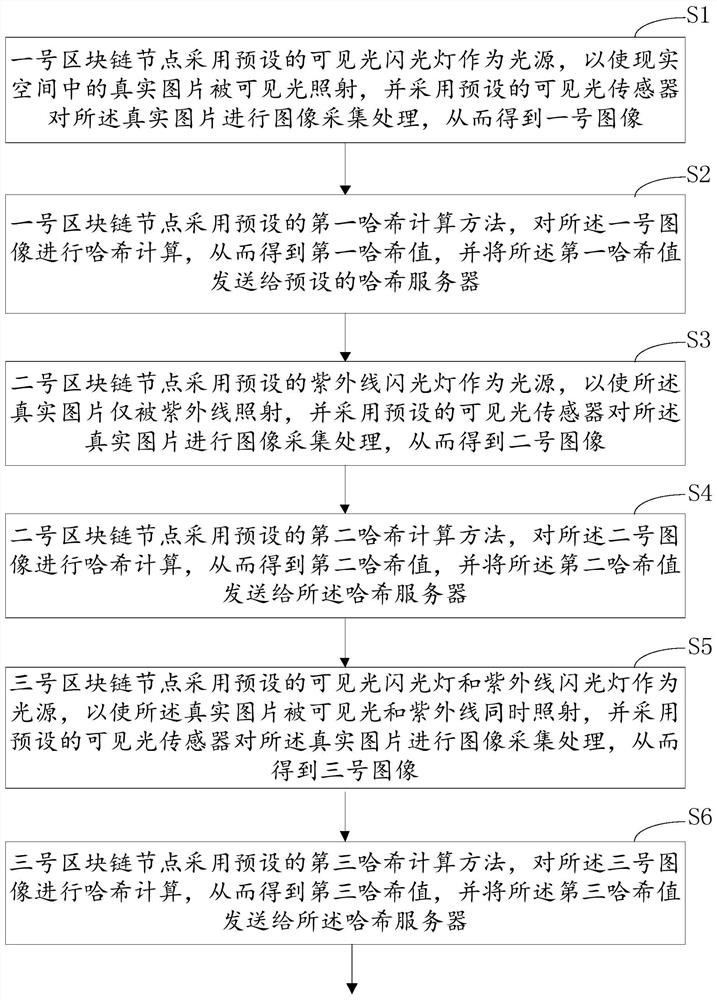
ActiveCN112668649BOvercoming flaws not applicable to hidden computer virusesReliable forensicsCharacter and pattern recognitionPlatform integrity maintainanceAlgorithmUltraviolet lights
This application discloses a reliability verification method, device and system for computer forensics, which obtains hidden computer viruses, image recognition models and coding rules; irradiates visible light on the real picture frame; conducts the first image collection and processing, and obtains the second One image, to obtain the first image recognition result; carry out the first encoding process to obtain the first code; irradiate the ultraviolet light and visible light on the real picture frame at the same time; carry out the second image acquisition process to obtain the second image, and obtain the second Image recognition result; obtain the second code; make the real picture frame only be irradiated by ultraviolet rays; perform the third image acquisition process to obtain the third image and obtain the third image recognition result; perform the third encoding process to obtain the third code; Integrate into the total code, and calculate the similarity value; if the similarity value is greater than the similarity threshold, it is determined that the computer forensics is reliable. Therefore, the reliability verification of forensics for hidden computer viruses is realized.
Owner:CHINA SOUTHERN POWER GRID COMPANY +1
Hard disk write-protection lock based on USB equipment under Windows environment
InactiveCN101373457BInnovative designReduce use costUnauthorized memory use protectionInternal/peripheral component protectionWrite protectionOperational system
The invention relates to the field of computer forensics, in particular to a write protection lock for a hard disk in the Windows environment. The write protection lock comprises a USB unit, a loadingprogram deposited in the sector 0 of the USB unit, a hard disk write-protection lock program deposited in the hidden sector of the USB unit. The loading program monitoring Windows operation system intermits the read-write of an objective hard disk through INT13H; when a computer is started up, the hard disk write protection lock program is embedded into the Windows operation system. The hard diskwrite-protection lock program monitoring Windows operation system reads and writes the objective hard disk through a drive program, and redirects write operation to the UBS unit, thereby preventing thedata on the hard disk from being modified. The write protection lock is designed originally; no additional hardware units are needed between a computer motherboard and the hard disk. The service cost is low, and just one USB unit supporting the start-up from USB is needed; the use value is high; the write protection lock can be used as a running platform for computer crime forensics software.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
A method for extracting text data files in physical memory mirroring
ActiveCN102945288BAccurately getSpecial data processing applicationsData ingestionOperational system
The invention discloses a method for extracting a text data file from a physical memory image. The method comprises the following steps of: searching an eprocess structure of a notepad.exe progress by utilizing characteristic values of the eprocess structure and offset between the characteristic values, and acquiring a page directory base address of the progress; and acquiring text data description information and labeling information in memory, and accurately acquiring the text data in the notepad.exe progress through the principle of converting the address of an operating system. The method can be used for data recovery, data extraction, computer forensic and the like.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
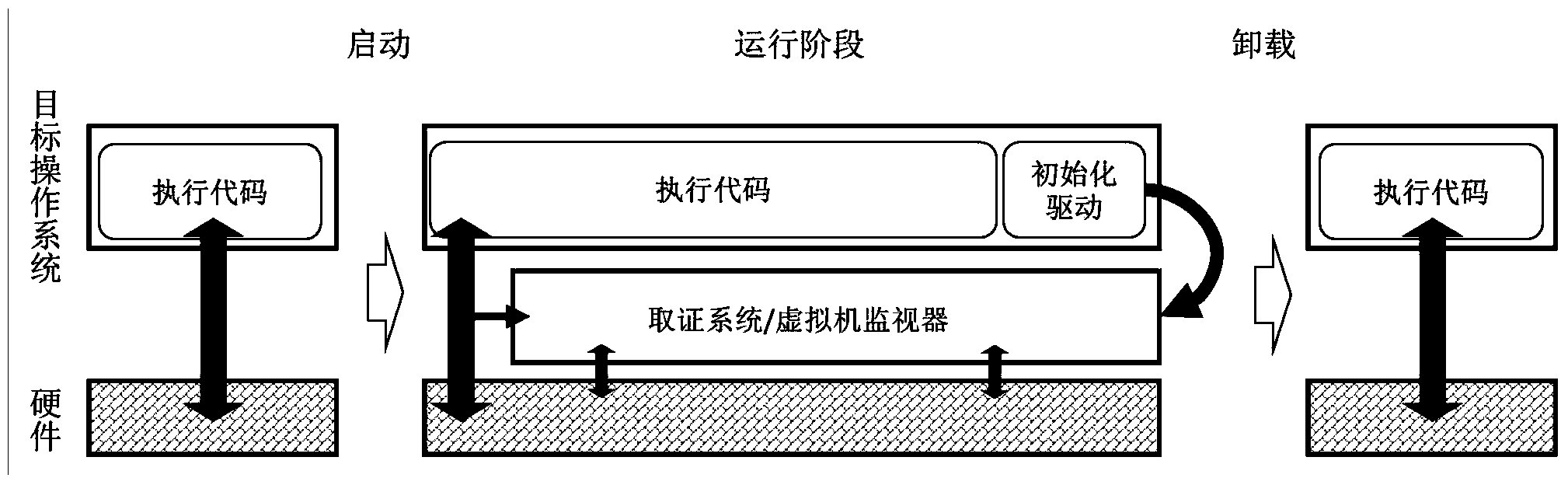
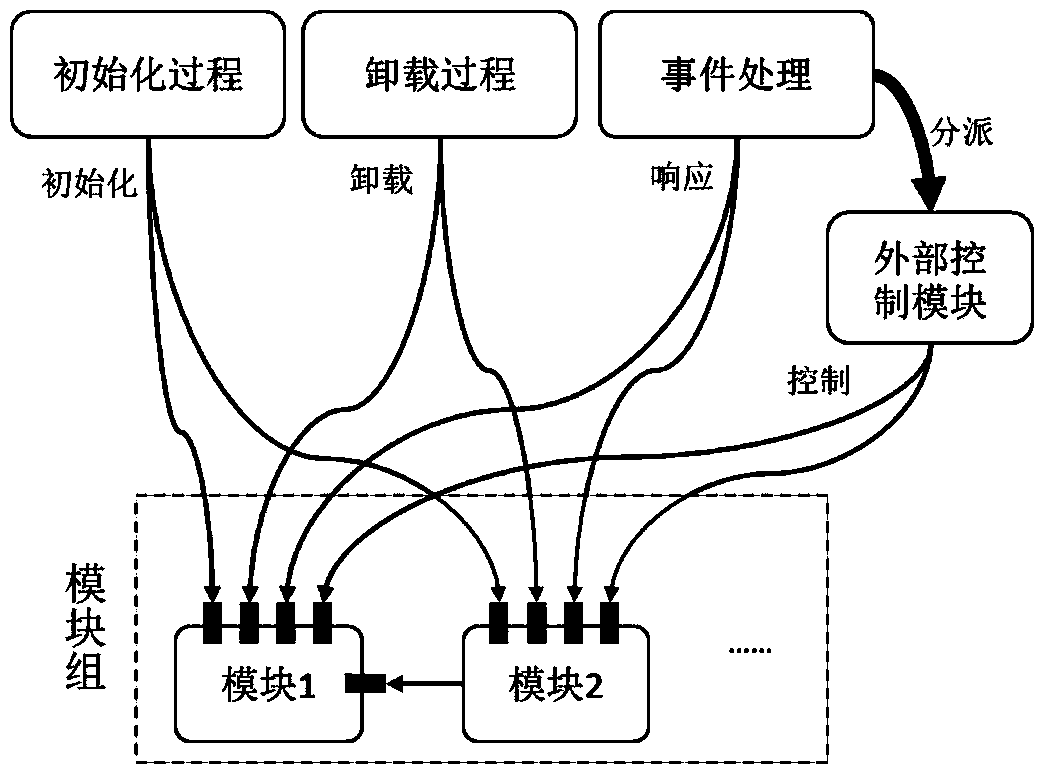
Modular computer forensic system and method based on hardware virtualization
InactiveCN104021063BAvoid lossPrevent tamperingHardware monitoringSoftware simulation/interpretation/emulationCore functionMultiplexing
The invention discloses a modular computer forensic system and method based on hardware virtualization. The modular computer forensic system comprises an initialization drive, a system control center, a system support module set and a forensic function module set. The method is based on the hardware virtualization technology, a light virtual machine is set up through the initialization drive when an operation system operates, the system control center supports a hardware virtual platform and manages all sub modules, and the system support module set supports all basic functions of the forensic module set. According to the method, interfaces of the forensic function module set are standardized, multiplexing and extension of the modules are supported, and forensic tools can focus on the core function, and a large amount of repetitive work is reduced; no codes of the target operation system need to be modified, performance losses are low, memory usage is less, a safe and credible real-time forensic foundation platform is set up, and convenience is brought to acquisition of the various forensic tools based on virtualization.
Owner:NANJING UNIV
System and method for selectively collecting computer forensic data using DNS messages
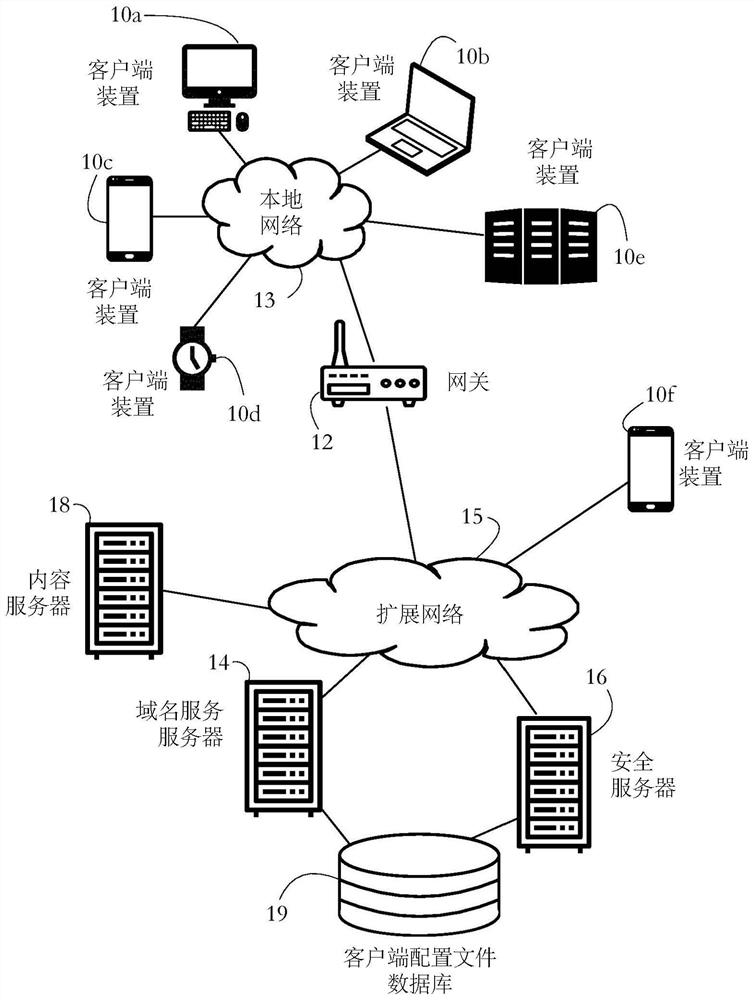
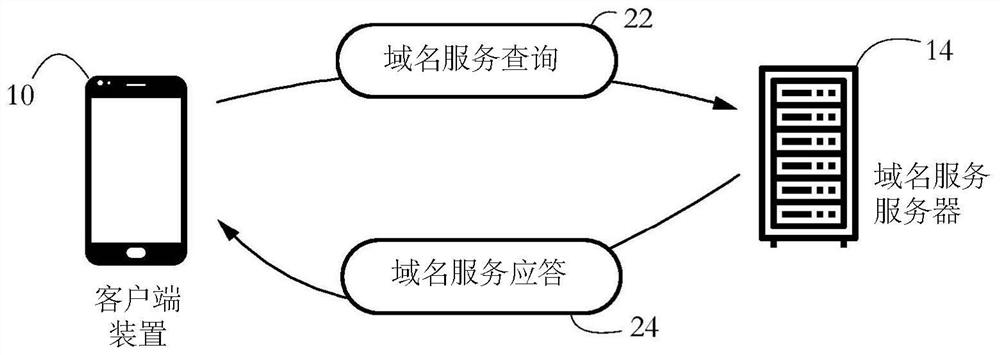
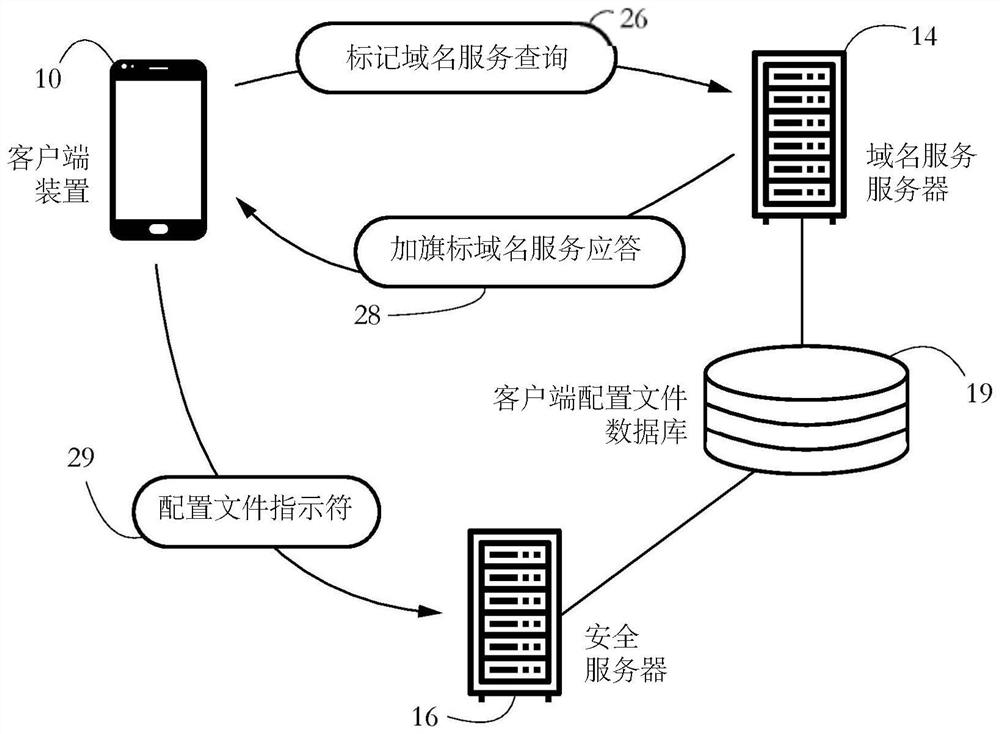
PendingCN114145004AEasy to understandData switching networksSecurity arrangementInternet privacyEngineering
The described systems and methods allow for selective collection of computer security data from client devices, such as personal computers, smartphones, and Internet of Things (IoT) devices. A security application executing on each client device includes a domain name service (DNS) agent that marks outgoing DNS messages with a client ID. The DNS server selects a client for data collection by returning a DNS response including a service activation flag. Some embodiments thus enable per DNS message selectivity for data collection. In some embodiments, subsequent network access requests made by the selected client are rerouted to a secure server for analysis.
Owner:BITDEFENDER IPR MANAGEMENT
A data evidence tamper-proof method, device and system based on computer forensics
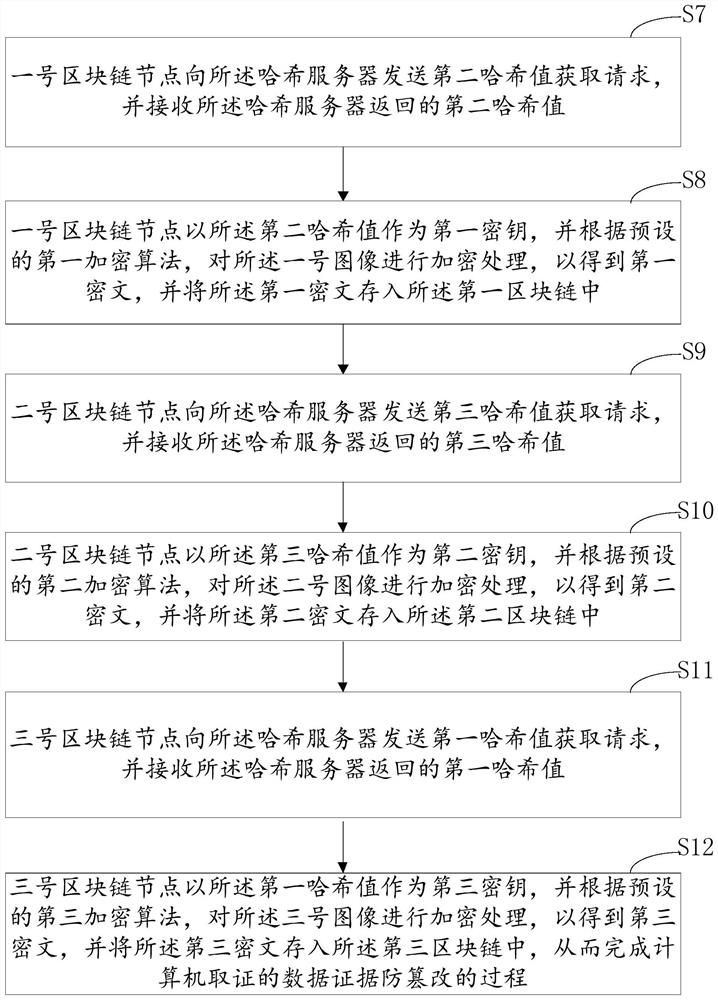
ActiveCN112434344BEnsure data securityReduce the possibility of tamperingDigital data protectionPlatform integrity maintainanceComputer hardwareAlgorithm
This application discloses a method, device and system for anti-tampering of data evidence based on computer forensics, including: No. 1 blockchain node uses a visible light flash as a light source to collect and process images to obtain No. 1 image; perform hash calculation to obtain The first hash value; the second block chain node uses ultraviolet flashlight as the light source, and performs image acquisition and processing to obtain the second image; performs hash calculation to obtain the second hash value; the third block chain node uses visible light flashlight and The ultraviolet flash lamp is used as a light source to perform image acquisition and processing to obtain the No. 3 image; perform hash calculation to obtain the third hash value; the No. 1 block chain node obtains the first ciphertext and stores it in the first block chain; The No. 2 block chain node obtains the second ciphertext and stores it in the second block chain; the No. 3 block chain node obtains the third ciphertext and stores it in the third block chain. In this way, the data security of computer forensics is guaranteed, and the possibility of being tampered with is reduced.
Owner:CHINA SOUTHERN POWER GRID COMPANY +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com